Emptiness: A New Evolving Botnet
Background
Our honeypot system captured a new DDoS botnet sample on 2019-06-23. We named it Emptiness which comes from the running process name as well as its C2 domain. Emptiness is written by Golang and supports both Windows and Linux. Our further analysis reveal its iterative evolution: the early version Emptiness was only armed with DDoS function and was propagated through Mirai.shiina variant botnet that had been run by the same author for a long time. The latter version Emptiness was added with ssh scan to enable self-propagation. Besides, C2 communication protocols of both Emptiness and Mirai.shiina kept changing constantly, which increases the difficulty of being tracked by security researchers.
The Timeline of Emptiness
-
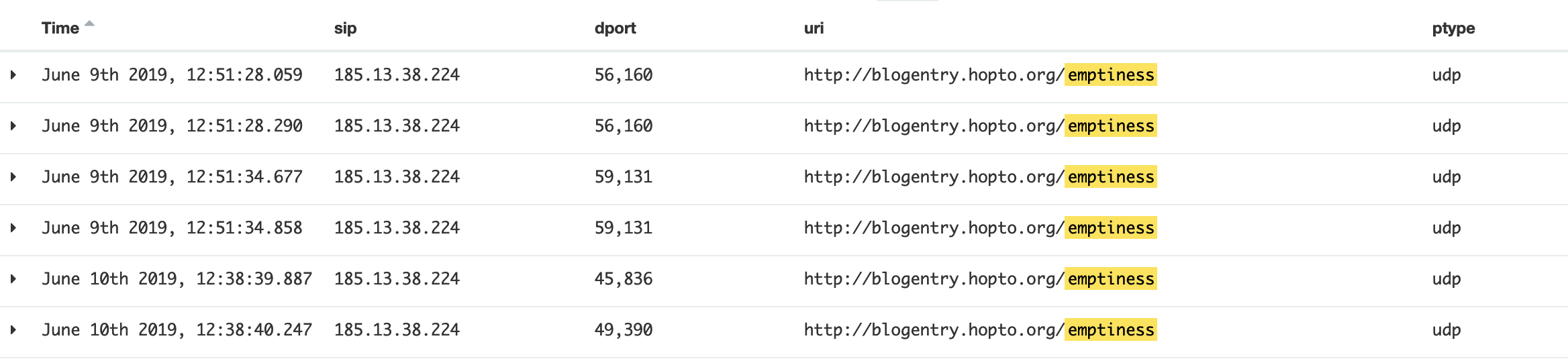
2019-06-09: we first observed Emptiness download URL,but was not able to download the bot sample at that time.
-
2019-06-23: we captured bot sample Emptiness.V1
-
2019-06-26: we captured bot sample Emptiness.V1.1
-
2019-07-03: we exposed DDoS attacks launched by Emptiness.v1.1
-
2019-07-06: we captured bot sample Emptiness.v2, which said hello to us (360Netlab) "politely".

Emptiness Sample Analysis
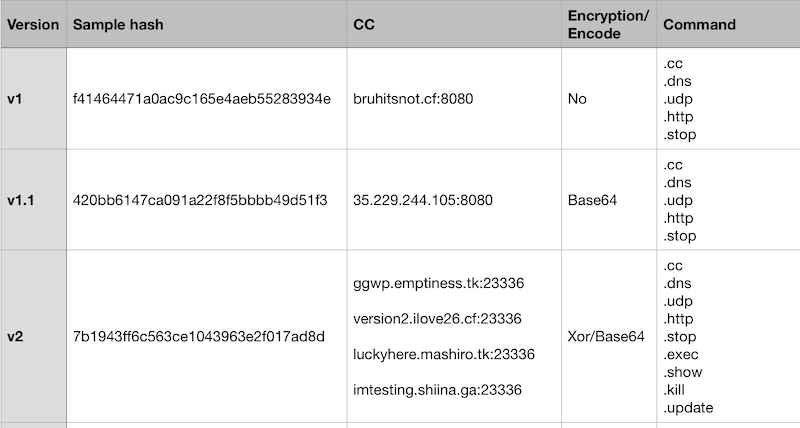
The following table summarizes the main differences between three versions of Emptiness.
