Malware uses namesilo Parking pages and Google's custom pages to spread
Abstract
Recently, we found a suspicious GoELFsample, which is a downloder mainly to spread mining malwares. The interesting part is that we noticed it using namesilo's Parking page and Google's user-defined page to spread the sample and configuration. Apparently this is yet another attempt to hide control channel to avoid being tracked|monitored|blocked from the malicious actor and it probably has served them well.
The exact sample had been reported by Tencent security team, but the analysis of the propagation is not quite accurate. It is often thought that during the domain parking period (Domain Parking), the content displayed on the page is managed by the domain parking provider, and the actual owner of the domain cannot modify its page content. However, in this case, the domain parking provider allows the domain owner to customize the parking page. The attacker took advantage of this, along with the custom pages provided by Google, to spread his malware.
This has two obvious benefits: on the one hand, the attacker hardly needs to pay any bandwidth and server costs for the malicious code distribution; on the other hand, as the bots ‘talk’ to the domain parking provider and google, the control traffic totally blends in, making it very difficult to be monitored and blocked.
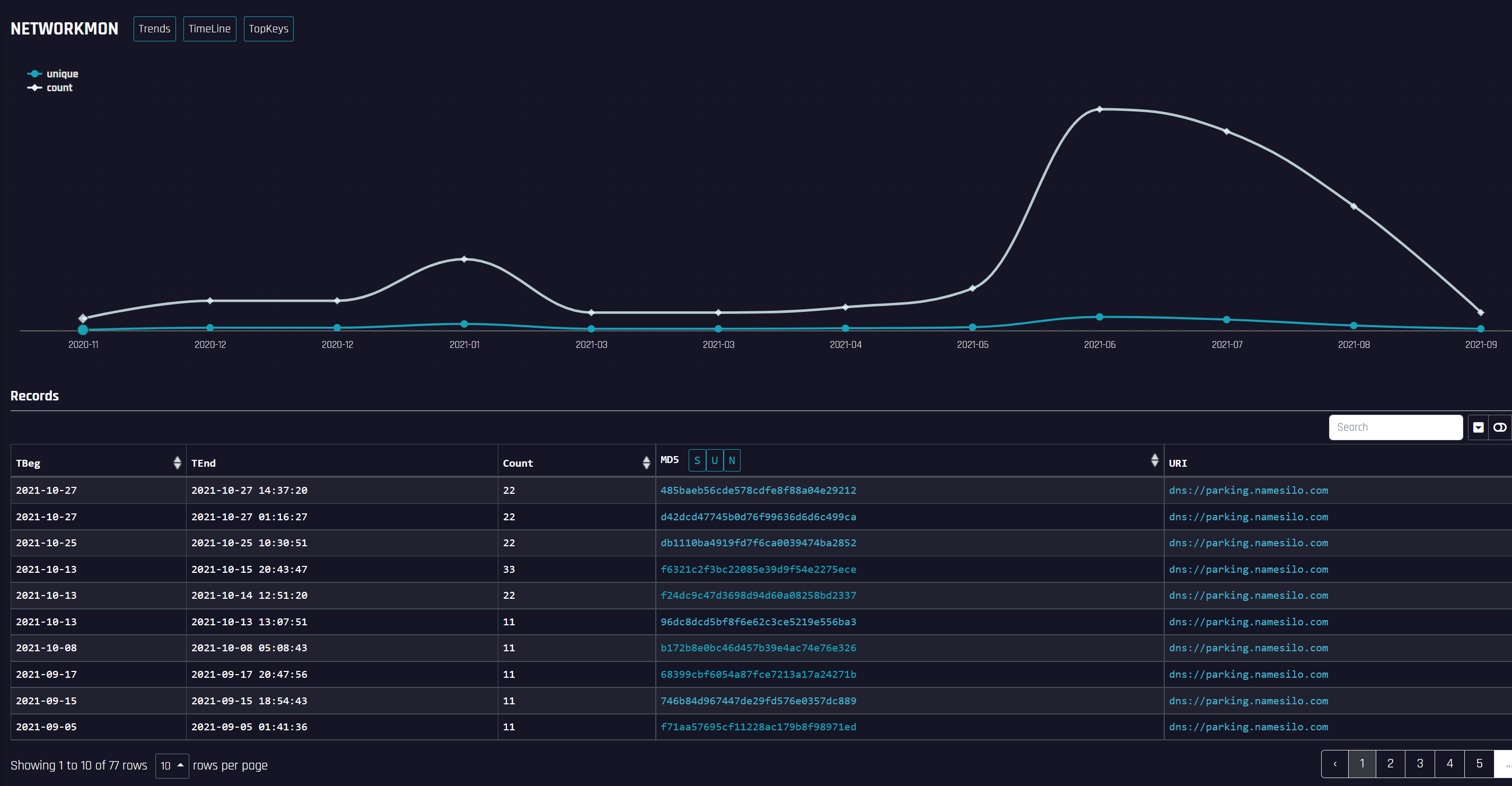
From our DNSMon/DTA monitoring data, we see this new trend has shown signs of increase in recent months.
Origins
On 10.13, our BotnetMon IDed a suspicious GoELF sample that would request a known suspicious domain www[.]hellomeyou.cyou, which Tencent had covered in a previous mining malware report.
There is nothing particularly interesting regarding to the mining part, however, we noted that the DNS resolution of www.hellomeyou.cyou has historically been CNAME to a parking domain parking.namesilo.com
2020-11-09 2021-11-07 19904 www.hellomeyou.cyou CNAME parking.namesilo.com
The parking domains are usually registered but not activated, how could they be a part of the malicious sample distribution?
Logging into namesilo's user service interface, we learned that its ParkingPage is user-definable content, which in turn gives hacker groups the opportunity to exploit it.
