A quick stats on the 608,083 Mirai IPs that hit our honeypots in the past 2.5 months
Over the last few weeks Mirai, a DDoS botnet family which is believed to be responsible for the large attacks against Brian Krebs on September 13, 2016, has become a hot topic in security community. Previous investigations show that this malware mainly infects IoT devices, e.g., CCTV, and TCP ports of 23 and 2323, which are used for Telnet, are the main infection vector.
On September 30, Mirai’s source code was leaked, which gives us the chance to better understand how this family of botnet works. After a some exploration on the leaked source, a vulnerability was found in its scan module, which, together with the fact that Mirai only scans TCP ports of 23 and 2323, enables us to distinguish the Mira TCP SYN scans from other scanners by checking the SYN packet's header fields. The evaluation on our old dataset shows 608,083 uinique Mirai IPs have hit our honeypots since August 1, 2016. In this post, I will give a quick statistics on the checked Mira scans.
The first Mirai scan that came to us was on 2016-08-01 12:46:01 UTC+8, August 1, 2016. Till 23:59:59 UTC+8, October 13, 2016, totally 1,063,786 Mirai scans were checked. The daily stats can be shown in Figure 1.
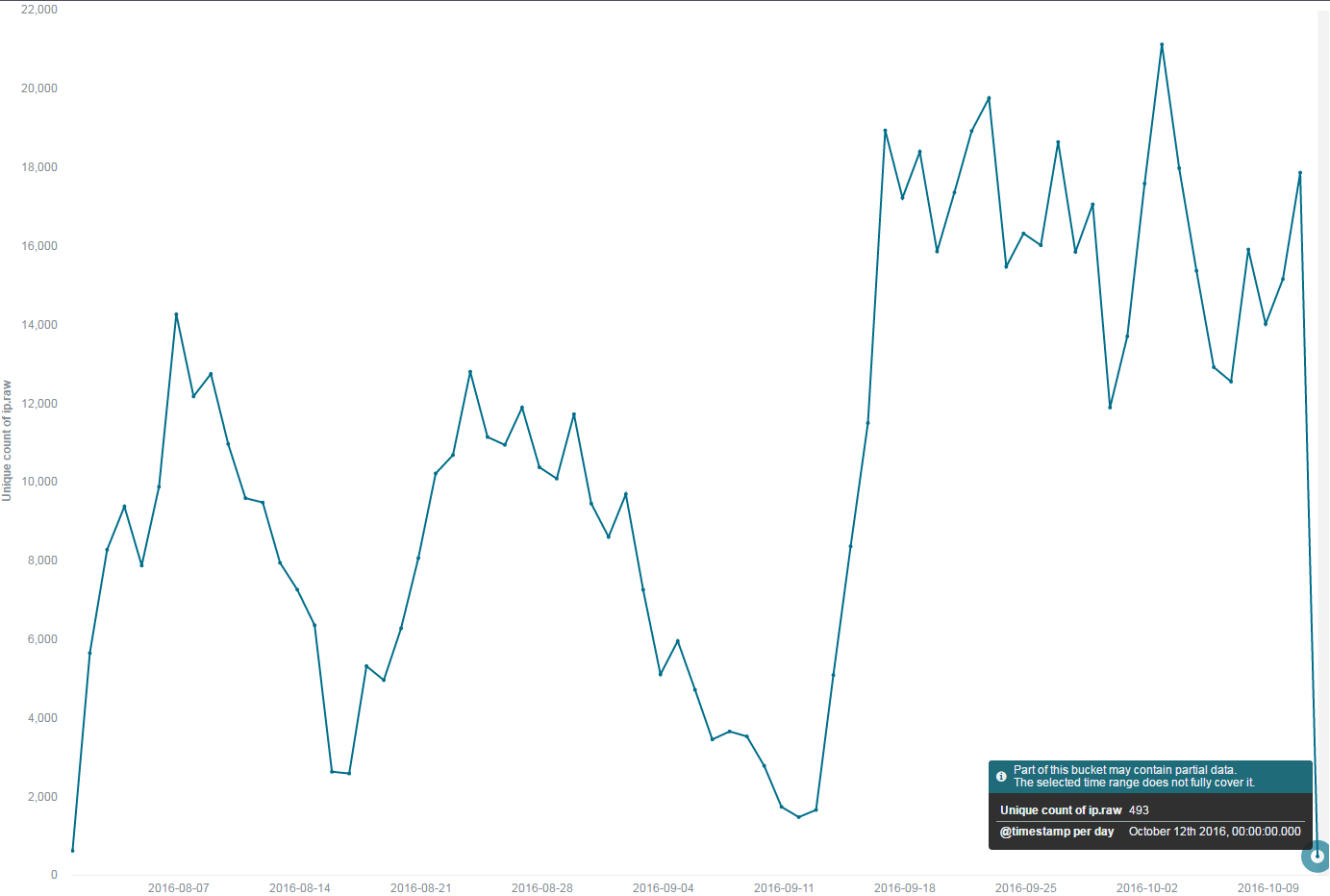
Figure 1, Daily variations of Mirai scans
It seems that after a few fluctuations the Mirai botnets reached a plateau in mid-September and have remained that activeness status till now.
Further investigations show that those scans came from totally 608,083 unique IPs across 196 countries, as shown in Figure 2.