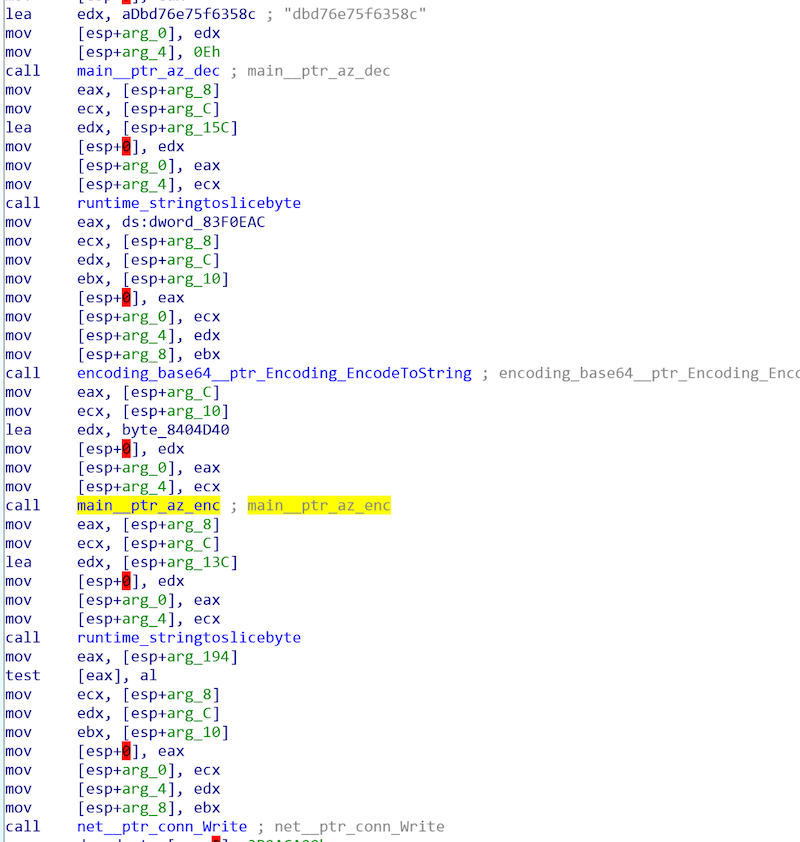
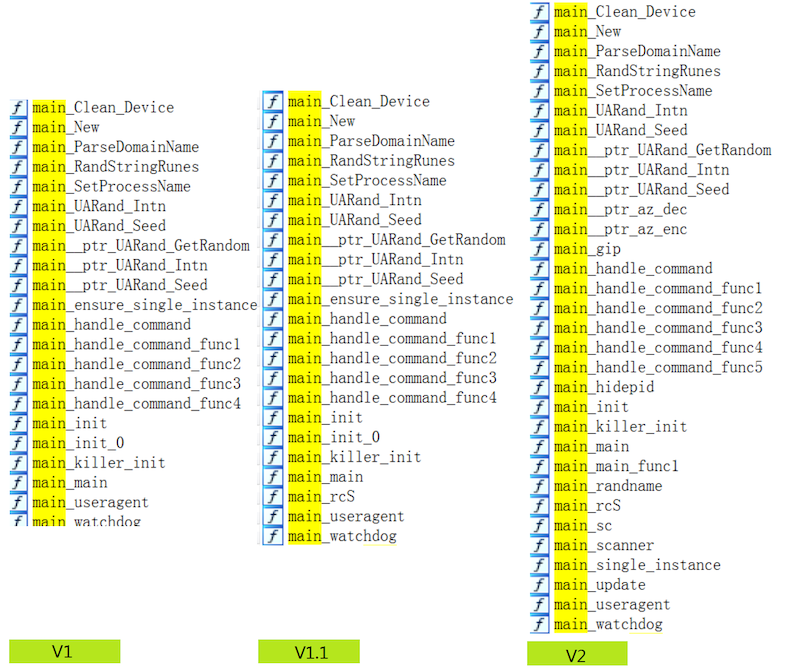
All these three versions are written by Golang and are protected by standard UPX. As shown in the following figure, their main function logics are mainly implemented in main package and can be categorized into three aspects: host behavior, data encoding/encryption and C2 protocol. Next we will introduce Emptiness from these three aspects.
Host Behavior
Most host behaviors performed by Emptiness are common operations, such as ensuring singleton, modifying process name, turn off watchdog, clear history logs, delete system command, stop system service and so on. The only thing worth to note is that Emptiness will kill process using specific ports through its main_killer_init function. In this way, it can remove bot competitors and close vulnerable ports and thus occupy victim machine exclusively. The following figures show its methods of killing process and the ports it intends to kill.
