Http 81 Botnet: the Comparison against MIRAI and New Findings
Overview
In our previous blog, we introduced a new IoT botnet spreading over http 81. We will name it in this blog the http81 IoT botnet, while some anti-virus software name it Persirai, and some other name it after MIRAI.
In this blog, we will compare http81 against mirai at binary level:
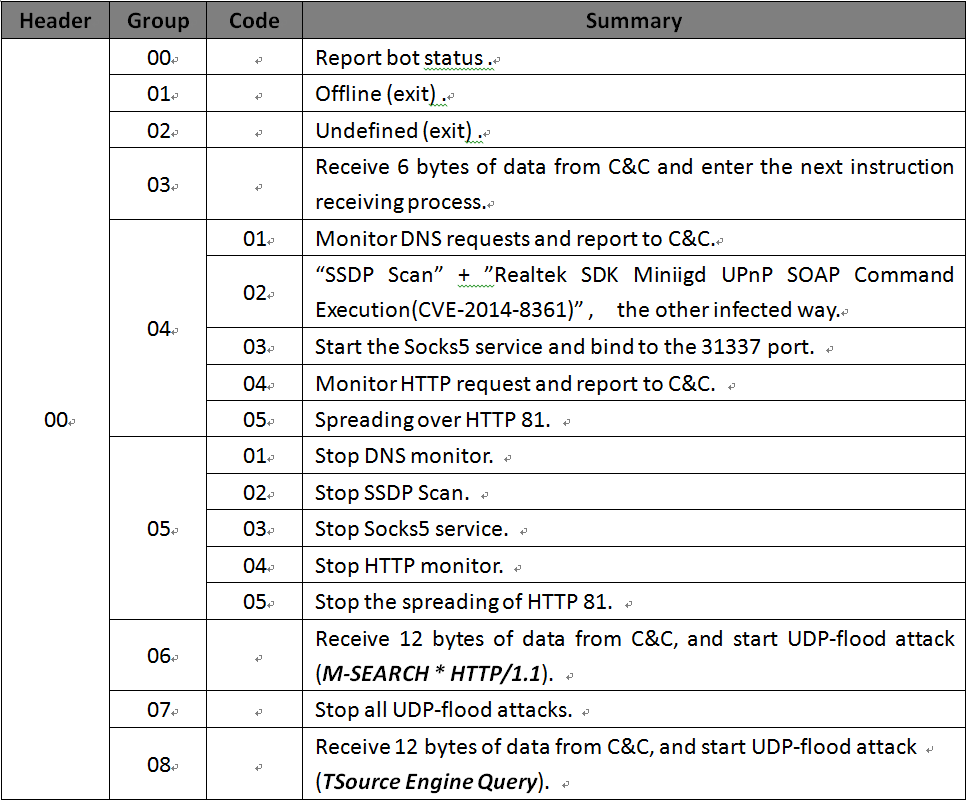
1. Similarities to Mirai 1.1 Same IP Blacklist in Scanning Module 1.2 Same Functions as a Fundamental Library 2. Differences against Mirai 2.1 C2 Presence in the Source Code 2.2 Infection method 2.3 C2 Communication Protocol 2.4 Attack vector
With the distinguish differences in infection, C2 communication and attacking vector, the http81 should be treated as a different botnet from mirai.
This blog also introduce several new findings:
- another inactive infection method on SSDP/UPnP
- the SSDP/UPnP infection payload is reused by
00 06UDP-Flood - the C2 domains are now silent by resolving to internal network address
****PS:*If not noted,MIRAI analysis will be based on the leaked source code from GitHub;the HTTP 81 botnet analysis will be based on the reverse engineering result of sample with a md5-hash 9584B6AEC418A2AF4EFAC24867A8C7EC .
Similarities to Mirai
Same IP Blacklist in Scanning Module
As we all know,mirai were spreading very fast under the support of SYN port detection. Nowadays this mechanisms is borrowed by several different botnets, including this http81.