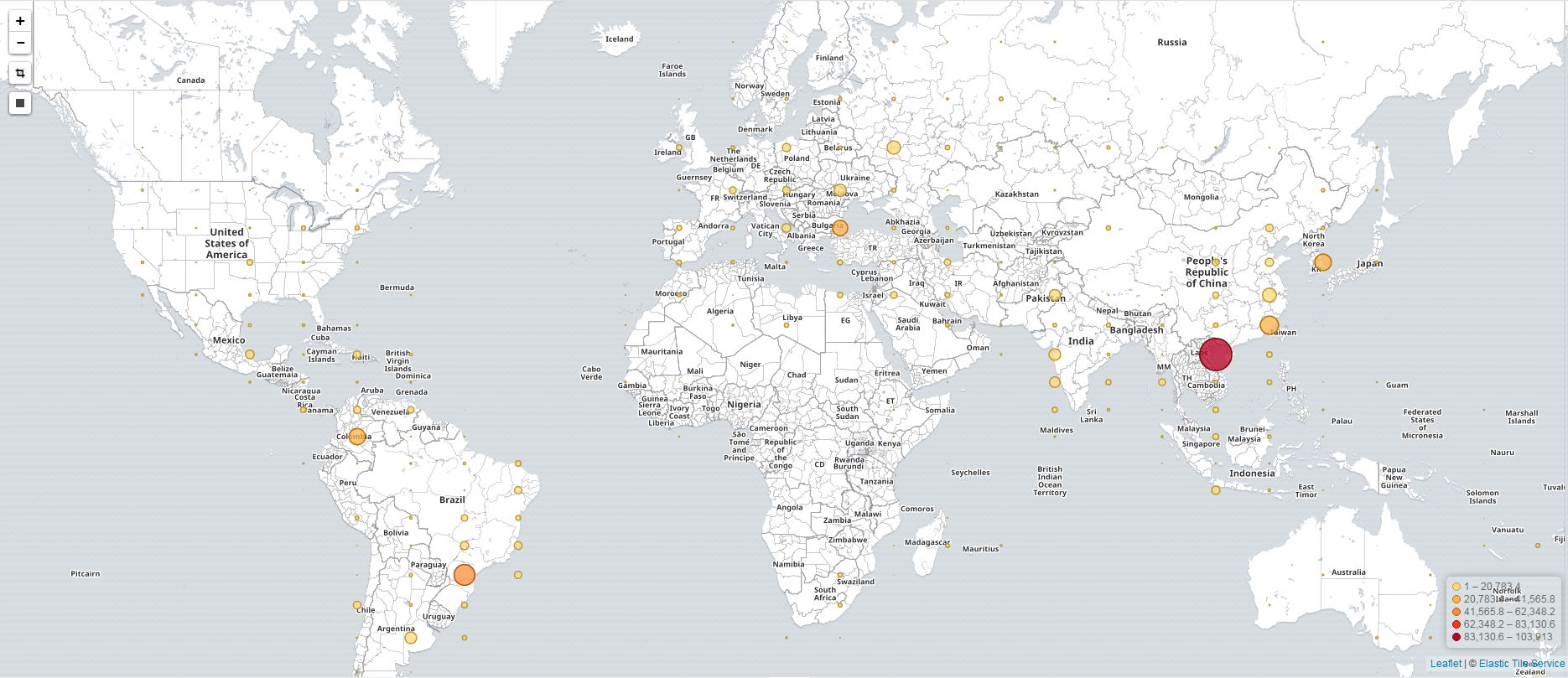
Figure2, Geo-locations of Mirai IPs
The top 10 countries/ASNs stats show that some Asian countries, including Vietnam, China, India, and Korea, have the largest number of Mirai bots.
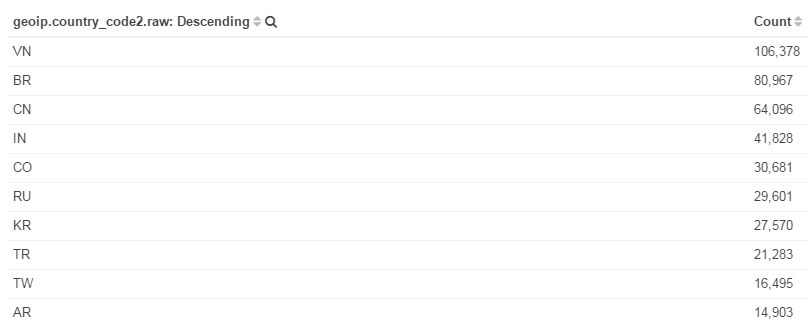
Figure 3, Top 10 countries of Mirai bot IPs
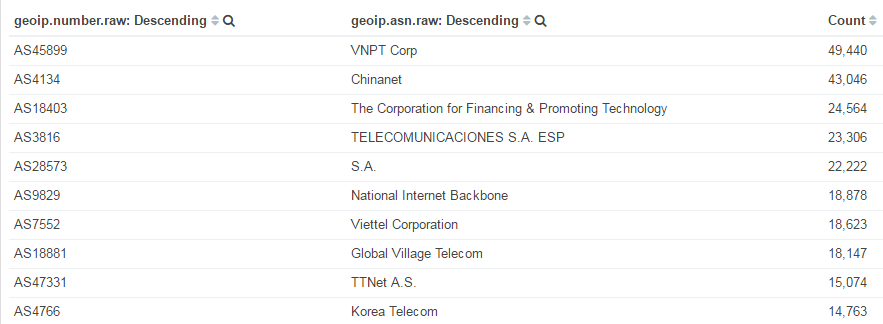
Figure 4, Top 10 ASNs of Mirai bot IPs
In the future we will still keep an eye on the progress of Mirai scans.
Besides that, we have been able to extract couple of Mirai C2s (command and controller), and added them into our DDos botnet command tracking system, with that, we will hopefully be able to track the Mirai botnet attacks (target, attack type, attack instructions) in real time. Stay tuned for more update on this.