-
Methods of killing process
-
V1 & V1.1
fuser -k -n tcp -
V2
1: fuser -k /tcp 2: lsof -i tcp:%s | grep LISTEN | awk '{print $2}' | xargs kill -9
-
-
Ports it intends to kill:
"22" "23" "80" "420" "1337" "1991" "5332" "6553" "6554" "6666" "6667" "6697" "18904" "37215" "42026" "48101" "52869" "57643"
Data Encoding and Encryption
We demonstrate how Emptiness encodes or encrypts data in different versions using its register message.
-
Emptiness.V1 communicate through plaintext and no encoding or encryption is involved.
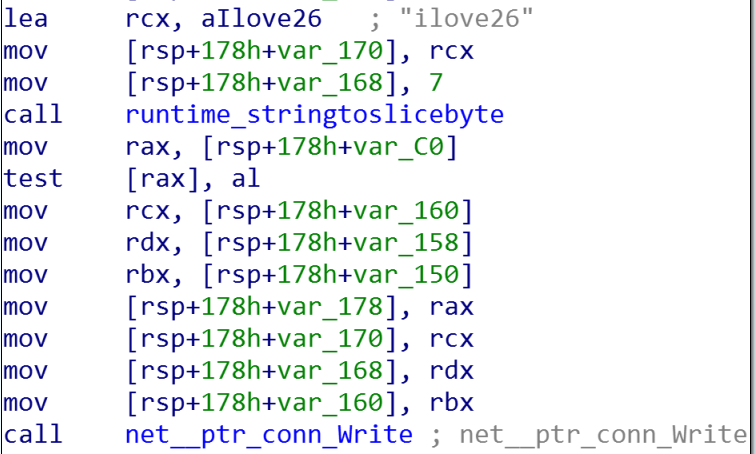
-
Emptiness.V1.1 encodes the message with Base64
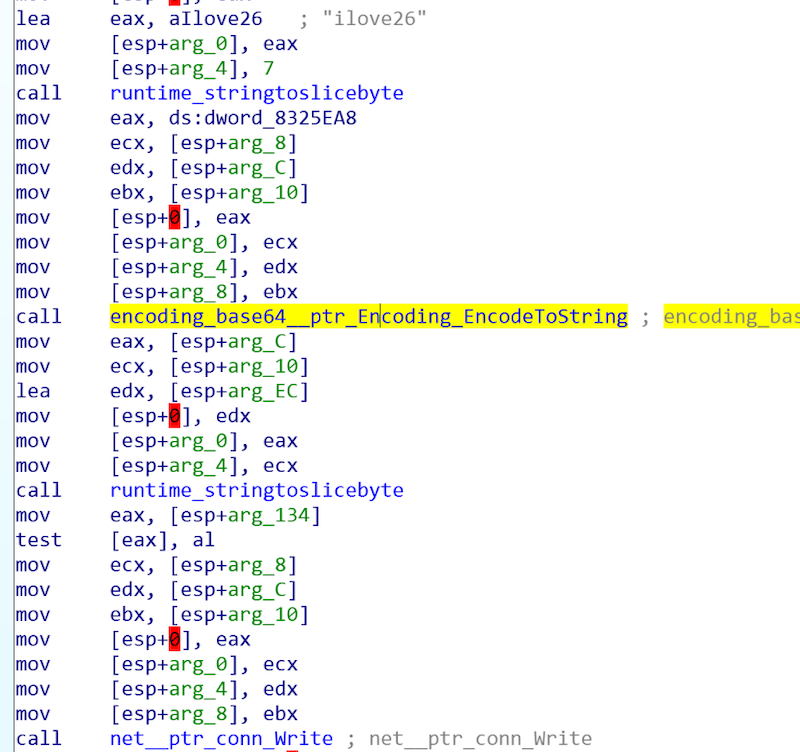
-
Emptiness.V2 first encodes the message with Base64, then encrypts it with XOR transformation and the XOR key is “B2BB01039307BAA2"
C2 Protocol
Register Message
-
Emptiness.v1
00000000 69 6c 6f 76 65 32 36 |ilove26| -
Emptiness.v1.1
00000000 61 57 78 76 64 6d 55 79 4e 67 3d 3d |aWxvdmUyNg==| Base64 encode,plaintext is:ilove26 -
Emptiness.v2
00000000 64 33 65 63 37 39 37 35 66 37 36 61 65 66 64 62 |d3ec7975f76aefdb| 00000010 66 63 64 63 33 63 33 65 |fcdc3c3e| Base64 encode and then XOR transformation,plaintext is:ilove26
Supported Command
-
Emptiness.V1 and Emptiness.V1.1
.cc .udp .dns .http .stop -
Emptiness.V2
.cc .dns .udp .http .stop .exec .slow .kill .update
Examples of DDoS Attack Command
- UDP attack
LnVkcCAxMi4xNjIuMjIwLjEwNiA4MCAyNTYgNTUgNzIw
Base64 decode
00000000 2e 75 64 70 20 31 32 2e 31 36 32 2e 32 32 30 2e |.udp 12.162.220.|
00000010 31 30 36 20 38 30 20 32 35 36 20 35 35 20 37 32 |106 80 256 55 72|
00000020 30 |0|
- HTTP attack
Lmh0dHAgd3d3LmxscnJ5LmNuIDgwIC8gNjAgNjA=
Base64 decode
00000000 2e 68 74 74 70 20 77 77 77 2e 6c 6c 72 72 79 2e |.http www.llrry.|
00000010 63 6e 20 38 30 20 2f 20 36 30 20 36 30 |cn 80 / 60 60|
The Relation between Emptiness and Mirai.shiina
Two of the four Emptiness.V2 C2 servers(luckyhere.mashiro.tk and imtesting.shiina.ga) were used by mirai variant. Mirai.shiina and the corresponding sample is f6e9f3567684a0a7402ad97209b8525b. We name it Mirai.shiina based on its infection command /bin/busybox SHIINA and its sample file name shine.{arch}. Sharing the same C2 server strongly indicates that Emptiness and Mirai.shiina belong to the same author.