Mirai introduced an IP blacklist code snippet when choosing target scanning IP address to avoid touching some specific CIDR(SOURCE: scanner.c). As shown in the following figure.
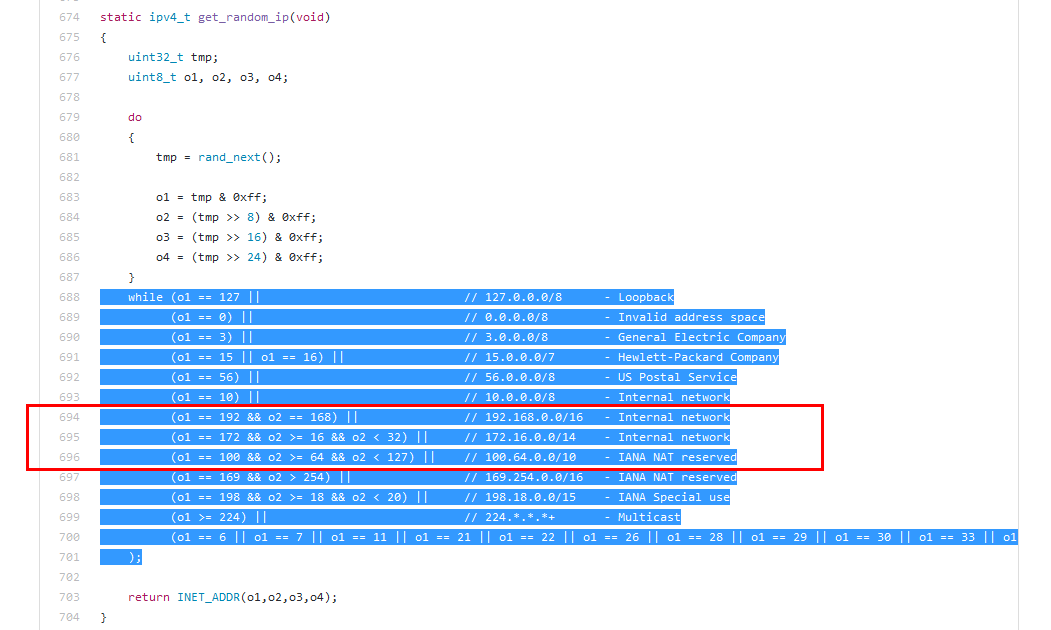
Exactly the same code snippet exists in http81 botnet in function sub_A7C4. Following figure shows the same code lines in the red boxes. In fact, the whole while cycle is the same.
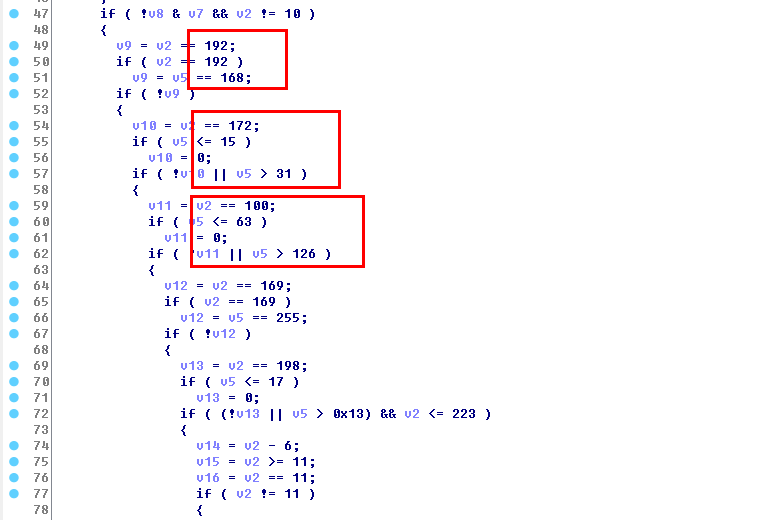
Same Functions as a Fundamental Library
When compared at assembly instruction level, it is clear that a small number of functions are highly consistent between two botnets.
