GPON Exploit in the Wild (II) - Satori Botnet
This article was co-authored by Rootkiter, Yegenshen, and Hui Wang.
In our previous article, we mentioned since this GPON Vulnerability (CVE-2018-10561, CVE-2018-10562 ) announced, there have been at least five botnets family mettle, muhstik, mirai, hajime, satori actively exploit the vulnerability to build their zombie army in just 10 days.
We mainly focused on the muhstik botnet in the previous blog. Before and after the publication of the article, through joint efforts with the security community, we managed to kill 12 IP addresses of the Muhstik botnet on the OVH and 1 IP address on the Microsoft network. For a detailed list of IP addresses, see the Annex IoC section.
One thing noteworthy is about these botnets' exploit effectiveness. From our estimate, only 2% all GPON home router is affected, most of which located in Mexico. This happens because of the way they utilizing the published PoC.
Now let’s take a look at the these botnets:
- Satori: Satori is the infamous variant of the mirai botnet.
- We first observed this botnet coming after the GPON vulnerable devices at 2018-05-10 05:51:18, several hours before our last publish.
- It has quickly overtakes muhstik as the No.1 player.
- Mettle: A malicious campaign based on IP addresses in Vietnam (C2 210.245.26.180:4441, scanner 118.70.80.143) and mettle open source control module
- Hajime: Hajime pushed an update which adds the GPON's exploits
- Two Mirai variants: At least two malicious branches are actively exploiting this vulnerability to propagate mirai variants. One of them has been called omni by newskysecurity team.
- imgay: This appears like a botnet that is under development. Its function is not finished yet.
This article will mainly introduce the current update of the Satori botnet. In the follow-up we may publish a third article and go over the remaining ones.
Comparison of Delivery Frequency of Different Botnets
Honeypot data can provide some basic comparison between different botnets that try to hit the GPON-related vulnerabilities. And following is a top10 list of attack payload that been requested by the bots. For a complete list, see the IoC section at the end of the article:
% botnet_name url
57.77% satori hxxp://185.62.190.191/r
32.66% muhstik hxxp://51.254.219.134/gpon.php
2.20% muhstik hxxp://162.243.211.204/gpon
1.99% muhstik hxxp://165.227.78.159/gponb6abe42c3a9aa04216077697eb1bcd44.php
0.96% muhstik hxxp://128.199.251.119/gpon.php
0.64% imgay hxxp://149.28.96.126/forky
0.60% imgay hxxp://149.28.96.126/80
0.57% imgay hxxp://149.28.96.126/
0.57% imgay hxxp://149.28.96.126/81
0.53% muhstik hxxp://165.227.78.159/gpon.php
You can see Satori (account for 57.80% of all attempts we saw) and muhstik (38.87%) are the main force behind of the current GPON exploits bots.
Satori Malware Download URL
The new Satori uses the following set of URLs to propagate malicious code:
hxxp://185.62.190.191/arm
hxxp://185.62.190.191/arm7
hxxp://185.62.190.191/m68k
hxxp://185.62.190.191/mips
hxxp://185.62.190.191/mipsel
hxxp://185.62.190.191/r
hxxp://185.62.190.191/sparc
Satori Malicious Code Samples Analysis
Take this sample as an example:
hxxp://185.62.190.191/arm md5hash:d546bc209d315ae81869315e8d536f36
The code of this sample has changed a lot from the original version of Satori. From the aspect of sample binary alone, the relationship with the original Satori is not very strong. However, considering some of its key factors, such as some key strings, domain name TXT information, email addresses, etc., we still attribute it to the Satori variant.
There are four encrypted strings in this sample, and the corresponding decryption results are as follows:
- c.sunnyjuly.gq
- Viam0610TCiLpBvezPFGL2aG
- {"id":0,"jsonrpc":"2.0","method":"miner_reboot"}
- {"id":0,"jsonrpc":"2.0","method":"miner_file","params":["reboot.bat","4574684463724d696e657236342e657865202d65706f6f6c206574682d7573322e6477617266706f6f6c2e636f6d3a38303038202d6577616c20307864303839376461393262643764373735346634656131386638313639646263303862656238646637202d6d6f64652031202d6d706f72742033333333202d6d707377206775764a746f43785539"]}
The first string is the C2.
The second string will be printed at the device console.
The third and fourth strings are only defined but not being used.
