Early Warning: ADB.Miner A Mining Botnet Utilizing Android ADB Is Now Rapidly Spreading
Author:Hui Wang, RootKiter,
twitter/360Netlab
About 24 hours ago, around 2018-02-03 15:00(GMT +8), a set of malicious code began to spread rapidly, here are some quick facts:
- Timeline : the earliest time of the infection can be traced back to January 31. And the current worm-like infection was detected by our system from around 2018-02-03 15:00
- Infected port : 5555, which is the working port of adb debugging interface on Android device, this port should be normally closed
- Worm behavior : The Malicious code looks for open 5555 adb debug interface after successful infection, which is worm like.
- Target equipment : Most are android based devices. We will not publish details as of now.
- The number of infected equipment : 2.75 ~ 5k, so far mainly in China (~ 40%) and South Korea (~ 30%)
Also, this malware borrows some of the mirai's scanning code, this is the first time we see the mirai code being used by Android bot
Overall, we think there is a new and active worm targeting android system's adb debug interface spreading, and this worm has probably infected more than 5,000 devices in just 24 hours.
Infection Trend on Port 5555
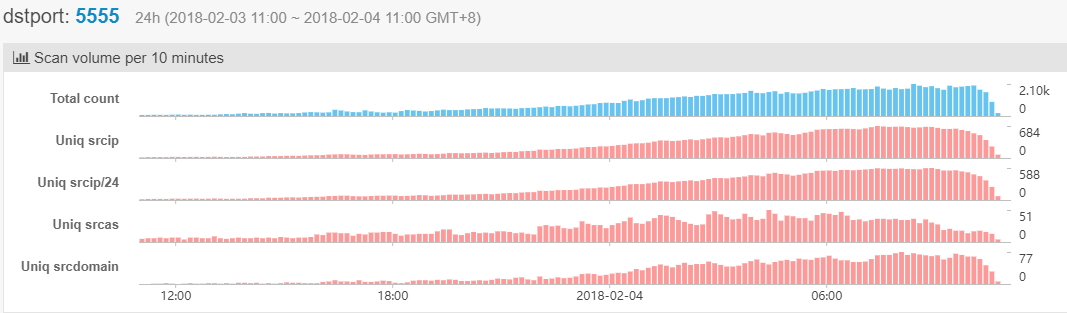
As can be seen from the figure above, the scan traffic on port 5555 starts around 15:00 pm on 2018-02-03 , reaches 3 times the daily average number, and has a tenfold increase around 24:00. the number of IPs initiating scanning and the total scanning traffic are still growing as of now.
As it can be seen below, the current 5555 port scan traffic has been gone up to the top ten of all ports on our scanmon system. The last time we saw a new port suddenly jumped to the top 10 list was the mirai botnet, which goes back to September 2016.
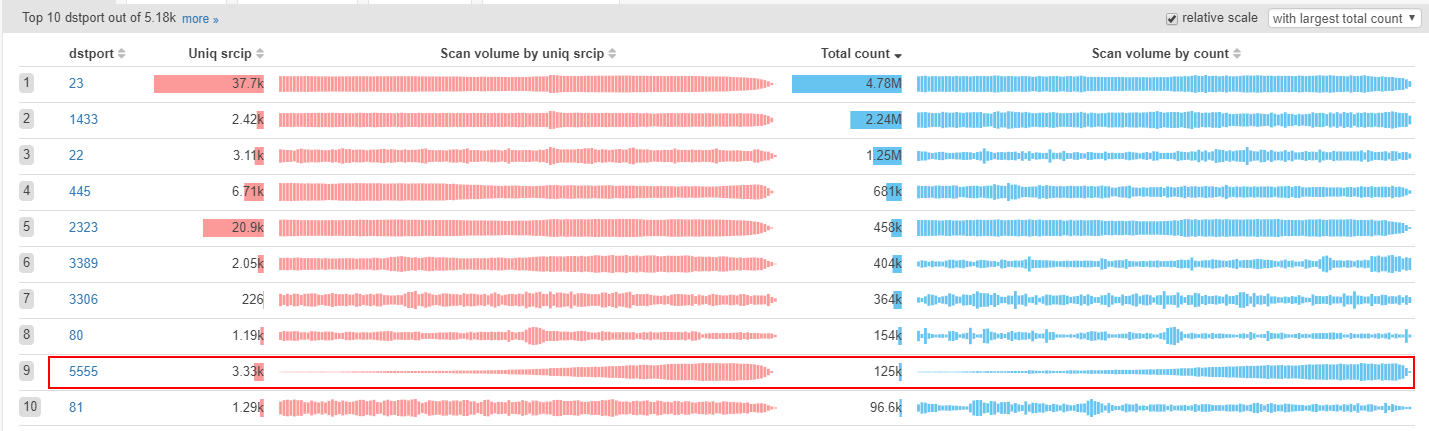
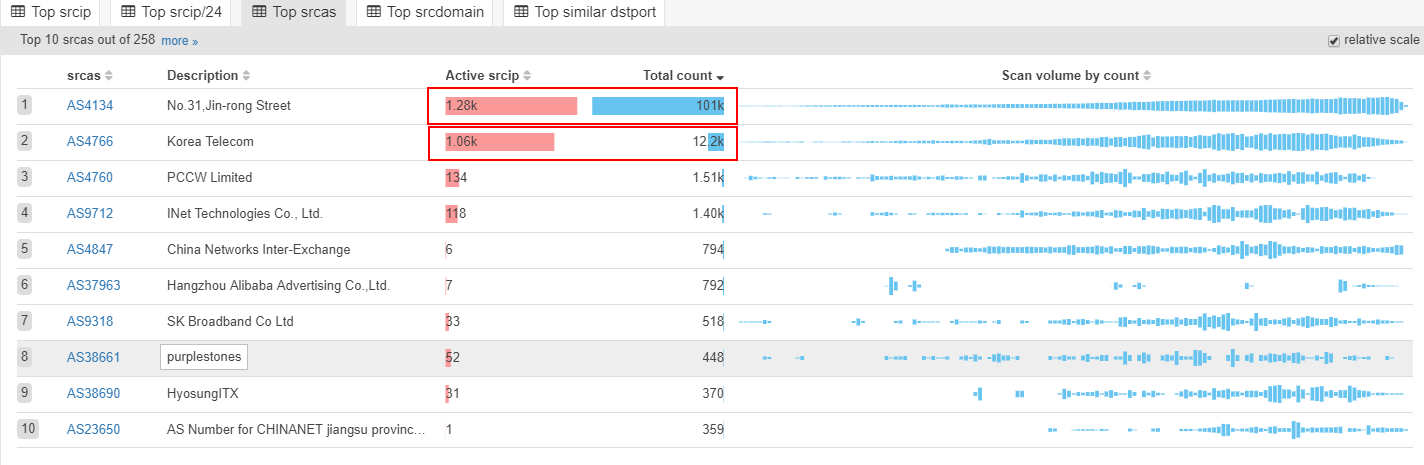
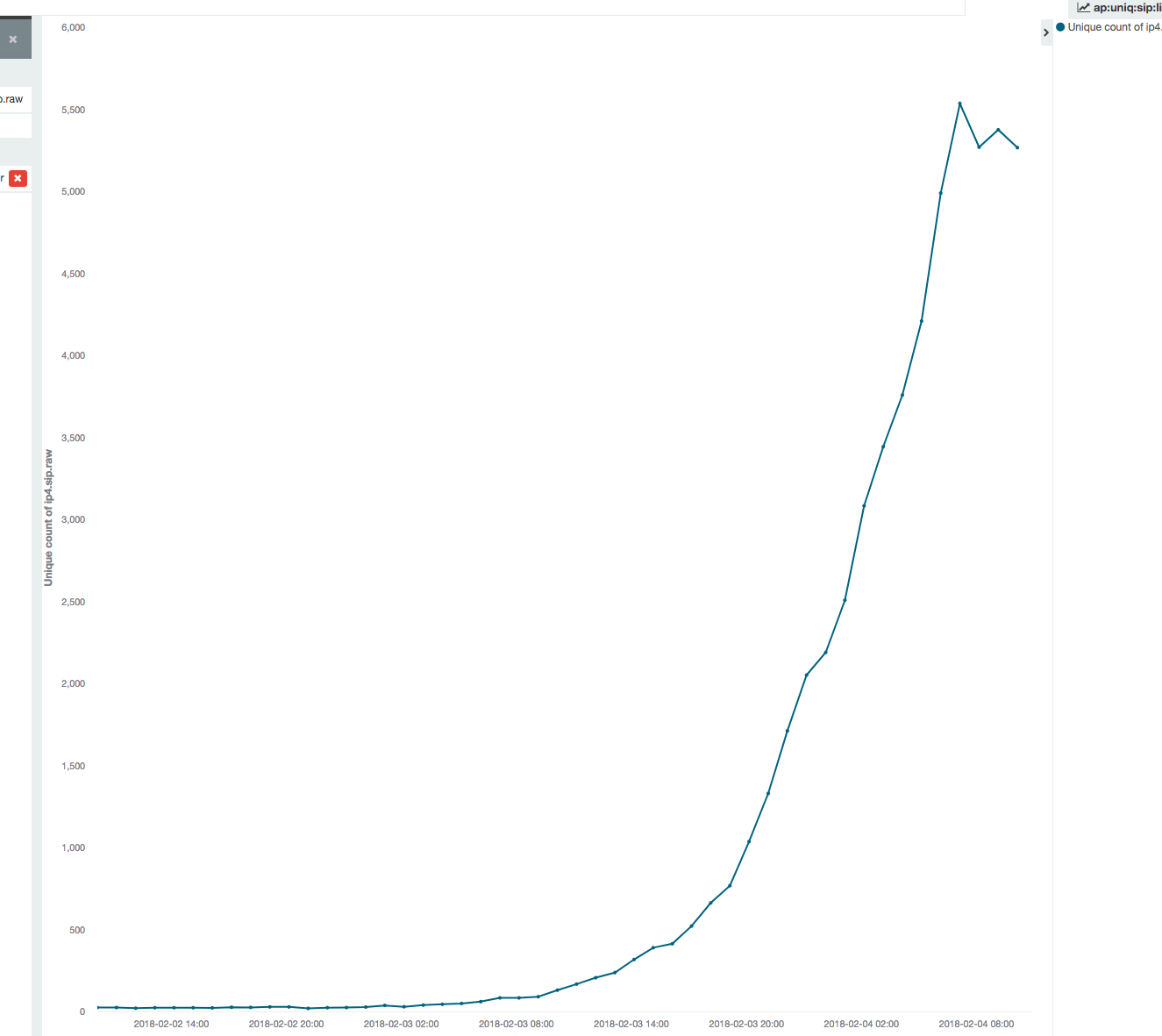
The number of unique scan sources is 2.75k on our scanmon system, and 5.5k on our botnet tracking system.