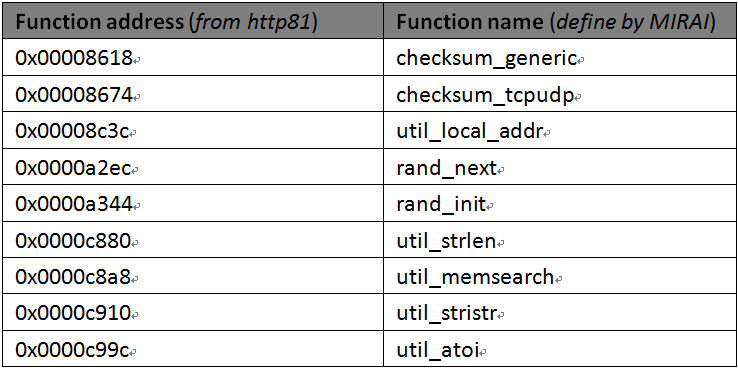
These listed functions looks very fundamental, as from the function name. For example, the function rand_next is called in the IP blacklist snippet mentioned above.
Differences against Mirai
C2 Presence in the Source Code
In the MIRAI source code, an Xor encryption algorithm is used to protect the original C2 domain name, to bury it into a ciphered text deep in the source code. Clues are showed in following snapshot, from the table_init function of the table.c file.
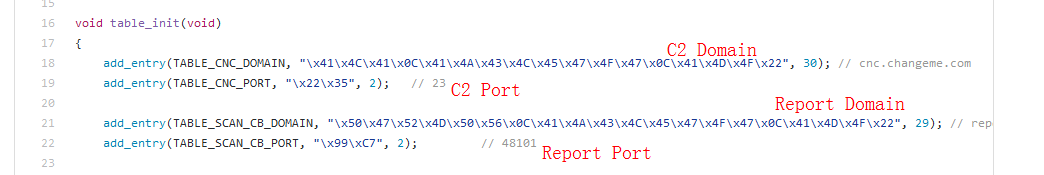
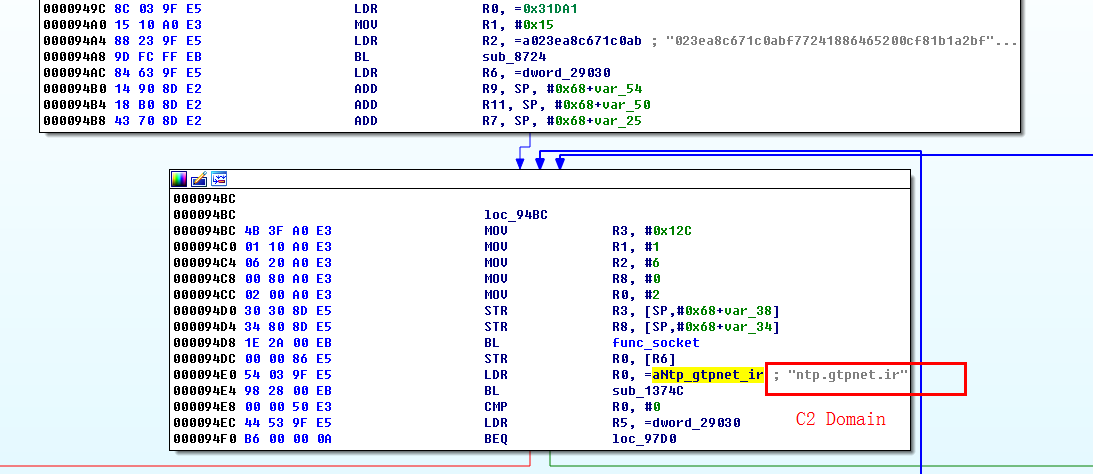
But in http81, the C2 is store in plain text. A bared C2 can be seen from the figure below.
Infection method
The source leaked mirai was spreading over telnet 23/2323. Some mirai variants works on different ports such as 7547/6789/3777, but no evidence of http 81 port exists. More details can be found in Mirai Scanner.
