CLDAP is Now the No.3 Reflection Amplified DDoS Attack Vector, Surpassing SSDP and CharGen
Author: Xu Yang,kenshin
With our DDoSMon, we are able to perform continuous and near real-time monitoring on global DDoS attacks. For quite a long time, DNS, NTP, CharGen and SSDP have been the most frequently abused services in DDoS reflection amplification attacks. They rank respectively 1st, 2nd, 3rd and 4th in the last 365 days.
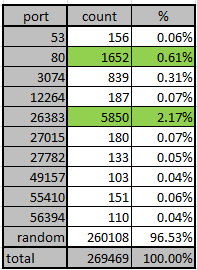
Recently, we noticed that CLDAP-based reflection amplification attacks (hereinafter referred to as CLDAP attack) have surpassed SSDP and CharGEN as the third biggest reflective DDoS attack vector. The figures below display the percentage of CLDAP attacks in the last 365 and 90 days among all reflective amplification DDoS attacks:
(Source: DDoSMon. The Insight web page on this site covers most of the data in this blog.)
CLDAP attack first appeared in the end of October last year, just a year ago. In this blog, we look at the rise of the CLDAP attack:
- Over the last 365 days, we have observed a total of 304,146 CLDAP reflection amplification attacks involving 215,229 unique IPs.
- In the last three months, CLDAP attack has entered into a new stage, the number of CLDAP attacks in the last three months has reached to 168k (11.2%), slightly more than CharGen attack(164k, 11%), and much more than SSDP attack (70k, 4.4%).
Our DRDoS data feed at our OpenData page maintain a list of top reflector IPs being used in the last 30 days, security researchers can contact netlab@360.cn to apply for free feed download.
Stages of Attack Evolution
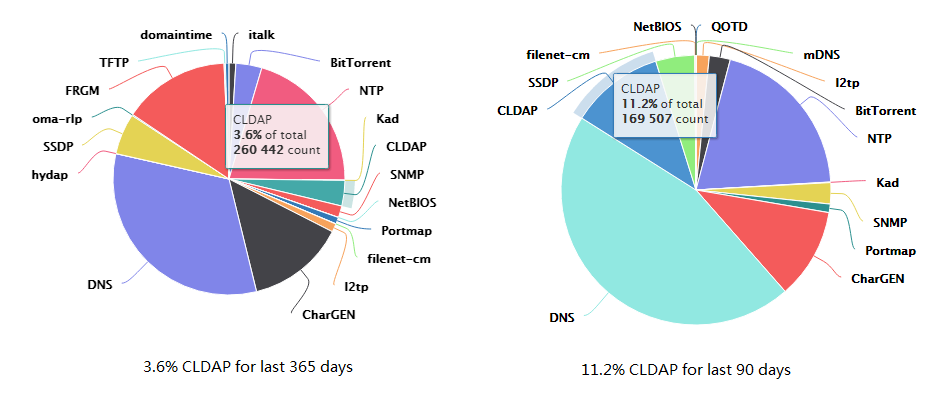
The above figure shows last years’ weekly counts of CLDAP reflection attack.
We can divide CLDAP attack activity into three stages:
- Initial stage: 2016-10 ~ 2017-04, about 1000 attacks per week on average
- The first climbing stage: 2017-04 ~ 2017-08, about 6000 attacks per week on average
- The second climbing stage: 2017-08 ~ now, about 15000 attacks per week on average
From the above statistics, you can see that CLDAP has become one of the workhorses in DDoS attack.
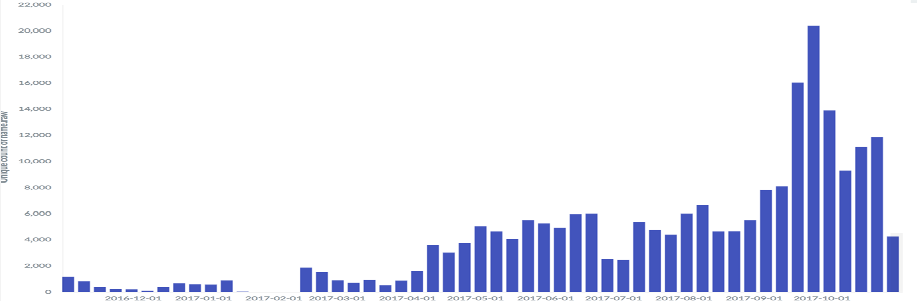
We also extracted all the LDAP reflector IPs that had been used in ddos attacks, did a month to month comparison, and generated the following diagram.
From the diagram, you can tell that the overlap rate of CLDAP ips has been going up and getting stable at around 40%.