Most of the Infected devices Are Android Smart Phones or TV Box with ADB Debugging Interface Opened
Those infected devices are actively trying to spread malicious code. By analyzing the spreading source, we found that most of them are smart phones and smart TV (TV box) based on Android.
We will not publish detailed infected models here. Till now, we don't think it is a vendor level issue.
Infected Devices are Used to Dig XMR Coins
A set of malicious code are located till now. Among them, the xmrig related ones are involved in digging XMR tokens, with two groups of configurations.
These two share the same wallet address but with different mining pool address:
- Mining Pool : pool.monero.hashvault.pro:5555 or pool.minexmr.com:7777
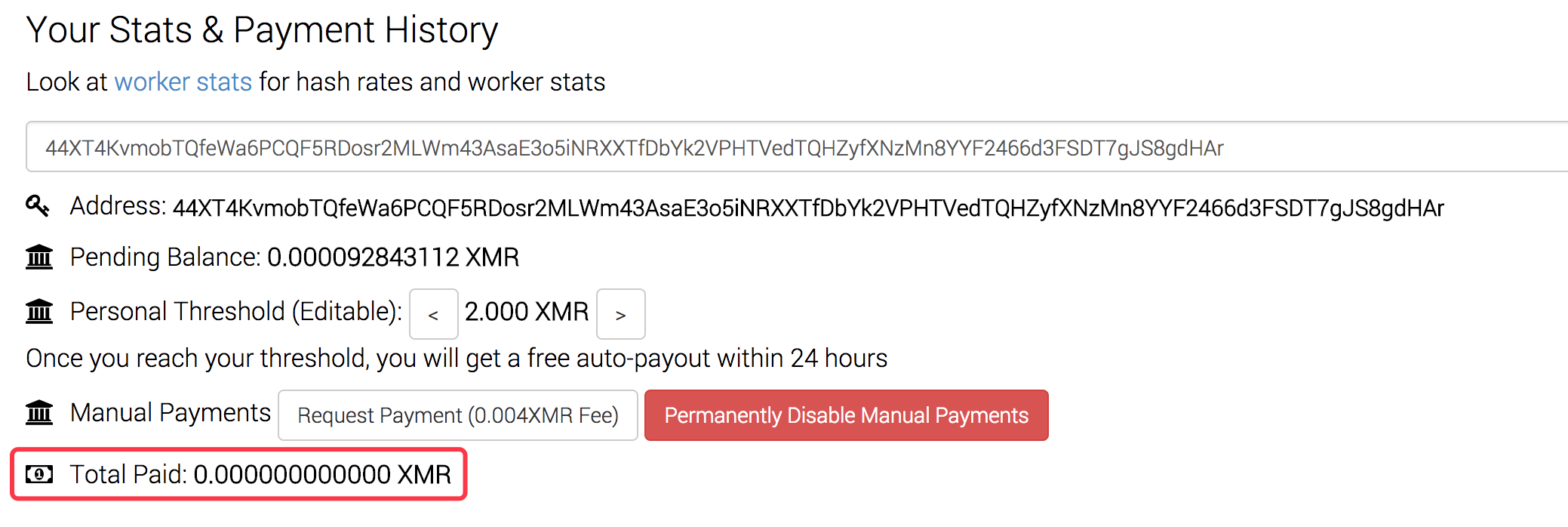
- Wallet Address : 44XT4KvmobTQfeWa6PCQF5RDosr2MLWm43AsaE3o5iNRXXTfDbYk2VPHTVedTQHZyfXNzMn8YYF2466d3FSDT7gJS8gdHAr
- Pool Pass : x
Till now, zero coins have been paid, as can be seen in below:
We will post any important update here to further illustrate this, stay tuned.