This http 81 port injection is a unique feature of the http 81 botnet, with more details listed in our previous blog.
C2 Communication Protocol
In the MIRAI source code, attack_parse function(Source: attack.c) records the details of its protocol.
http 81 botnet adopts a completely new protocol, listed in following table. In this list, 00 06 and 00 08 are code for UDP flood.
Attack vector
MIRAI owns 10 DDoS attack vectors including a unique GRE/VSE attacks, which listed in the attack.h file.
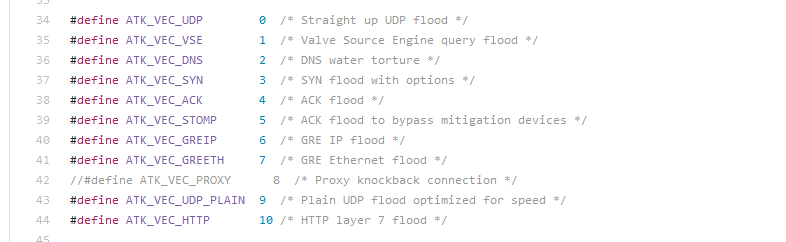
But http81 owns just two DDoS attack vectors. Both are UDP flood with protocol numbers 00 06 and 00 08, mentioned in above.
New Findings
Another Inactive Infection Method on SSDP/UPnP
Although http81 use a unique http 81 injection, there is another infection method with instruction code 00 04 02, which seems inactive.
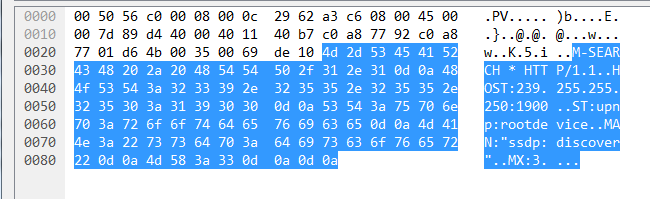
Once activated, large number of UDP requests will be send in a short time to randomized destination IP on port 1900, with following packet contents.
M-SEARCH * HTTP/1.1 HOST:239.255.255.250:1900 ST:upnp:rootdevice MAN:"ssdp:discover" MX:3
This is exactly the first request packet of the SSDP protocol (Function address: 0x0000A918). If one of them hits a SSDP device, the bot will enter the SSDP interactive process to get more device information, and try to use the EXPLOIT (CVE-2014-8361, "Realtek SDK Miniigd UPnP SOAP Command Execution" ) when the keyword (:52869/picsdesc.xml) appears(Function address: 0x0000A458).
Sometimes, when the bot can not directly exploit the target device on the WAN side, an function containing "AddPortMapping" will be tried (Function address: 0x0000AE20) to establish an port tunnel, through which another shot of exploit will be tried.
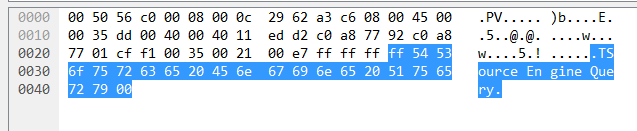
The SSDP/UPnP Infection Payload is Reused by 00 06 UDP-Flood
The http81 botnet owns two DDoS attack vector, 00 06 and 00 08. Payload of the former 00 06 is exactly the first request packet of SSDP protocol.
Payload of the later 00 08 is different.
The C2 Domains Are Now Silent by Resolving to Internal Network Address
ntp.gtpnet.ir/load.gtpnet.ir are now silent by resolving to internal network address since 2017-04-26 02:13:49(GMT+8), so the bot-master will not send command to the botnet at this moment. But it doesn't mean bot-master has lost control to the botnet.
- ntp.gtpnet.ir A 10.40.40.40
- load.gtpnet.ir A 10.50.50.50
Two different explanations we listed here:
- The manager found the botnet exposed and cut off the connection.
- The manager is sharpening the botnet, but interfered by the heavy load from the bots. So the manager temporary offline the domain for a easier development.
Review
We will treat http81 a new new family different from mirai.