Multiple historical snapshots of the site in our DNSMon system showed that the title of the page was a malicious sample link, and the description of the page was xmrig configuration.
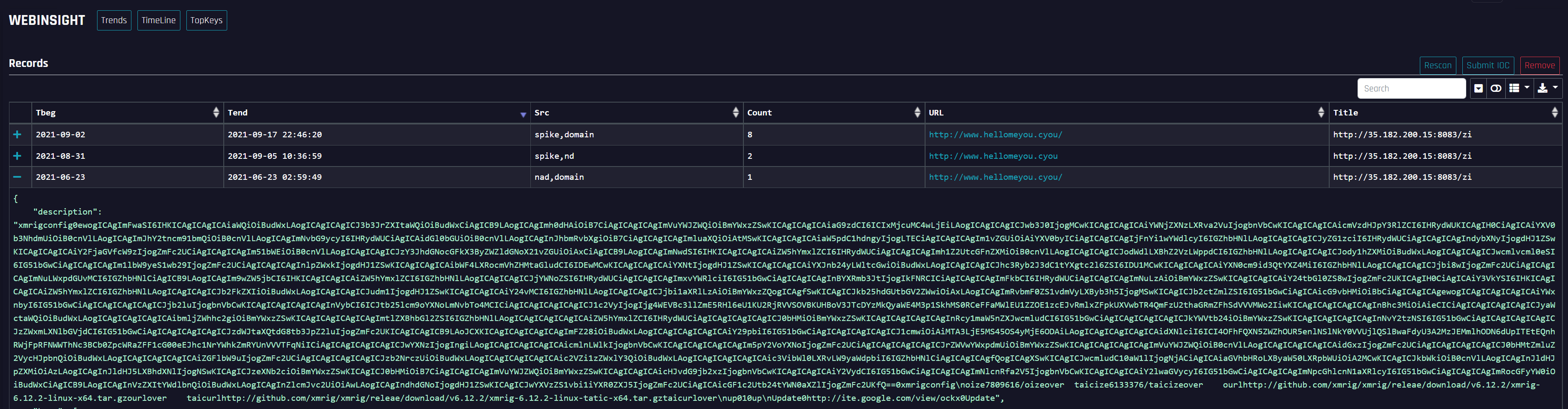
At the same time, there is also the exploitation of github and google links in the description, which further analysis shows that both are a part of malware distribution channel. Among them, google's custom page contains a base64 encoded xmrig mining software.
When talk about Parking domain related security issues, many articles out there would refer to some well known problems, mainly Malvertising and abuse related.
In this case, it is different. This particular case uses the “user-customize" parking page directly for its control channel. Hackers do not need to have their own machines and IPs, they just use the parked pages provided by the domain registrar, as well as the custom pages of google(see the following snapshot) to help spreading their malware. By doing this, the malicious actor totally goes under the radar because all the control channel traffic use these totally legit "public facilities”
Correlation
Through the page similarity correlation analysis, we see a total of 8 web records with similar configurations in the historical data.
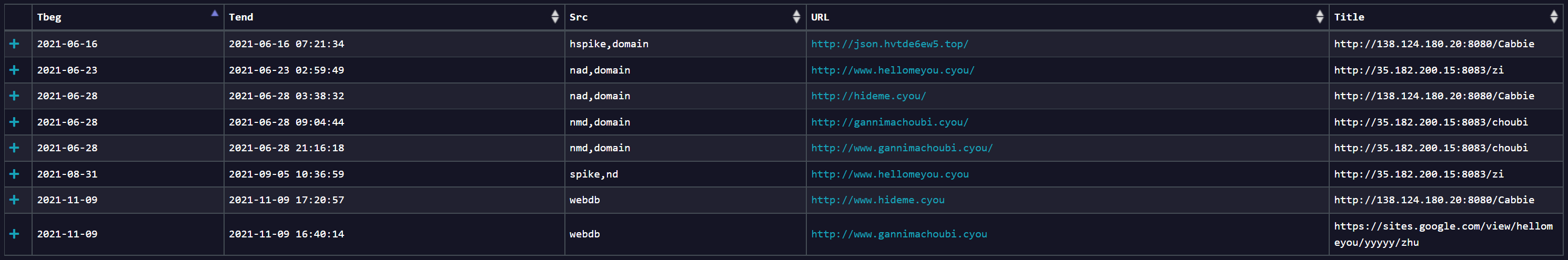
Corresponding to the capture of 2 samples
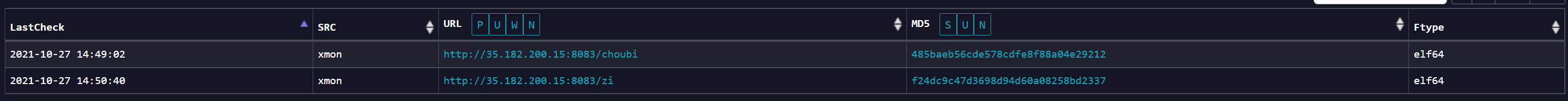
We retraced the history of the malicious samples involving parking.namesilo.com in our BotnetMon and could see an upward trend since June this year, looks like this technique might have been working well, we will keep an eye on it.
IOC
485baeb56cde578cdfe8f88a04e29212
96dc8dcd5bf8f6e62c3ce5219e556ba3
f06d38aa4f472a7e557069cc681d997c
f24dc9c47d3698d94d60a08258bd2337
f6321c2f3bc22085e39d9f54e2275ece
hideme.cyou
hellomeyou.cyou
gannimachoubi.cyou
hvtde6ew5.top
https://sites.google.com/view/dogtoken/Home
https://sites.google.com/view/tabjoy/