Attack Vectors
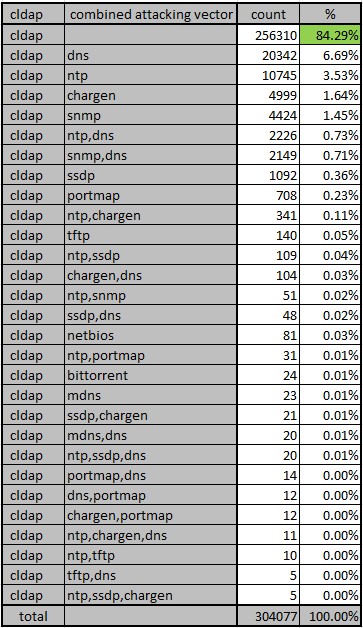
In all attacks involving CLDAP, over 84% are CLDAP only, with no other combined attacking vector. There are also some other combinations, which be seen as below.
Attacking Duration
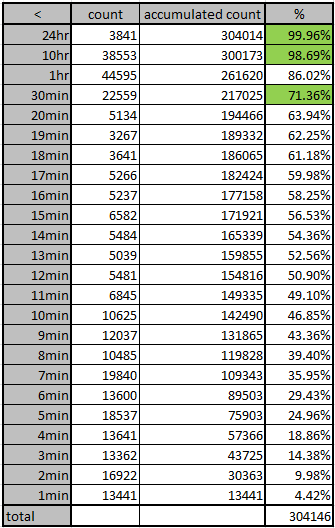
The duration of CLDAP attack varies: the shortest attack was less than 1 minute, and the longest one lasted more than 3 days. As shown in the figure below, the attack time span at 1, 2 and 3 standard deviations (68%, 95%, 99.7%) are respectively 30 minutes, 10 hours and 24 hours.
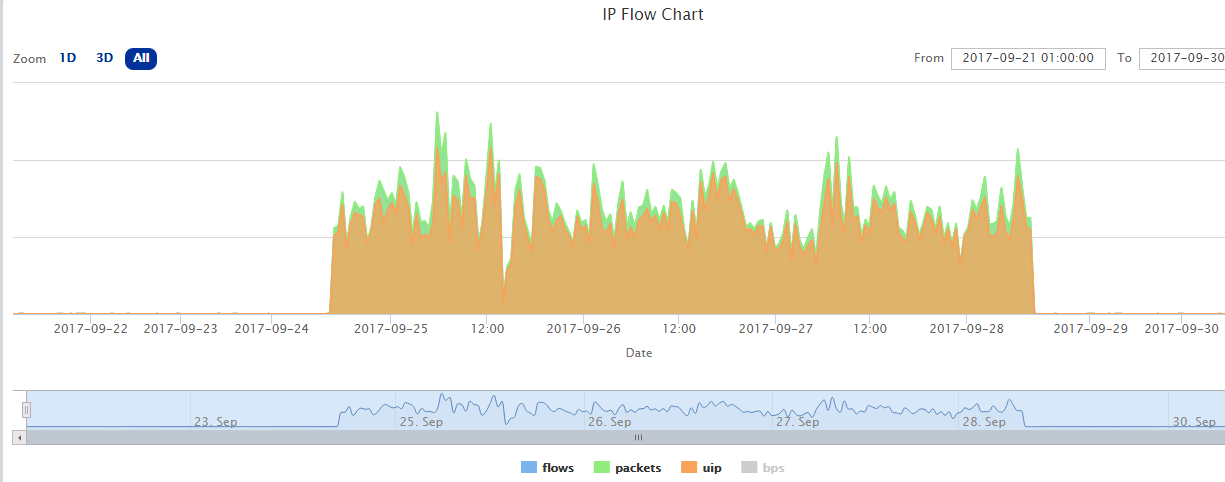
The 3-days attack mentioned above occurred from 2017-09-24 15:00:00 to 2017-09-28 09:00:00. The victim IP address, 151...15 belongs to a CDN service provider.
Destination Ports
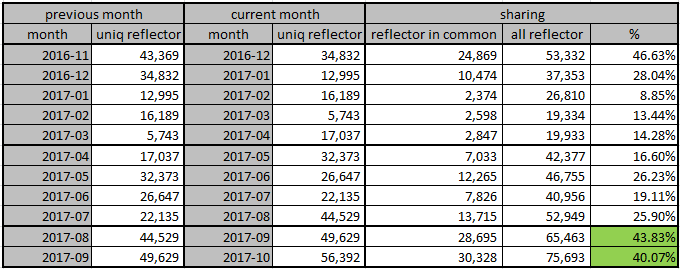
The distribution of the victim's destination port is shown in the following table:
- In most cases(96.5%) of CLDAP attack, the destination ports are randomized. This is consistent with other reflection amplified DDoS attacks.
- Note port 26383 stands out, which is not a commonly used service port, we suspect a particular CLDAP attack toolkit gets reused all the time by different attackers, or maybe there is big CLDAP attack provider somewhere.