It is worth mentioning that these two strings are similar to the code used in Satori.robber, which can serve as a circumstantial evidence that the sample is homologous to Satori.
The Hex part of the fourth string can be deciphered as follows. Although not used, it looks like a command string, containing a mine pool address, and a wallet address
EthDcrMiner64.exe -epool eth-us2.dwarfpool.com:8008 -ewal 0xd0897da92bd7d7754f4ea18f8169dbc08beb8df7 -mode 1 -mport 3333 -mpsw guvJtoCxU9
The Wallet Address of Satori
The wallet address information is as follows. According to the current estimate of $700 per ETH token, Satori received a total of approximately $200 in the current 6-day operation
$ curl "http://dwarfpool.com/eth/api?wallet=0xd0897da92bd7d7754f4ea18f8169dbc08beb8df7"
{
"autopayout_from": "0.050",
"earning_24_hours": "0.04629051",
"error": false,
"immature_earning": 0.0037158866909999997,
"last_payment_amount": "0.05286277", #last pay amout
"last_payment_date": "Tue, 15 May 2018 17:26:04 GMT", #last pay day
"last_share_date": "Wed, 16 May 2018 09:46:47 GMT",
"payout_daily": false,
"payout_request": false,
"total_hashrate": 137.57,
"total_hashrate_calculated": 781.0,
"transferring_to_balance": 0,
"wallet": "0xd0897da92bd7d7754f4ea18f8169dbc08beb8df7", #wallet address
"wallet_balance": "0.02818296", #balance due to pay
"workers": {
"": {
"alive": true,
"hashrate": 137.57,
"hashrate_below_threshold": false,
"hashrate_calculated": 781.0,
"last_submit": "Wed, 16 May 2018 09:46:47 GMT",
"second_since_submit": 335,
"worker": ""
}
}
}
The Domain Name and the Out-coming Message from Its TXT
The C2 name in the sample c.sunnyjuly.gq has no IP address resolution yet. But, it does provide TXT record, which might carry the information its author communicates to the outside world. The author changed TXT information twice so far and note it uses a @riseup.net email address
2018-05-14 04:22:43 c.sunnyjuly.gq DNS_TXT Irdev here, i can be reached at village@riseup.net, goodbye
2018-05-10 00:55:06 c.sunnyjuly.gq DNS_TXT It is always the simple that produces the marvelous
Worth noting that the origin Satori.robber also used the same DNS zone sunnyjuly.qg. At that time, the author also leave a message in the sample, as follows. The email address in it is also a @riseup.net。
Satori dev here, dont be alarmed about this bot it does not currently have any malicious packeting purposes move along. I can be contacted at curtain@riseup.net
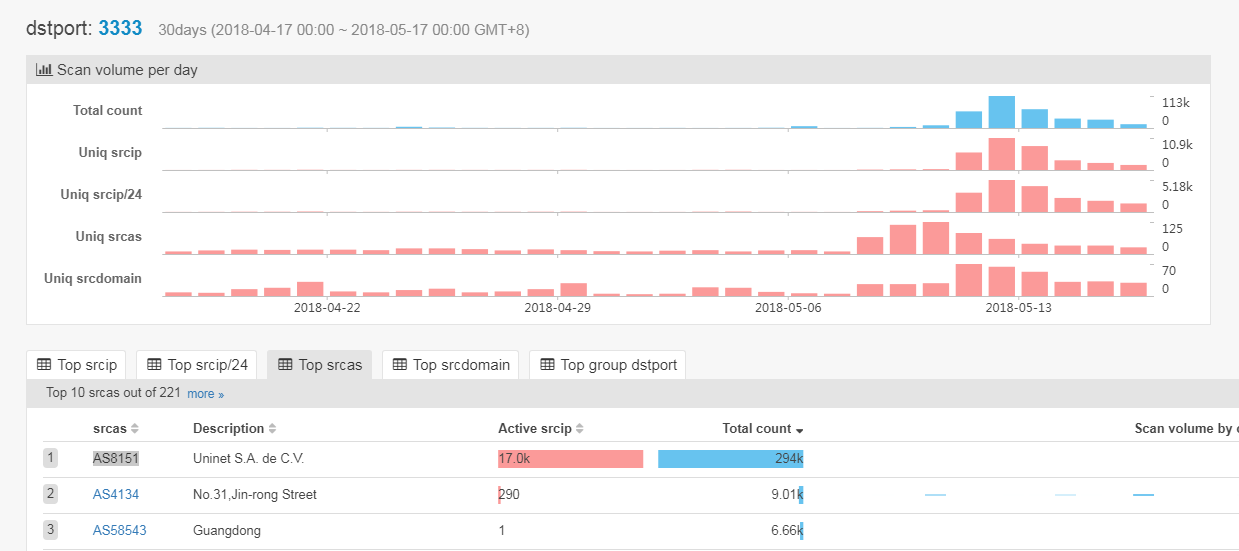
The Port 3333 Scan Spike Caused by Satori
The current version of Satori also scans port 3333 which can be seen at our ScanMon system. The source of this scan is about 17k independent IP addresses, mainly from Uninet SA de CV, telmex.com, located in Mexico.
