Memcache DDoS: A Little Bit More
This blog is a joint effort of 360 0kee Team, 360 CERT, and 360 Netlab.
Memcache UDP Reflection Amplification DDoS (hereinafter referred as Memcache DRDoS) has attracted quite some attentions from security community this week. We are not going to repeat the public known facts, and this blog will only touch base with some more details,
Original Disclosure on POC 2017 Meeting
Memcache DRDoS, was first disclosed around 2017-06, by 0kee team from our company. Here is the detailed document first published in November 2017, at PoC 2017 conference
In this document, we point out:
- An extremely high bandwidth amplification factor, at least 50k
- The number of potential reflection points is large, estimated around 60k utilizable memcache server in November, 2017. And these servers tend to have higher bandwidth resources
Current Trends on DDoSMon
Since the disclosure, we have been using DDosMon to monitor memcache DRDoS on the backbone level. In the past few months, this kind of attack is not very popular, but things have greatly changed since February 24th, 2018.
Just in a few days, Memcache DRDoS rise up from less than 50 events per day, up to 300~400 per day. And today's number has already reached 1484, with an hour to go. These numbers are shown in the following figure:
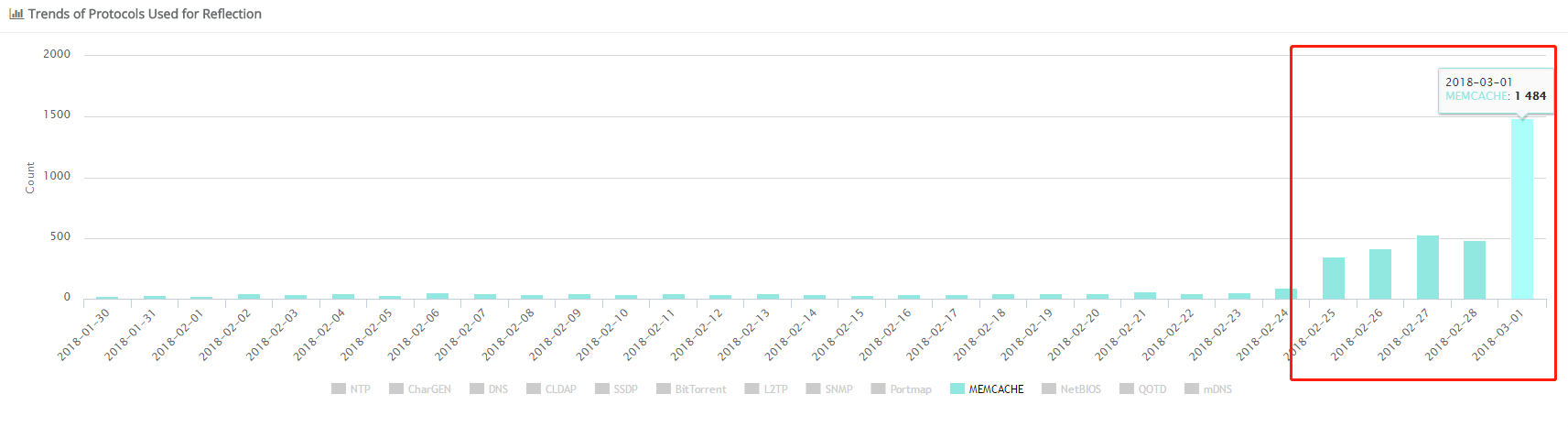
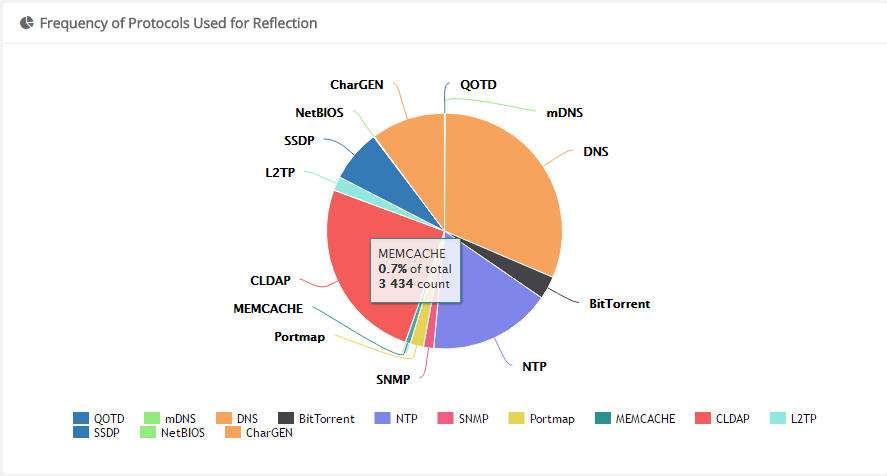
It should be noted that current Memcache DrDoS is still not the mainstream of DDoS.
It accounts for less than 1% in all DRDoS, ranks after DNS, CLDAP, NTP, SSDP, CharGen, L2TP, BitTorrent, Portmap and SNMP.
The Real Amplification Factors We Tests on Real Network
So how big the amp factor we should be expecting in real attacks? We performed some tests, as well as analyzed some real attack payloads we captured, and the following are some numbers:
- The amplification factor, from 1k to 60k, can be stably achieved in our testing environment
- We reached the maximum 60k amplification factor in real network
- These test results are consistent with those of the original 0kee team estimates, and the US-CERT Alarm.
- The maximum 60k amplification factor can not be achieved by the attack payload we have captured. Those payloads are somehow problematic, may cause the memcache server crash, so the attack cannot continue. But an easy fix will take care the bug, the attacker would be able to achieve a 60k amplification factor eventually.
- What is more, even an amplification factor higher than 60k can be made, but we will not discuss the details here.
Currently Known Attack Cases
Akamai has just reported a DDoS attack case, with the peak attack traffic at 1.3Tbps, a new Akamai record after 2016 Mirai DDoS attack against KrebsonSecuritycom.
On February 27, Qrator Labs reported a DDoS attack case on medium.com. According to the article, this attack is on UDP 11211 port, and convinced Memcache DRDoS, with the peak attack traffic as high as 480Gbps.
Beside these reported cases, we believe other big attacks have actually occurred but not publicly reported.
Current Countermeasures Taken by ISPs and Security Communities
Currently, a number of related security notices have already released, part of which:
- Notifications: Multiple security vendors, certs have issued notices, such as CloudFlare, Qrator Labs, Arbor Networks, US-CERT, and so on
- Defensive Actions: Multiple ISPs, including NTT have placed rate limits on UDP 11211 port.
At this point, we probably will start to see more bigger attacks, "G era" to "T era of DDoS" might have started.
Our DDosMon Memcache page
When event like this happens, one of the security community needs is the visibility, we have temporally setup a webpage here on our DDosMon page to track in near real-time about the Memcache attacks, it displays the Memcache attack trend, victims and some statistic, feel free to take a look.