More Info about Mirai.shiina
Our monitor system shows that Mirai.shiina botnet was running at least from 2019-03 to 2019-07 and during this period it was very active and deliver attack command frequently. The figure below shows some example of its attack commands.
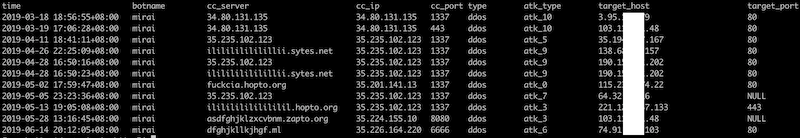
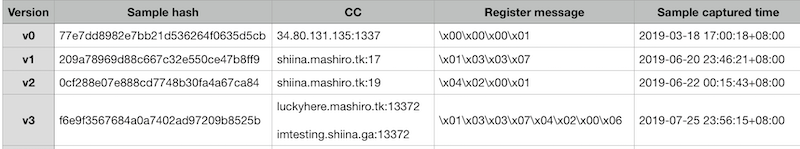
Besides, we can divide Mirai.shiina into four versions according to the difference of its C2 protocol, see the following table and we infer that the author kept modifying C2 protocol continuously to prevent from being tracked.
Question: Why the author wants to build the new Emptiness Botnet?
According to the above analysis, we know that the author of Emptiness has also run Mirai.shiina botnet for a long time, which is active to launch DDoS attacks and seems to own quite a few bots. So why the author still wants to build the new Emptiness botnet? We guess the reasons behind are:
- To support cross platform. Emptiness is written by Golang, which can be easily migrated across different platform. Golang currently supports more than 40 platforms, including
android/arm,Darwin/arm,linux/arm,windows/arm, etc. - To evade detection. Today Mirai is commonly known and can be detected by most of anti-virus engines. Developing a completely new botnet can greatly decrease the risk of being detected. As an example, we submit one Emptiness sample to VT and found that only one anti-virus vendor identified it as malware.
Contact us
Readers are always welcomed to reach us on twitter, WeChat 360Netlab or email to netlab at 360 dot cn.
IoC
Emptiness CC
emp.web2tor.cf
bruhitsnot.tk
bruhitsnot.cf
emptiness.web2tor.cf
version2.ilove26.cf
luckyhere.mashiro.tk
imtesting.shiina.ga
ggwp.emptiness.tk
Emptiness Sample MD5
f41464471a0ac9c165e4aeb55283934e
420bb6147ca091a22f8f5bbbb49d51f3
7b1943ff6c563ce1043963e2f017ad8d
53bb43411ecbad39b18b0662b53c07a0
1899667e48c64b113c0de54cf3bb63d5
Mirai.shiina CC
34.80.131.135
shiina.mashiro.tk
luckyhere.mashiro.tk
imtesting.shiina.ga
Mirai.shiina Sample MD5
77e7dd8982e7bb21d536264f0635d5cb
209a78969d88c667c32e550ce47b8ff9
0cf288e07e888cd7748b30fa4a67ca84
f6e9f3567684a0a7402ad97209b8525b