Contact Us
We can be reached at twitter or at WeChat subscription account 360Netlab.
Ioc
Those IPs once under muhstik control, but now cleared by security community:
139.99.101.96:9090 AS16276 OVH SAS
142.44.163.168:9090 AS16276 OVH SAS
142.44.240.14:9090 AS16276 OVH SAS
144.217.84.99:9090 AS16276 OVH SAS
145.239.84.0:9090 AS16276 OVH SAS
145.239.93.125:9090 AS16276 OVH SAS
147.135.210.184:9090 AS16276 OVH SAS
192.99.71.250:9090 AS16276 OVH SAS
51.254.221.129 "AS16276 OVH SAS"
66.70.190.236:9090 AS16276 OVH SAS #当前未生效
51.254.219.137 "AS16276 OVH SAS"
51.254.219.134 "AS16276 OVH SAS"
191.238.234.227 "AS8075 Microsoft Corporation"
All the malware downloading URLs exploiting GPON vulnerability.
% botnet_name url Country & Region ASN
57.77% satori hxxp://185.62.190.191/r Netherlands/NL AS49349 Dotsi, Unipessoal Lda.
32.66% muhstik hxxp://51.254.219.134/gpon.php France/FR AS16276 OVH SAS
2.20% muhstik hxxp://162.243.211.204/gpon United States/US New York AS62567 DigitalOcean, LLC
1.99% muhstik hxxp://165.227.78.159/gponb6abe42c3a9aa04216077697eb1bcd44.php United States/US Clifton AS14061 DigitalOcean, LLC
0.96% muhstik hxxp://128.199.251.119/gpon.php Singapore/SG Singapore AS14061 DigitalOcean, LLC
0.64% imgay hxxp://149.28.96.126/forky United States/US College Park None
0.60% imgay hxxp://149.28.96.126/80 United States/US College Park None
0.57% imgay hxxp://149.28.96.126/ United States/US College Park None
0.57% imgay hxxp://149.28.96.126/81 United States/US College Park None
0.53% muhstik hxxp://165.227.78.159/gpon.php United States/US Clifton AS14061 DigitalOcean, LLC
0.32% muhstik hxxp://162.243.211.204/gponexec United States/US New York AS62567 DigitalOcean, LLC
0.28% imgay hxxp://149.28.96.126/8080 United States/US College Park None
0.25% untitled-1 hxxp://186.219.47.178:8080 Brazil/BR AS262589 INTERNEXA Brasil Operadora de Telecomunicações S.A
0.11% imgay hxxp://149.28.96.126/imgay United States/US College Park None
0.11% muhstik hxxp://162.243.211.204/aio United States/US New York AS62567 DigitalOcean, LLC
0.11% muhstik hxxp://46.243.189.102/ Netherlands/NL AS205406 Hostio Solutions B.V.
0.07% untitled-2 hxxp://114.67.227.83/busybox China/CN Beijing AS4808 China Unicom Beijing Province Network
0.07% omni hxxp://185.246.152.173/omni Netherlands/NL AS56630 Melbikomas UAB
0.07% untitled-2 nc://114.67.227.83:7856 China/CN Beijing AS4808 China Unicom Beijing Province Network
0.04% satori hxxp://185.62.190.191/s Netherlands/NL AS49349 Dotsi, Unipessoal Lda.
0.04% untitled-2 hxxp://114.67.227.83 China/CN Beijing AS4808 China Unicom Beijing Province Network
0.04% untitled-3 hxxp://209.141.42.3/gponx United States/US Las Vegas AS53667 FranTech Solutions
0.04% untitled-2 hxxp://114.67.227.83/ China/CN Beijing AS4808 China Unicom Beijing Province Network

